KYC Integration Strategies for Smooth and Regulatory-Compliant Onboarding

- 01 What Is KYC Integration and Why Does It Matter?
- 02 KYC Integration Architecture and Deployment Models for Businesses
- 03 The Control Layer: Fusing Identity Verification (IDV) and AML
- 04 Compliance Orchestration: The Brain of the Integration
- 05 Operationalizing KYC Integration From Workflow Design to Live Operational Readiness
- 06 Build a Scalable and Regulator-Ready KYC Strategy With Shufti
KYC integration has developed from a procedural point of validation to a key structural element in digital onboarding systems. Organisations are now faced with an increasing number of regulatory requirements, including the FATF recommendations (as amended October 2025) and the EU Anti-Money Laundering Directives. These frameworks emphasize the importance of embedding compliance into operational processes.
The shift to Perpetual KYC is an indication of a need for constant monitoring. This allows organizations to identify new risks, refresh risk profiles where necessary, and maintain proper records during the customer relationship.
Different KYC integration models suit different business types depending on regulatory exposure, technical maturity, data residency obligations, and risk tolerance. The following sections outline how each model aligns with specific organizational needs.
What Is KYC Integration and Why Does It Matter?
KYC integration means Know Your Customer is embedded into onboarding systems and customer lifecycle processes instead of being handled manually or in disconnected tools.
In comparison to siloed solutions, integrated KYC systems combine identity data gathering, risk score, and automated decisioning, which makes verification accurate and auditable.
Identity data capture in a structured format, real-time assessment of risk, and compliance logging that create records that can be presented to the regulator are all core elements. Perpetual KYC is also supported by modern frameworks, which allow tracking the customer risk profile and adjusting it dynamically.
When these processes are embedded into operational systems, organizations can respond proactively to emerging threats. This approach also maintains steady regulatory compliance and fosters trust throughout onboarding, account management, and beyond.
KYC Integration Architecture and Deployment Models for Businesses
KYC architecture reflects technical maturity, regulatory exposure, and risk tolerance, shaping data flows and controls. Organizations must ensure compliance, data residency, scalability, infrastructure ownership, and continuous monitoring rather than one-time checks.
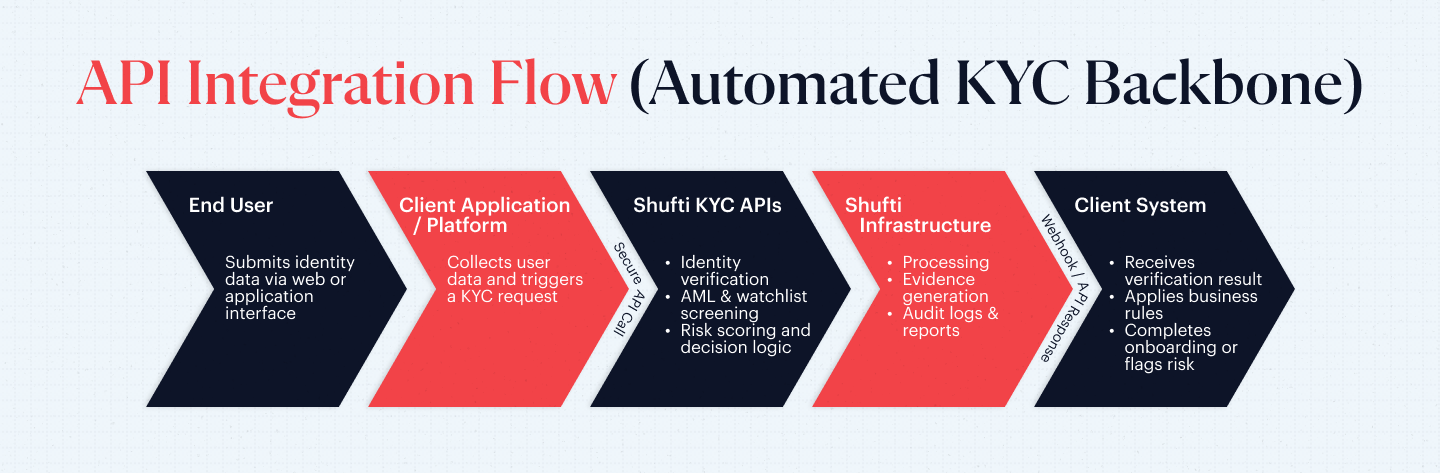
API Integration (Backbone for Automated KYC)
Automated KYC of proprietary systems and third-party platforms is based on API-based integration. KYC API Integration coordinates identity validation, AML screening, and decision logic using the same workflow. Real-time functionalities, including webhooks, modular endpoints, structured reporting, and audit-grade evidence, enable compliance oversight effortlessly without the need for manual intervention. Secure transmission and retention under provider control lowers the internal burdens of operation. This model has a quick deployment, elasticity, and lower infrastructure investment. It fits well with fintechs, marketplaces, crypto platforms, and development-based organizations.
