What is Placement in Money Laundering

- 01 What Does Placement Refer to in Money Laundering?
- 02 Purpose and Significance of the Placement Stage
- 03 Common Methods of Placement in Money Laundering
- 04 Money Laundering Placement Examples
- 05 Red flags which can signal placement stage of money laundering
- 06 The AML Compliance Role in Placement Countermeasures
- 07 Enhancing Your AML Strategy of Placement Risk
- 08 Frequently Asked Questions
Money laundering is not only a crime that disguises dirty money, it’s a catalyst that funds more serious crimes, funds criminal enterprises, slows economic growth, and erodes public trust in the financial system.
Money laundering begins the moment illicit cash tries to enter the financial system, known as placement. It is the first step in the three stages of money laundering, the other two being layering and integration. The placement stage of money laundering is both a criminal’s biggest risk and a compliance team’s best opportunity.
At this stage, funds are most vulnerable to detection when they’re first deposited, converted into monetary instruments, or mixed with legitimate earnings. Therefore, it is very important to stop dirty money at the door of the financial system before it obscures the trail through layering.
What Does Placement Refer to in Money Laundering?
Placement in money laundering is the very first stage of the process, wherein the criminals place the proceeds of crime into the controlled financial system. It essentially focuses on disconnecting the money from the illegal activity by physically or digitally introducing illicit proceeds into the financial system or retail economy. The purpose is to obscure the source and avoid notice by authorities by using techniques like informal value transfer, structuring, and use of mule accounts, etc.
The placement stage of money laundering is an important area that needs to be understood since most of the red flags are identified at this level. Any successful effort towards these preconditions is the future concealment, which is one of the critical areas of concern for regulators and compliance officers.
Purpose and Significance of the Placement Stage
The main purpose of placement money laundering is to move tainted money into the clean economy without raising suspicion. It poses great risks to financial institutions, which must detect and mitigate these attempts on a timely basis.
Criminals utilize the placement stage to safeguard their business operations and lines of income, where they know visibility at that level will be detrimental to the grand design of laundering.
Placement is of especially crucial significance by virtue of its susceptibility. This is because it involves face-to-face currency exchange, hence involving the suspicion of the supervisor. Effective identification here can prevent broader, more sophisticated methods of laundering from taking hold.
