6 Industry Experts Share Their Thoughts on NFC ID Verification

Thanks to the growth of contactless transaction systems like Apple Pay, NFC is now a mainstream technology. The majority of smartphone users must have come across the term “NFC” since mobiles nowadays are NFC-enabled. Did you know that there are more than two million NFC-enabled devices in use today? However, the use of this technology is still not known to many.
Also known as Near Field Communication technology, NFC is a standards-based wireless system that makes touchless payments convenient for individuals. It enables short-range communications between NFC-enabled devices. Nowadays, it is also used for identity verification purposes
Shufti has introduced NFC Verification to make the identity verification process more effortless and robust. Take a look at how it works followed by some expert insights on it.
What is NFC Verification?
Why should we (the IDV industry experts) stay behind when everybody else is using near field communication? NFC technology is now widespread in the identity verification market and the system verifies information embedded in chip-based ID documents.

How Does Shufti NFC Verification Work?
Shufti’s NFC Verification works in the following steps:
- The end-user first uploads an NFC-enabled ID document (this could be an NFC-enabled ID card/passport/driving license)
- Now, the end-user taps the document to the phone
- Data from the NFC chip in the document is now cross-matched against the information printed on the ID document
- Verification results are delivered
NFC Verification – What the Industry Experts Have To Say
Government-issued ID documents now have an NFC chip embedded that contains all the personally identifiable information (PII) that is digitally signed and encrypted. NFC-based document verification entails higher levels of security and authenticity along with many other benefits. We conducted a short survey about NFC and its role in the identity verification system. Take a look at what the experts have to say about NFC-based identity verification.
Higher Security
The level of security significantly increases with near field communication verification. How? The chip in the identity document has all the information that is needed for IDV. Since it cannot be tampered with, businesses can securely onboard legitimate customers though validating all the data in the NFC chip, hence minimizing false positives.
Here’s what Cybersecurity Expert at VPNoverview, Veronica Miller, has to say:

Effective KYC/AML Compliance
After the skyrocketing numbers in criminal activities last year, the regulatory authorities have increased the rigidity of KYC and AML laws. The changing KYC/AML landscape in 2021 requires technologically advanced identity verification mechanisms. So, NFC identity verification is the best way to effectively comply with the evolving regulations.
The Know Your Customer (KYC) and Anti Money Laundering (AML) processes are mandatory for the corporate world. However, they consume a lot of time, especially when the process is manually completed. Moreover, the tedious process increases customer drop-off rate which none of the businesses enjoy.
“The importance of high-quality KYC processes cannot be overlooked. Using NFC-based identity document verification, you can reduce fraud by detecting cloning and establishing the required level of trustworthiness at a distance, at a low cost, and with no data mistakes. NFC is really helpful for all the businesses that have transformed their business digitally.”
-Veronica Miller, Cybersecurity Expert at VPNoverview
KYC and AML processes can be more effective if the NFC-enabled ID verification approach is followed. With Shufti NFC Verification, the chances of fraudster onboarding diminish making it easier for companies to comply with the regulations.
Suggested: A Comprehensive Guide to AML Compliance [2020]
Enhancing Operational Efficiency
The co-founder of CocoSign, Caroline Lee finds NFC verification a great way of increasing the efficiency of the customer onboarding process.