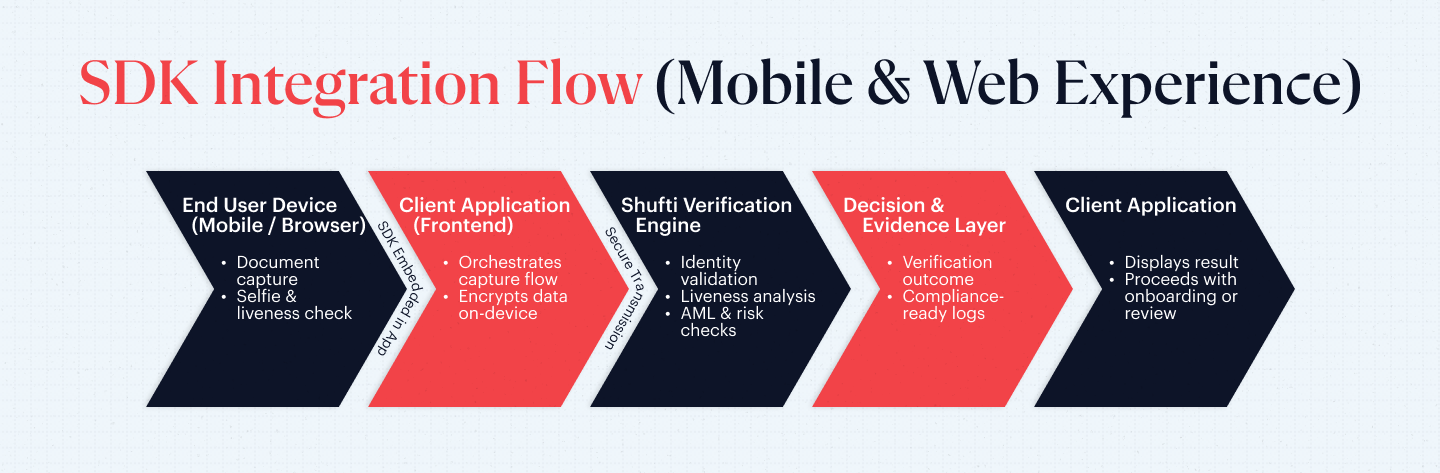
SDK Integration (Mobile & Web)
SDK integration embeds verification directly into mobile applications and browser-based onboarding flows. Capturing of documents, selfies, and liveness signals on the device is paired with validating and risk assessing on the server side. In this way, it enhances the completion rates, provides uniformity in the cross-device user experiences, and simplifies maintenance at the front-end. It is commonly adopted by mobile-first services, digital wallets, gaming platforms, and applications that face consumers.
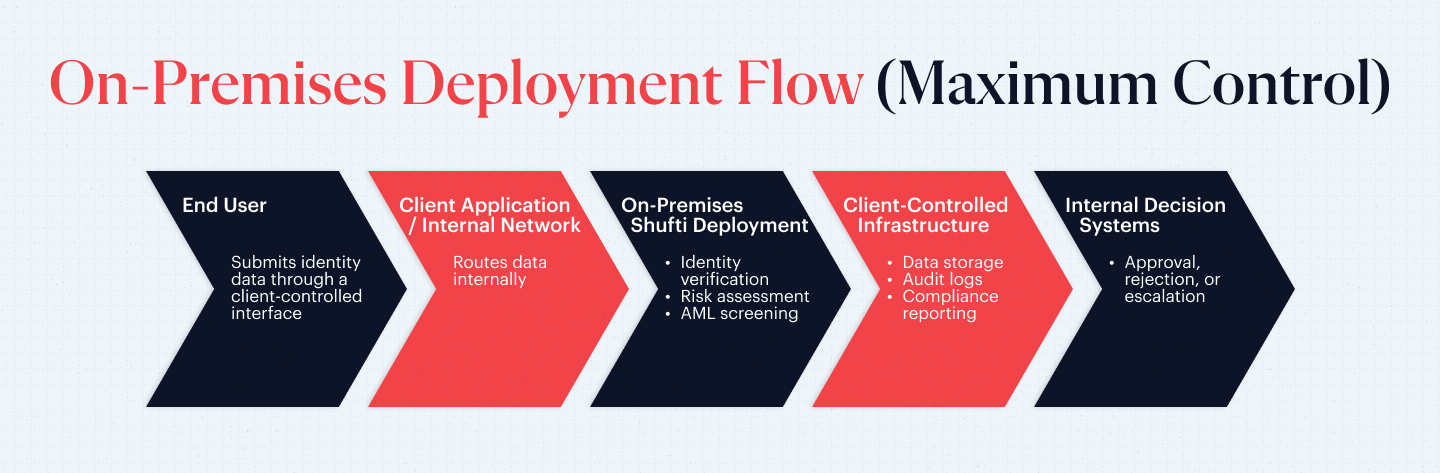
On-Premises Deployment
On-premises deployments provide organizations with full control over infrastructure and data, with no information transmitted externally. This model is commonly adopted by banks, government agencies, and operators of critical infrastructure, particularly where strict data localization is required. Examples include India’s Digital Personal Data Protection Act (DPDP Act), 2023, with DPDP Rules notified in 2025, and Saudi Arabia’s Personal Data Protection Law (PDPL), issued in September 2023 and enforced from September 2024. While on-premises deployments typically involve higher costs and longer implementation timelines, they offer maximum data sovereignty, reduced cross-border regulatory risk, and strong audit readiness.