Common Methods of Placement in Money Laundering
Several major techniques characterize the placement stage of money laundering:
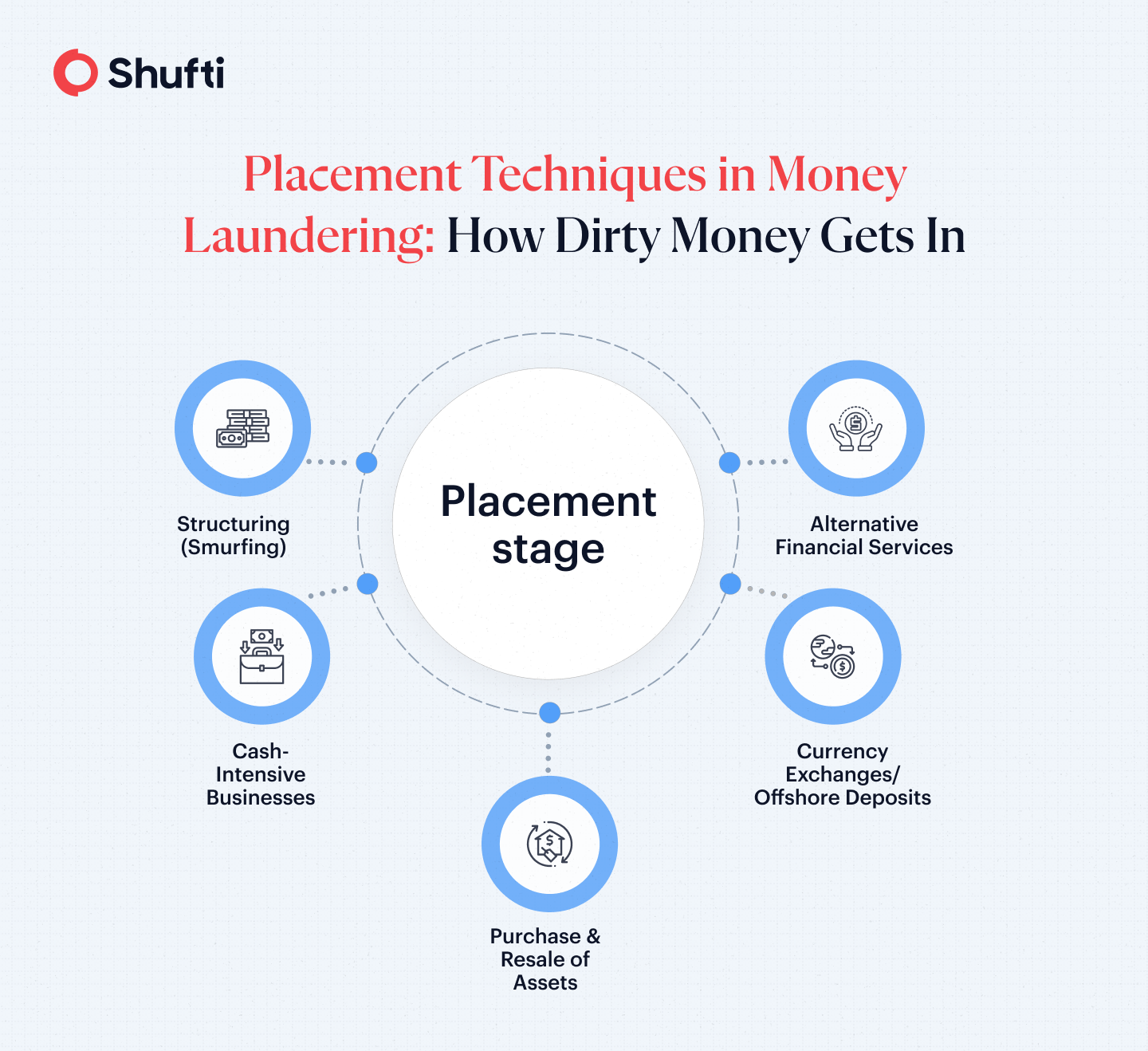
- Structuring (smurfing) deposits: Criminals divide large sums into smaller deposits, spaced out over time and across multiple accounts to evade regulatory reporting thresholds.
- Cash-intensive businesses: in cash intensive businesses like restaurants, casino, and nightclubs, it is hard to tell the difference between clean and dirty money since illegitimate funds are shown as legitimate cash sales.
- Buying and selling valuable properties: Valuable properties, including real estate properties, vehicles, jewelry, art works and precious metals, are purchased and then resold to legalize the gains of illegal operations.
- Currency exchanges and offshore deposits: Money is transferred to foreign currencies or even transferred to countries with less strict AML regulations, and in effect, put it outside the domestic regulatory framework.
- Monetary Instruments: The money can also be deposited through traveler’s checks, money orders, stored value cards, or by paying debts using cash provided by an illegal source.
The purpose of these techniques is to obscure the origins of the funds and bypass standard compliance procedures. This often requires financial institutions to employ refined transaction monitoring and risk assessment tools.
Money Laundering Placement Examples
Money laundering placement examples can be highly sophisticated and quite devastating to societies and economies. A recent real-world example is the Vancouver Model, which evolved in the Canadian province of British Columbia (B.C.), and which exhibits the diversity and sophistication of placement methods.
Case Study: The Vancouver Model
Cullen Commission report of 2019 estimated that an amount of $46.7 billion was laundered in 2018 in Canada, of which $7.4 billion was laundered in B.C. alone. Criminal groups of Vancouver controlled a multi-level placement activity through front businesses that included casinos, upscale real estate, and international movements of capital. The process typically started with large volumes of cash from drug trafficking and illegal operations, often delivered in duffel bags filled with small bills.
In order to avoid limitations on fund transfers out of China, Chinese citizens have cooperated with the organized crime networks in Vancouver. These syndicates would wire transfers in China and furnish their clients with the same sums of illegal money in Canada.
The money would be used to buy high-value casino chips, and the gambler would play with small stakes till he or she redeems the remaining casino chips with casino-issued cheques. These cheques were the clean money, which now manifests as gambling winnings.
