Video KYC (VKYC) | Identity Verification and Fraud Prevention

In the last few years, the verification industry has experienced remarkable expansion. As our technological capabilities advance, so do the means by which hackers and fraudsters can commit financial crimes. This appeared in numerous forms, occasionally, hackers would access a person’s account and quickly empty it by using sophisticated methods of crime. But as technology has developed and artificial intelligence has taken hold, the illicit use of it has grown significantly over the past few years.
According to an FTC report, in 2022, consumers lost 8.8 billion to scammers, a 30% rise over the previous year. Finding an effective approach that can assist in real-time verification and secure operations no matter what, where, or when, is a challenge for businesses, financial institutions, and practically for all industries. Manual identity verification is insufficient to streamline operations and safeguard organisations as well as individuals, which is why they need a VKYC solution in practice that can assist them in separating true identity from spoofing and preventing fraud and criminal actions.
What is VKYC?
VKYC, or video KYC, is a method of video identification done both in person and remotely online with the help of a KYC agent. Customers must also digitally provide their identification documents for verification during this video meeting. An individual is instantly authenticated during video KYC, after which access can be granted or denied. VKYC is also known as video identification, video-based customer identification process, video verification, and video interview KYC in some nations and jurisdictions.
Video KYC will take several forms depending on how it is included into a company’s KYC routine. For instance, some businesses might decide to employ video conversations to connect users with real-time KYC agents, whilst others might decide to use automated video capture to record crucial KYC flow moments and look for signs of fraud.
What is the Procedure for Video KYC?
The video KYC procedure differs depending on the vendor and even the company’s needs. The VKYC typically has four steps, which makes onboarding and verification simple. These actions include:
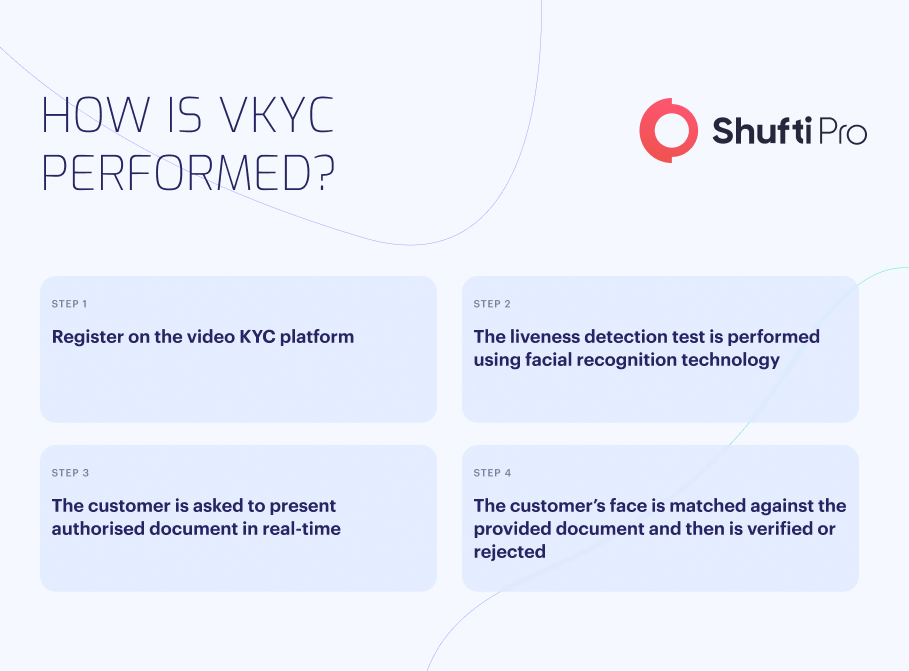
Registration on VKYC Platform
First and foremost, the process begins with the registration. The customer receives a video call from the KYC representative for additional detection after signing up.
Liveness Detection
Upon successfully receiving the call, the person is to screen against liveness detection. There are several methods to do it. KYC agents may interrogate each person separately or request to move. The major goal of this is to identify people to protect them from deep fakes, look-alikes, twins, amecas, real-life-like dolls, high HD resolution videos or photographs, sleeping, and hesitant users.
Provision of Document
Following the completion of the liveness detection, the subject is prompted to provide a valid government-issued document in front of the camera in real-time. Doing this not only verifies the individuals but also confirms that they are authorised and real.
Verify and Onboard
The person’s face is compared to the image of the document that has been submitted in the final step to ensure that it is authentic and has not been altered or fabricated. After all the procedures are finished, a choice must be made. If there are no indications of fraud or spoofing, the user is identified as a real person, verified, and onboarded. However, if the applicant has displayed any potential deep fakes or other indicators, they are rejected and put through additional screening.
How do Businesses Benefit from Automated Video KYC Solutions?
Digital video KYC is a complicated process, but it can nevertheless assist businesses in safely and remotely onboarding consumers. All-in-one digital VKYC solutions may assure compliance with regulatory standards, guard against fraud, and maintain high conversion rates even when they go beyond the usual doc+selfie verification.
KYC & AML Regulatory Compliance
Regulated sectors like banking, Fintech, Insurance, etc., must guarantee complete adherence to regional regulations. This is done to shield them from regulatory fines, terrorist financing, and money laundering. They are able to efficiently and affordably manage all the needs with the aid of digital onboarding solutions.
