KYC Verification – The Significance of Identity Verification in the Telecom Industry

Increasing smartphone usage throughout the world has accounted for large amounts of data being shared through digital means. Customers are required to fill in their personal information through online banking apps and also need their phone numbers to complete everyday tasks like ordering food.
Meanwhile, the telecom industry continues to face concerns due to fraudulent activities like SIM swap fraud and data theft, both of which arise due to the lack of identity verification. Even though there have been developments in the form of remote operations, the industry is still not free of identity fraud and financial crime.
Frauds Targeting the Telecom Industry
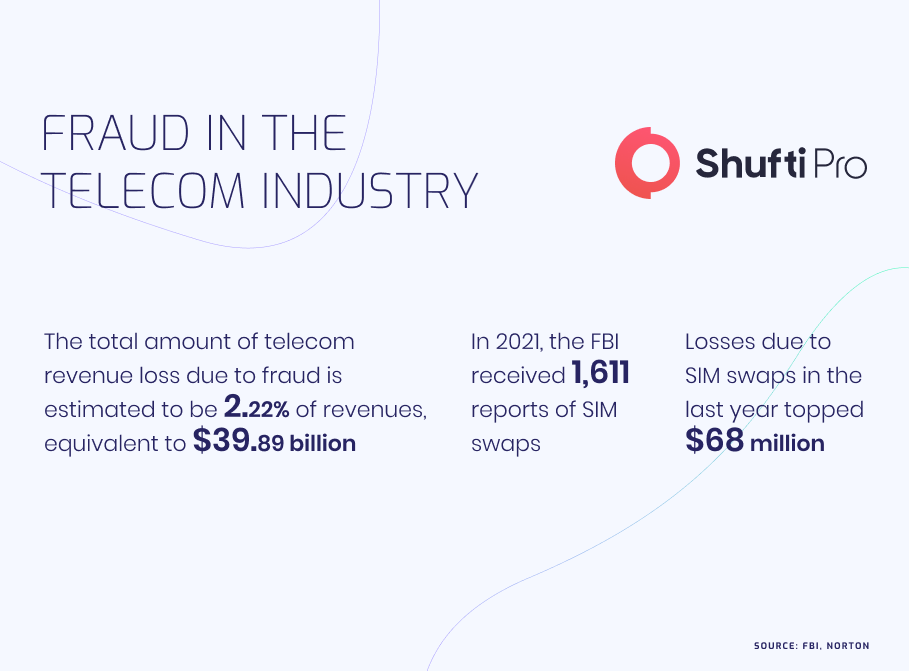
Mobile devices that are used for making online transactions and communicating sensitive information are vulnerable to fraudulent activities. Even the smallest of loopholes in a mobile network can enable fraudsters to use smartphones for identity fraud, payment scams, and account takeover. According to the Communications Fraud Control Association (CFCA), a telecom company called Telefonica Group with a $49.2 billion annual revenue in 2020 lost $915 million in revenue to fraudsters and criminals.
Fraudulent methods like SIM Farms are now being adopted by scammers to capitalize on the free services in the telecom industry. Using this method, fraudsters take payments and send SMS messages to thousands of random recipients to try and obtain personal information. If successful, they use the personal information for SIM swaps, which itself is a kind of identity theft targeting a mobile phone to get access to social media accounts, bank accounts, and even crypto wallets by getting their hands on OTPs (one-time passwords).
One of the major names in the telecom industry, T-Mobile, was recently targeted by an extortion gang Lapsus$ with SIM swapping attacks and code theft. SIM swapping fraud isn’t the end of the story, as phishing SMS techniques are also seen targeting telecommunication companies here and there. The most recent example came in the form of large-scale SMS messages that promoted fake financial aid programs to Ukraine. Phishing scams even prevailed during the COVID-19 period when fake vaccination programs were used to try and gain access to payment details.
These kinds of cases make it more and more difficult for the authorities to regulate the telecommunications industry. While SIM swapping remains an easy task for fraudsters, it has negative effects on both telcos and their customers. In the absence of regulatory measures that require robust identity verification measures, the industry will see increasing fraud rates in the years to come. Regulations for the telecommunication sector should include the requirement for providing proof of identity while purchasing a SIM.
Identifying and Eliminating Frauds
SIM swapping is made possible when a customer’s personal information is transferred to the SIM of an online scammer using techniques like hacking. This kind of scam not only makes the customers’ personal information vulnerable to misuse but also brings the risk of hackers gaining access to other related information that is linked to their SIM cards. This information may include e-mail credentials and banking details. Telecommunication companies must adopt a risk-based approach to identify and eliminate such fraudulent activities.
After the telecom industry gave its customers zero rate calls, it became clear that the sector needed and used the best available preventive measures. There has been a 2500% rise in calls and SMS messages to Ukraine since the Russian invasion earlier this year. As of now, telecom companies must do even more and make efforts to detect fraud while ensuring a fair service usage policy. There must be systems in place to monitor customers’ usage of telecom services, as well as the monitoring of networks and other data sources involved when there are activities deviating from standard procedures. In this way, telecom companies can detect and report suspicious activities.
There are now robust solutions available in the market for telecom service providers to keep an eye on suspicious activities and identify SIM swap frauds through devices that show unusual usage patterns. Telecom companies that monitor the red flags in mobile service usage are able to successfully combat fraudulent activities. This is done by detecting unusual activities in volumes of traffic coming from a specific location through mobile devices that send large numbers of SMS containing a link. Suspicious activities can also be detected through IMEIs that show relatively higher data consumption compared to other devices in a short span of time.
How the Telecom Industry Can be Secured
Know Your Customer (KYC) is the process of verifying customers’ identities that is implemented by banks and any other financial institution dealing with monetary operations. It is aimed at preventing the risks of identity fraud and keeping an eye on both customers and telecom service providers. In several areas, KYC measures are encouraged by governments as part of AML (Anti-Money Laundering) regulations and as part of measures to secure mobile operators from unwantedly becoming the source of money laundering and terrorist financing. Even in areas where KYC measures are not encouraged by governments, telecom operators must incorporate robust identity verification measures to prevent fraudulent entities from accessing their system.
Online identity verification service providers like Shufti utilize technologies like biometric facial recognition along with thousands of AI algorithms to authenticate the identities of telecom companies’ customers. KYC compliance ensures that companies run background checks on their customers to identify whether they are linked to PEPs (Politically exposed persons) as well as checking for their presence in global sanctions lists.
How Shufti Can Help
The telecom sector and communication service providers are being challenged by cybercriminals and finding it hard to curb reverse-engineered scams. Due to this reason, online accounts and financial wallets are more likely to get breached. Thus, the credibility, as well as the reputation of service providers, is at stake.
Shufti’s identity verification services are an ideal option for the telecommunication industry as it allows mobile service providers to identify clients’ real identities before getting them on board. Powered by thousands of AI algorithms our solution can authenticate with 98.67% accuracy in less than a second. In addition to this, the telecommunication service providers can also make risk assessment reports of high potential risk clients.
Want to know more about our Identity verification services for the telecom sector?

 Explore Now
Explore Now