Step-By-Step Guide to Ideal KYC Checks

Customer onboarding has evolved from a days-long process to mere seconds. A user takes a photo of their ID, completes a quick liveness check, and, if everything checks out, they’re onboarded almost instantly.
Behind that smooth experience is an entire layer of KYC checks working in the background, verifying identities, screening risks, and filtering out bad actors long before they can commit any fraudulent activity.
In 2025, with synthetic identities, deepfake-driven fraud, and evolving AML obligations, KYC isn’t a box-ticking exercise. It’s the infrastructure of trust, compliance, and consumer safety in every modern financial platform.
Below is a practical step by step by step guide for designing an ideal Know Your Customer process that allows enterprises to gain customer trust, maintain their professional integrity, and satisfy customers by making the procedure less intrusive and more effective.
The Backbone Behind Every Digital Onboarding Flow
Every onboarding journey, whether for a bank, lender, crypto platform, forex, or fintech, relies on one core engine: a structured, risk-aware KYC checks process.
It includes the following steps:
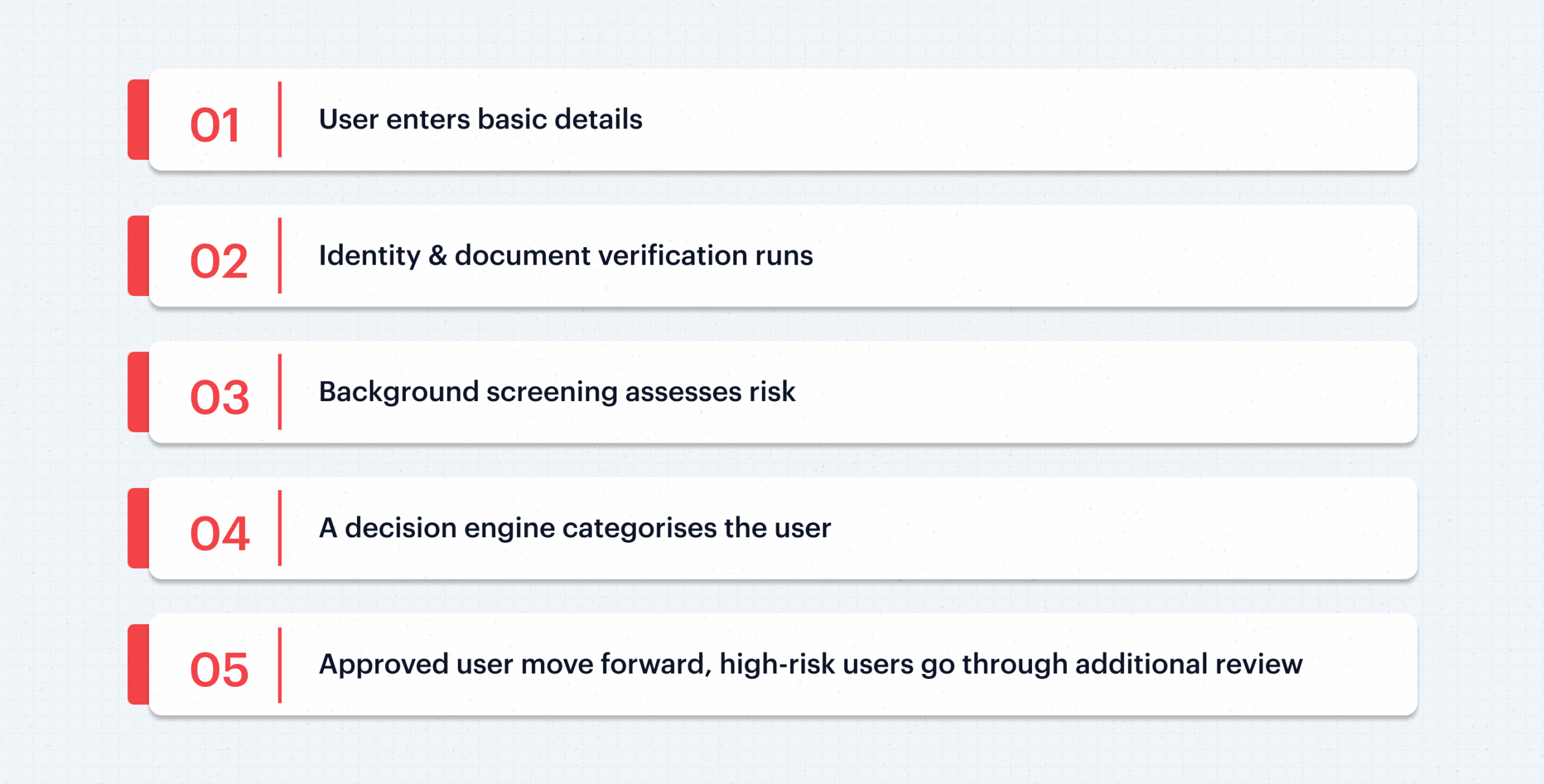
What looks like a simple step to the customer is actually a multi-layered KYC workflow. Ideal Know Your Customer checks balance three important areas: user experience, fraud prevention, and regulatory requirements. If these objectives are achieved with minimum friction for the user, the process is working smoothly. When they don’t, conversion drops, or worse, vulnerabilities open up.
The foundation of ideal Know Your Customer checks is speed, accuracy, and automation.
Step 1: Capture Customer Information
An effective KYC process begins with the extraction of accurate, structured, and comprehensive data. The accuracy of this step defines the smoothness of the remaining onboarding journey for the user.
For individuals, the optimal setup captures core identity information such as full name, date of birth, contact details, address, and a government-issued ID.
For businesses, however, onboarding includes legal registration details, business nature, and identification of directors and ultimate beneficial owners.