Fraud Protection
Online firms in the peer-to-peer, e-commerce, and automobile-sharing sectors fight fraud regularly. To gain access to these services, fraudsters utilise forged documents and identities that have been stolen. To make sure that only legitimate and authorised consumers are using their services, an increasing number of enterprises are turning to video identification systems.
Rate of Conversion
Organisations are very worried about losing clients whilst they are onboarding. However, video KYC is far more user-friendly than the manual option. Depending on their risk profile and transaction volumes, businesses can choose which users receive video verification. In this approach, they may decide whether to use regular KYC to increase their pass rates or video KYC when it is necessary by law or when the risks are great.
Improved Customer Experience
Customers can quickly, easily, and seamlessly complete their KYC needs with the use of video KYC. Wait times can be drastically decreased, and overall customer satisfaction can be increased by using Video KYC to remove the need for clients to physically visit a site.
The Growing Need for Video KYC in 2024
Many businesses have benefited from digitisation’s increased technology capabilities to speed up formerly time-consuming operations, but it has also offered thieves new ways to get around security safeguards, launching us into a chaotic fraud landscape. Video KYC can be used in the following ways to counter dangers like identity fraud.
Spoofing Attacks
Using artificial intelligence (AI) and cutting-edge technology, along with forged or stolen identification documents, imposters get beyond security barriers. By presenting a digitally manufactured face made from photos, 3D-rendered models, and masks, criminals try to get around facial recognition systems.
Synthetic Identities
As real information, like a social security number (SSN), is combined into a fake document to pass onboarding and KYC checks by misrepresenting such data, synthetic identities are significantly more sophisticated and difficult to detect. In the early phases of fraud, such faked documents are difficult to spot, but video KYC offers an efficient way to mitigate these emerging hazards.
Deep Fakes
Deep fakes are videos that have been fabricated using advanced deep learning technology to get past security precautions and gain unauthorised access to a network. For instance, during this level of face verification, a deep fake video is issued if the verification process calls for a video of the consumer.
Key Considerations for Successful Video KYC Implementation
To guarantee a smooth and efficient implementation of video KYC, many elements must be carefully taken into account. Businesses can implement video KYC that is quick and compliant by concentrating on six important factors.
Selecting the Right Video KYC Solution Provider
For a successful implementation, selecting a reputable and knowledgeable video KYC solution provider is essential. Businesses should assess the provider’s level of knowledge and expertise in the customer verification industry. To suit the business’s particular requirements and potential future expansion, it is crucial to evaluate the solution’s flexibility, integration, and customisation possibilities.
Regulatory Requirements Compliance
When implementing video KYC verification, it is crucial to keep up with essential regulations and requirements. Businesses must make sure the selected solution complies with all applicable compliance requirements and industry standards. Businesses can maintain compliance and stay out of trouble by routinely updating their systems to conform to changing regulatory requirements.
Integration with Existing Systems and Workflows
For an efficient onboarding procedure, video KYC must be integrated seamlessly with current systems and procedures. The solution must interact with the company’s customer management systems and make it simple to integrate video KYC into the current onboarding process. Customers won’t experience any delays or interruptions as a result of the process’s coherence and efficiency.
Utilising Technology to Improve Verification
Artificial intelligence (AI) and machine learning (ML) algorithms are examples of technological developments that can improve the verification process. A further level of security and accuracy can be added to the verification process by integrating facial recognition and biometric identification methods with video KYC. Businesses can manage their compliance requirements more efficiently by adopting a risk-based strategy for identifying and evaluating questionable transactions.
Ensuring Data Privacy and Security
VKYC procedures place a high priority on data protection and privacy. Organisations must put robust data security measures in place, such as encryption and safe customer data storage. To earn customers’ trust while ensuring regulatory compliance, businesses must abide by data privacy laws like the General Data Protection Regulation (GDPR).
Collaboration with Regulatory Authorities
Businesses employing video KYC must keep lines of communication open with regulatory bodies. Regular audits and assessments assist in ensuring compliance with legislation and show a commitment to battling financial crime. They also help keep up with changing compliance needs.
Conclusion
By taking into account the capabilities provided by the vendor, businesses may build the groundwork for an effective video KYC implementation and safeguard identities whilst saving money on operational costs. VKYC solutions are desperately needed by both businesses and people to stop illicit operations and maintain compliance standards to avoid fines, sanctions, and reputation damage. A flawless and efficient client verification process depends on choosing the correct solution provider, making sure that all legal requirements are met, and integrating the system with current workflows. As a result, the business’s overall security and compliance framework is strengthened, operational complexity is decreased, and customer satisfaction is increased.
How Can Shufti Help?
Shufti‘s VKYC solution can identify the most intricate and complex fraud attempts by using cutting-edge technology to protect your organisation from identity theft, fraud, and other financial crimes. We are a global company whose tools reflect our commitment to building international trust. Our customers have a demonstrated track record of raising custom satisfaction standards and increasing conversion rates with real-time verification readily available anywhere at any time. Our video identification solution reduces customer onboarding costs by 80% whilst removing unnecessary delays, friction time, and maintaining compliance.
Need to verify the individuals in real-time but scared of long, expensive processes?

 Explore Now
Explore Now