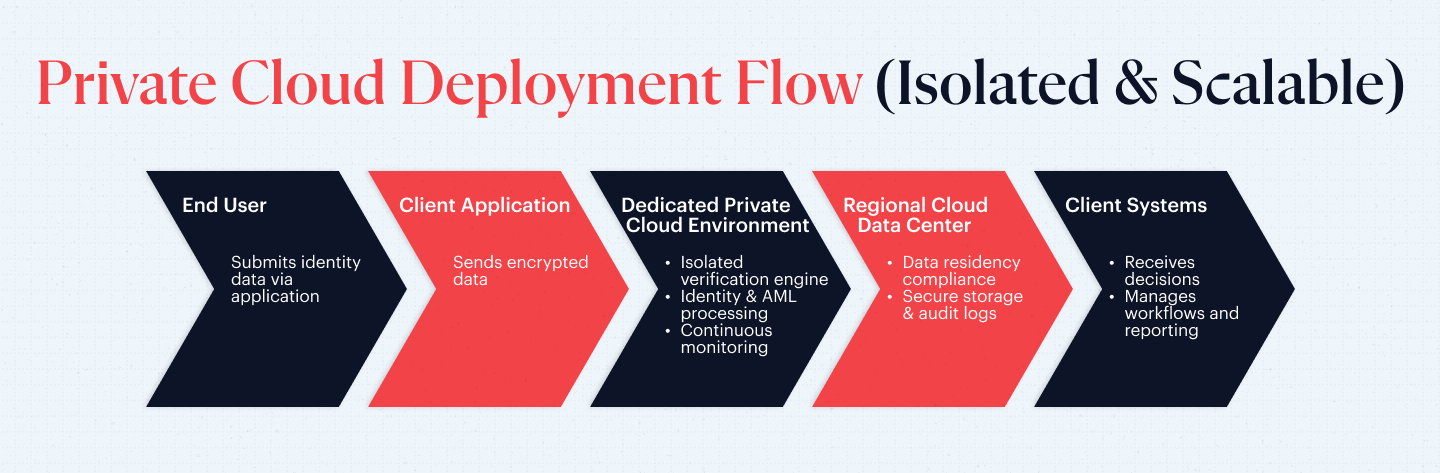
Private Cloud Deployment
Private cloud deployments run in dedicated and isolated environments to offer scalability. It also offers continuous monitoring of KYC, as well as robust data management, which can be remotely accessed. Data sovereignty or adherence to local laws can be maintained by companies through regional data centers, such as the Frankfurt data center, which supports the GDPR law. This way, companies are saved from legal issues regarding international transactions without compromising efficiency. Jurisdictional control is achieved without having to establish an entire infrastructure system.
Choosing the Right KYC Integration Model by Business Type
Selecting the appropriate KYC integration model depends on regulatory exposure, technical maturity, and data governance needs:
- Fintechs and startups: API or SDK integrations for rapid deployment and scalability
- Consumer-facing platforms: SDK integrations to embed verification into digital user journeys
- Banks and government institutions: On-premises deployments to meet strict data sovereignty and audit requirements
- Highly regulated enterprises: Private cloud models to balance jurisdictional control with operational scalability
This structure makes the suitability of each model immediately clear.
The Control Layer: Fusing Identity Verification (IDV) and AML
The control layer represents the operational core where identity verification and AML function as a single, automated decision engine rather than disconnected compliance tasks.
Identity verification offers the fundamental assurance needed by downstream controls, as the AML checks are done on known, identifiable persons. IDV layer usually integrates document verification through the government, biometric matching and liveness detection, and checks of authoritative databases/registries to prove identity confidence.