Customers of the digital world do not like to wait for more than a minute, so operational efficiency is crucial. NFC speeds up transactions and similarly, NFC identity verification can readily validate all the customers which not only boosts the efficiency of the process but also increases the customer acquisition rate.
No Integration Required
Apart from all the aforementioned perks of identity verification using near-field communication, the one to ponder is that it does not need any integration. All it takes is an NFC-enabled smartphone that can fetch information through the NFC SDK.
“Customers benefit from NFC-based ID verification in several ways. However, the major overarching benefit is the fact that services can be tailored to meet the customer’s specific needs. This will deepen relations between consumer and the business and increase customer satisfaction rates.”
-Ben Laaerberg, Founder of MyNextGenerator.com
Emerging Trend of NFC Technology in Various Industries
Many industries have stepped forward in employing NFC technology. Here are some of the sectors that can avail all the benefits of NFC Verification.
Travel Industry
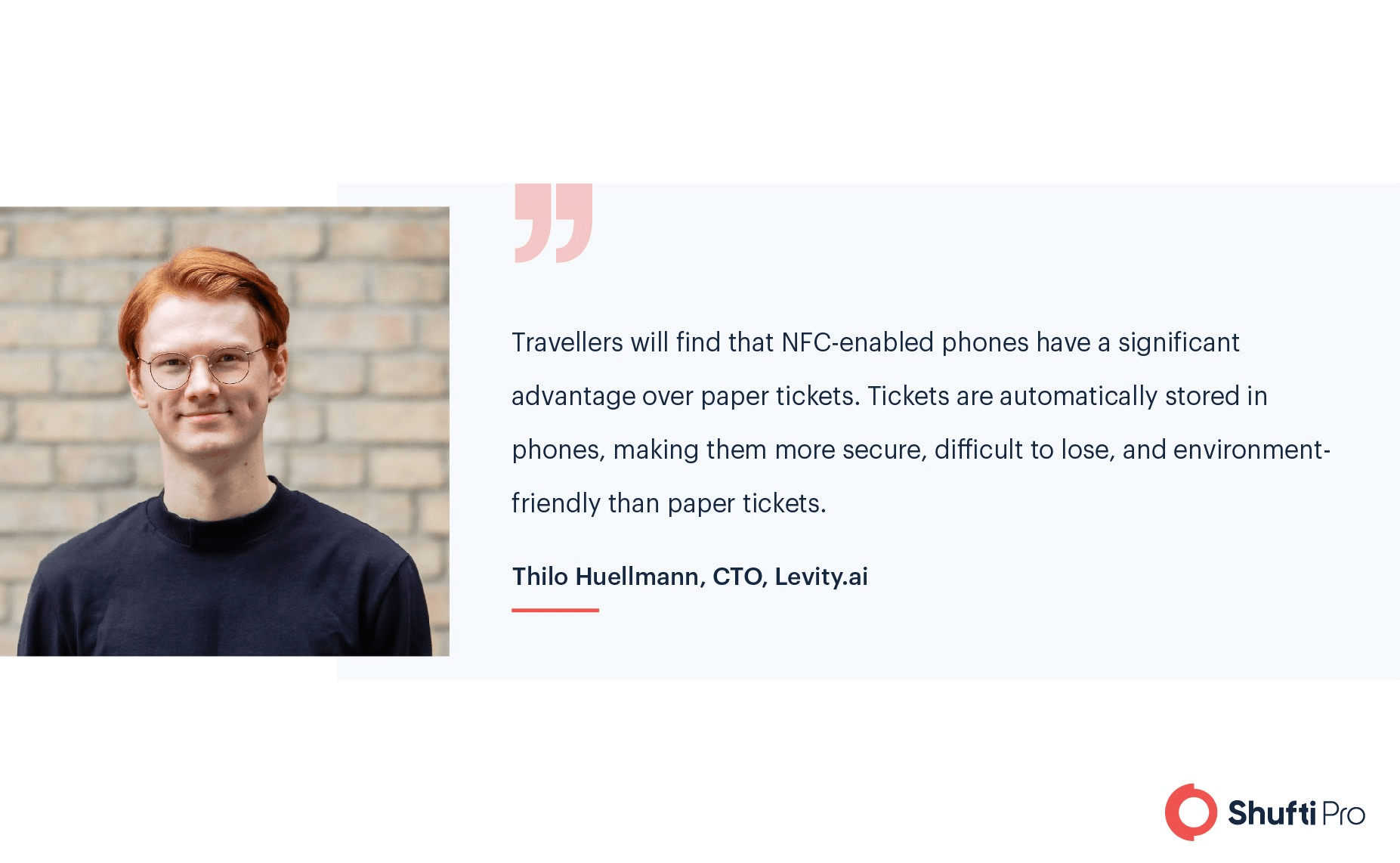
Onboarding passengers is already a difficult job these days thanks to the COVID test verification rule across the world. With a comprehensive and cumbersome identity verification process, travellers will only face challenges amid these turbulent times.
According to Thilo Huellmann, CTO of Levity.ai
Finance Sector
Tim Clarke, the Director of Sales and Marketing, SEOBlog.com says,

The banking and finance sector has been a target of fraudsters since forever but with an NFC verification, all financial institutions can prevent fraudsters from messing with the business.
In a Nutshell…
Identity verification should be a seamless process and this is what Shufti has considered while introducing NFC technology for identity verification. NFC Verification has the tendency to validate identity documents through NFC chips in seconds. Moreover, we ensure the highest possible accuracy rate.
NFC technology has been in use for making transactions frictionless and now, it has entered the identity verification market to make customer onboarding seamless too. Fraudsters cannot tamper with the chip in the NFC-enabled identity documents. Therefore, an NFC-based identity verification system can help all businesses.
You can find out more about NFC Verification from our experts. Talk to them today and save your business from imposters.

 Explore Now
Explore Now













