How VCIP Supports Customer Due Diligence In High-Risk Transactions And Onboarding

Onboarding a new customer, making a high-value transaction, or opening a bank account are all high-stakes processes that require institutions to verify a person’s identity. The goal is to ensure they are onboarding the right individual and that the person is not a fraud.
In this digital economy, this process is usually carried out using online methods such as facial verification, AI-based checks, and self-declared information. However, unattended identity verification is vulnerable to loopholes.
As a result, in cases where the risk is higher, a stronger and more foolproof verification method is required. This is where Video-Based Customer Identification Process (VCIP) comes in.
What is VCIP?
VCIP, also sometimes referred to as Video KYC, is an attended verification process where a live agent joins a customer through a live video session to perform the required verification steps. It involves confirming the customer’s live presence, reviewing identity documents in real time, and matching those documents with facial data to ensure they belong to the person appearing on the video.
While VCIP is commonly used during customer onboarding, it is not limited to initial account creation. Many organizations also use VCIP as part of risk-based verification flows, both during onboarding and throughout a customer’s lifecycle. This includes scenarios such as high-value transactions, account changes, account takeover (ATO) frauds, suspicious activity reviews, or regulatory re-verification. All of these cases require stronger identity assurance beyond standard automated checks.
Video-Based Customer Identification Process
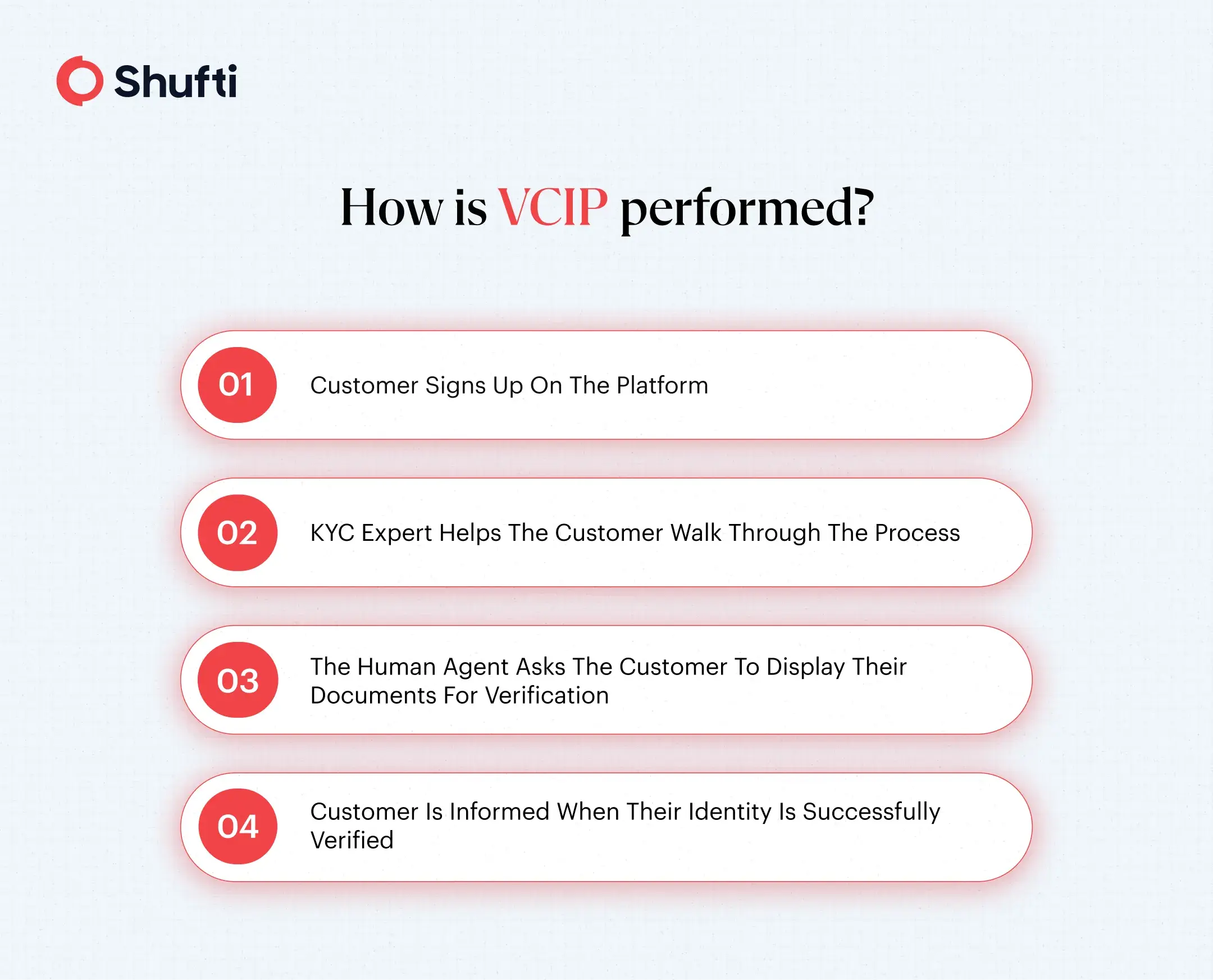
1) Sign Up
Customers sign up on the platform and join the KYC expert on a video call. The expert guides them throughout the process, making sure the verification is done quickly and with as little friction for the customer as possible.