After identity verification, AML controls such as watchlists, sanctions, adverse media, and PEP screening are also implemented within the same workflow with tuned escalation limits.
The joint orchestration of these processes ensures consistent risk assessment, reduces reliance on manual reviews, and accelerates decision-making without compromising control integrity.
Non-documentary signal analysis enhances fraud protection by combining device fingerprinting, behavior biometrics, and networking intelligence. These signals enable the detection of advanced attacks like face swapping and camera injection, even before triggering the document authenticity check. Solutions that only rely on document authenticity are highly likely to miss these advanced attacks.
From compliance, a coherent and timely evidence produced by just a single layer of control enhances the defense of audit since it generates consistent evidence of identity and financial crime checks. Operationally, it enables compliance teams to pay attention to exceptions and high-risk cases, whereas low-risk customers face minimum friction.
Compliance Orchestration: The Brain of the Integration
APIs and SDKs relocate information, whereas compliance choices are coordinated using orchestration. The current KYC integration has moved from strict, hard-coded flows to no-code orchestration layers that enable compliance team control over logic, sequencing, and escalation independent of engineering assistance.
In the case of 2026, orchestration facilitates jurisdiction-specific regulations, waterfalling based on risk, and fast regulation changes. Low-cost checks can run first, with higher-friction controls triggered only when risk signals justify escalation.
Thresholds and modules may be changed in real time when the requirements change. Orchestration also enhances resilience by rerouting verifications when a provider goes offline, which then maintains operational continuity and audit defensibility.
Operationalizing KYC Integration From Workflow Design to Live Operational Readiness
KYC integration only delivers regulatory and business value when it is embedded end-to-end. It also aligns customer experience, backend controls, and operational readiness from the first interaction to ongoing monitoring.
User Journey (Customer-Facing Workflow)
- Identity submission at onboarding: This begins when the customer enters personal information, government-issued ID cards, and biometric data through a digital interface.
- Immediate verification feedback: Automating these checks produces immediate results on the status of approval, conditional review, or risk flagging to avoid uncertainty or any delay in onboarding.
- Risk-based access decisions: Access, account opening, transaction amounts, and service authorizations are granted instantly based on the defined risk scores and compliance.
- Ongoing verification touchpoints: Further verification or document update notices may spring up later in connection with ongoing monitoring requirements in relation to pKYC.
System Journey (Backend and Operational Workflow)
- Regulatory and risk definition: These are established by the compliance team before any technical implementation to define regulatory requirements in a particular jurisdiction or risk thresholds to be exceeded before escalation can occur.
- Workflow configuration and orchestration: No code layers handle validation, exception management, and dynamic risk/territory adaptation based on the user risk profile and jurisdiction in a real-time fashion in a way that retains human oversight.
- Deployment model integration: The selected architecture, API, SDK, on-premises solution, or Private Cloud is integrated with core business systems, as well as consumer-facing communication channels.
- Automation, evidence generation, and explainability: Identity checks, AML screening results, and decision outcomes are automatically recorded to create audit-ready evidence. The Explainable AI (XAI) framework ensures a transparent and traceable decision logic for every approval or rejection, supporting regulatory expectations under the EU AI Act (applicable from 2026), EBA Guidelines on ML/TF risk management, and Financial Action Task Force (FATF) requirements for explainability and auditability in automated controls.
- Continuous monitoring and optimization: The risk models for data and alerting rules applied in pKYC are evaluated periodically to ensure the improvement of adaptive pKYC.
Industry-Specific Implementation Examples
- Banking and Fintech: The account opening process is simplified to include sanction screenings, setting transaction limits, and providing ready-for-audit audit trails.
- Crypto and Virtual Asset Service Providers: The access to the wallets and the transactions permitted on the same be tied to the identification and risk.
- Marketplaces and Platforms: Verification systems for both buyers and sellers that ensure a balance between building trusted communities and driving conversion maximization and regulatory compliance.
Build a Scalable and Regulator-Ready KYC Strategy With Shufti
KYC Policies need a flexible approach based on tightening regulatory requirements and complex patterns of fraud.
Scalability is all about choosing an integration model that supports continuous monitoring, jurisdictional controls, and audit-ready evidence without operational strain.
Shufti enables organizations to embed identity verification and AML controls directly into digital workflows through flexible deployment options designed for regulated growth.
The automation framework it offers enables real-time decision-making, continuous risk evaluation, and document-level compliance maintenance as per KYC standards. As the technologies of AI-driven verification and monitoring develop, the combined platform solutions will set the tone for how the respective compliance team can maintain control while not impeding the execution of the business.
Request a demo to assess how Shufti supports compliant expansion.

 Explore Now
Explore Now