What makes this step effective is not just the data itself, but how it’s captured without any error:
- Fields should be clear and purposeful,
- Formatting should be enforced to avoid inconsistencies, and
- Tools like OCR should extract information (even those in non-Latin languages) directly from IDs to prevent clerical mistakes in data input.
When data collection is clean, the entire KYC pipeline becomes faster, more accurate, and significantly less costly.
Step 2: Verify Identity & Documents
After the collection of data, the next requirement of an ideal KYC process is effective identity and document verification.
This process not only checks if the Identity document is real or fake but also includes a multi-layered verification process to detect tampering, validate authenticity, and confirm the real user is present at the other side of the screen.
An ideal identity verification step includes:
- Document authentication to verify if it’s forged, altered, or counterfeit, and validate MRZ codes
- OCR extraction for a thorough comparative analysis between the entered data and the one in the ID document
- Biometric verification (that includes face matching and liveness detection) to ensure the document actually belongs to the user being onboarded.
- Device and behavioural intelligence to detect anomalies like unusual IP locations or repeated onboarding attempts from the same device
This is the level of rigour seen in ideal KYC checks, and it’s increasingly expected to be followed across enterprises in the digital-first world.
Step 3: AML Screening
A real identity shouldn’t be confused with a safe identity. Once a person’s identity is established, the next step is to assign it an appropriate risk category. That’s why an ideal KYC procedure includes comprehensive background checks of the user that reveal risks that are not detectable at the document verification stage.
Effective AML Screening includes:
- Screening against international sanctions lists (imposed by OFAC, UN, etc.)
- Identifying politically exposed persons (PEPs)
- Checking adverse media for indicators of fraud, corruption, or financial misconduct
- Reviewing law enforcement and regulatory watchlists that highlight individuals linked to previous investigations
These checks should not only be automatic and fast but also need to be continuously updated. Regulatory lists change frequently as new entities are sanctioned, delisted, investigated, or added based on geopolitical or enforcement developments.
Institutions relying on outdated AML screening data risk overlooking high-risk individuals or incorrectly flagging low-risk customers. Real-time updates, therefore, become essential for decision accuracy.
In high-risk industries, AML screening forms the core defense layer for risk prevention, in order to assure the person is not only who they claim to be, but also someone a platform can safely serve.
Step 4: Apply Risk-Based Decisions
Users being onboarded do not pose the same level of risk. That’s why enterprise-grade compliance frameworks rely on risk-based KYC compliance checks to onboard low-risk users quickly and apply vigorous checks only when it’s essential to keep the onboarding workflow smooth.
In a best-practice setup:
- Low-risk users should pass through quickly with minimal friction.
- Medium-risk users should face secondary steps to clarify inconsistencies.
- High-risk users, such as PEPs or individuals from high-risk jurisdictions, should undergo Enhanced Due Diligence (EDD), requiring deeper checks and identification.
Ideally, these decisions are made through automated rules and risk scoring models, which ensure minimum manual workload and consistent outcomes.
This is what ideal KYC compliance checks look like: smart, flexible, and proportionate to the customer’s risk level. Such a KYC check process enables growth by a frictionless journey for maximum users.
Step 5: Ongoing Monitoring
A well-designed KYC process doesn’t stop when the user is safely onboarded. In fact, the ideal KYC compliance checks continue long after onboarding, as customer behaviour may change over time. Transaction patterns can shift, risk levels can change over time, or new information may surface.
This ongoing component should:
- monitor transactions and user activity for suspicious patterns,
- update risk scores with the availability of new information,
- trigger re-verification when found necessary, and
- keep the organisation aligned with changing regulatory obligations.
This is especially important as fraudsters increasingly behave “normally” during signup and only reveal risk indicators later. Continuous monitoring is what makes an ideal KYC system proactive, not reactive.
Why Strong KYC Checks Pay Off
When KYC checks are done right, the impact shows up everywhere. Fraud losses drop, regulatory compliance becomes easier, and onboarding flows feel smoother instead of being clogged with manual reviews.
Users are more willing to trust a platform that has a clear risk-based policy, which translates into higher user conversions and trust worth long-term relationships. At the same time, efficient KYC keeps operational costs under control and strengthens an institution’s overall AML posture, giving the confidence to enter new markets and launch new products.
Fintech adoption grows when trust is scalable, and that trust starts with KYC checks executed properly.
Best Practices for Frictionless KYC
Designing the ideal KYC experience means striking the right balance between robust security and a smooth user journey. A top-tier setup invests in automation to remove repetitive manual reviews, uses dynamic KYC flows so that friction matches the customer’s risk level, and intelligently integrates signals from documents, biometrics, device data, and behavioural patterns to reach more confident decisions.
Manual reviews still have a place, but in an ideal KYC model, they’re treated as a learning layer: every case helps refine rules and models so the volume of edge cases to be checked manually decreases over time. The system needs to be flexible and adapt quickly as new fraud techniques emerge, while still feeling simple and intuitive for reliable users from the first screen to the final approval. Ideal KYC isn’t about making onboarding intrusive; it’s about making it smarter.
How Shufti Empowers Businesses with Adaptable KYC Solutions
Enterprises across financial services, fintech, lending, and digital commerce continue to face rising pressure to verify identities accurately while keeping onboarding journeys efficient. These challenges require a verification model that adapts to customer risk, maintains regulatory alignment, and reduces exposure to evolving identity-based threats.
Shufti’s risk-based verification engine provides automated identity checks, real-time AML screening, biometric security, and configurable workflows that help institutions customize their KYC programs without compromising customer experience.
Request a demo to explore how Shufti can support your onboarding and compliance goals.

 Explore Now
Explore Now