2) Liveness Detection
The live video feed is analyzed by advanced technologies to make sure the video that’s being displayed is not a deepfake or a replay. KYC experts also interact with the customer and ask questions to further ensure that it is actually a live person sitting behind the camera.
3) Verification
The customer is then asked by the expert to display their ID card (or any other acceptable document), which is then analyzed for security features. In the case of an ID card, this may include verifying elements such as holograms, watermarks, and microtext to ensure the document has not been tampered with or forged.
4) Confirmation
Once the customer’s face is verified with the document, the process is completed, and the user is notified.
VCIP Regulations Across Regions
Below is a summary of how major regulators define and permit video-based customer identification.
India – RBI’s Master Direction (2016)
The Reserve Bank of India (RBI), under its KYC/AML framework, allows the use of VCIP as a valid remote customer identification method that can be used for remote verifications. According to the RBI’s Master Direction and recent clarifications, V-CIP can be used in real time through secure audiovisual interaction with a customer.
Germany – Circular 3/2017 (GW)
In Germany, the Federal Financial Supervisory Authority (BaFin) permits video identification procedures under its AML framework via Circular 3/2017 (GW). The circular sets out technical and organisational requirements, including real-time, uninterrupted video interactions, explicit consent at the start of the process, and trained personnel conducting the identification. These requirements aim to ensure video ID meets anti money laundering due diligence obligations under the German Money Laundering Act.
The UK – Money Laundering, Terrorist Financing and Transfer of Funds (2017)
In the United Kingdom, KYC and identity verification fall under the Money Laundering, Terrorist Financing and Transfer of Funds (Information on the Payer) Regulations 2017 (MLR 2017). These regulations state that firms that perform customer due diligence can identify and verify customers’ identities, but there has to be an expert or a relevant person doing the verification.
Choosing the Best VCIP Solutions
These are some of the key aspects of a software you should look for when evaluating a KYC solution:
- Regulatory compliance and regional coverage – Look for solutions that meet global and regional AML/KYC standards.
-
- Professionalism and language support of agents – Ensure Video KYC agents are professional, trained, and able to communicate clearly in the customer’s language.
- Risk-based verification support – Choose solutions that allow Video KYC to be used not just during onboarding, but also as part of risk-based verification flows, such as high-value transactions or periodic re-verification.
- Liveness detection and fraud prevention – Ensure the solution includes liveness checks and biometric verification.
- Ease of integration with existing systems – Opt for solutions that integrate seamlessly with your existing systems.
- Flexibility in verification workflows and operating models – Choose platforms with configurable flows and staffing options.
Conclusion
VCIP is a secure, compliant, and fraud-resistant verification method designed for remote identity checks, both during customer onboarding and throughout the customer lifecycle. Beyond initial onboarding, it plays a critical role in risk-based verification, such as validating identities during high-value transactions.
Shufti provides a reliable VCIP solution that combines live video verification with trained KYC experts, advanced liveness detection, and document and facial matching. These comprehensive solutions ensure that a real person is present during remote onboarding and that their identity is legitimate. With support for multiple languages, including German, Spanish, Hindi, and French, businesses can verify customers globally while maintaining a convenient and compliant verification experience.
Contact us to explore how you can integrate Shufti’s VCIP into your verification workflows and ensure regulatory compliance while scaling your business across markets.

 Explore Now
Explore Now