The proceeds were commonly further “placed” by investing in Vancouver’s luxury real estate market, mostly by complex ownership structures designed to conceal identities.
Investigations showed these transactions drove up local property prices. They also made housing less affordable. A significant number of the city’s most expensive properties were bought using unclear methods.
The following are some of the typical tricks that have been employed in such transactions:
- A technique known as smurfing to evade detection is breaking deposits into several bank accounts using false names.
- Layering money by investing it in cash-heavy enterprises such as night clubs or restaurants to conceal the origin of the money.
- Transferring large sums of money across borders and putting them into countries where the anti-money-laundering regulations are weak.
It was not only the distortion of finances in the Vancouver Model. It empowered criminal organizations, contributed to drug issue, and opened loopholes in gambling and real estate policies. These are just some of the examples of the actual danger and the ingenious approaches in the initial phase of money laundering.
Red flags which can signal placement stage of money laundering
Detecting placement in AML relies on vigilance and examining a combination of behavioral, transactional, and documentation-related red flags:
- Multiple just below threshold cash deposits are inconsistent with the profile
- Rapid cash-in, then immediate transfers.
- Third-party deposits into new accounts; nexus to known high-risk MSBs.
- Cash buy-ins at casinos followed by minimal play and cheque redemption.
- Early cash deposits for high-value goods (vehicles/jewelry) with quick resale.
Banking institutions are forced to comply with sound monitoring systems and KYC (Know Your Customer) procedures. This will assist in the identification of such behaviors, record profiles, and examine transaction histories to come up with deviations in normal activity.
The AML Compliance Role in Placement Countermeasures
Fighting the placement phase of money laundering is based on the placement in AML compliance:
- Effective KYC practices: Background checks on clients, records, and financial documentation, including Statement of Wealth, may point towards attempts to launder illegal money.
- Analysis of transactions and tracking: With the availability of machine learning, real-time filtering, and AI, it is possible to detect the placement and smurfing patterns.
- Sector-based strategies: Special consideration should be given to vulnerable sectors such as banks, bullion dealers, cash-intensive based business, and operation of high-valued goods.
- Collaborative and risk-based strategy: Information sharing between the financial institutions and regulatory agencies, with frequent audit increases AML defenses on a global scale.
Early detection has become impossible without technology. It helps in automating data analysis and linking seemingly disparate transactions, a necessity given the complexity and creativity of criminal placement tactics.
Enhancing Your AML Strategy of Placement Risk
Among the most important things is to realize and overcome the obstacles of the placement money laundering in compliance leaders and financial institutions.
Key takeaways:
- Recognize the common methods and examples of placement and invest in technology-driven monitoring for improved detection.
- Enforce a powerful compliance culture, provide regular, consistent training to employees, and revise the processes and procedures to keep pace with the changing placement strategies.
- For organizations seeking powerful AML infrastructure, partnering with hybrid solutions that provide real-time detection, automated screening, and regulatory reporting is recommended.
How does Shufti support greater compliance without compromising your business growth?
Detection of money laundering at the layering stage requires that financial institutions have a robust risk assessment and customer identification program that will help them comply without hindering their growth. Shufti’s proprietary document verification tech and custom OCR solutions built from scratch ensure customized compliance workflows based on each business’s compliance needs.
Accurate risk assessment is the starting point for the RBA; therefore, a strong risk assessment means stronger compliance, efficient use of resources, and minimized compliance costs. With Shufti’s screening and identity verification solutions, you can ensure risk assessment is your competitive advantage, not an obstacle in your growth.
Frequently Asked Questions
What happens at the placement phase of money laundering?
The initial stage is to place illicit money into the legitimate financial system, and this is usually done by deposits, buying of assets, integration with cash-intensive business, or use of other financial sources.
Which are typical methods of placement?
Tactics used often are smurfing (structuring deposits), commingling cash-intensive business, buying assets, exchanging currencies, invoice fraud, stored value cards, and financial instruments.
What are the red flags of placement?
The indicators of key concern are the presence of a number of small deposits immediately below reporting thresholds, unusual client behaviors, inconsistent information, unusual transaction patterns, and enormous unexplained third-party funds.

 Explore Now
Explore Now













