KYCC – Going an Extra Mile to Prevent Financial Crimes

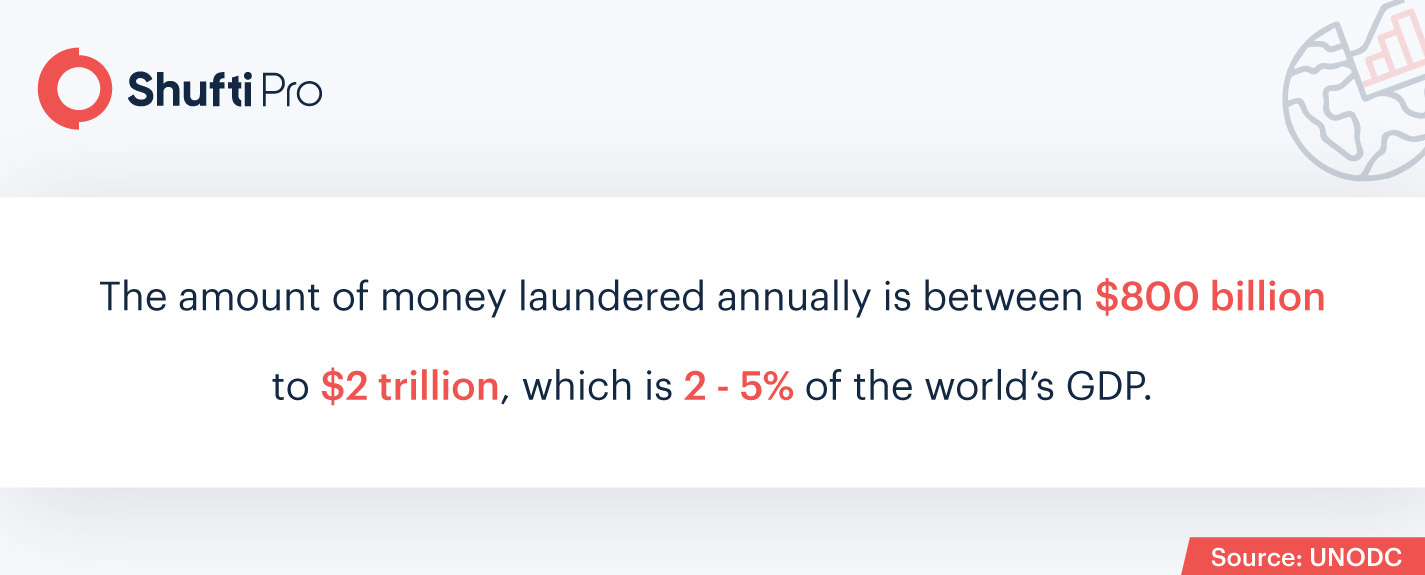
As cases of money laundering and terror financing are increasing globally, the concerns to overcome the gaps in the compliance measures related to identifying and verifying UBOs are rising. Mostly, shell businesses are set up to launder illegally earned money or to carry out other financial crimes. Global financial watchdogs are now deliberately working on establishing and imposing more rigid regulations to prevent fraudulent activities through shell companies.
Know Your Customer’s Customer (KYCC) process provides businesses a way of keeping an eye on their partnering customers, determining their source of income, its authenticity, and the potential threat of financial crimes they may pose to corporate entities.
Does KYCC Help in Preventing Money Laundering?
Know Your Customer’s Customer (KYCC) verifies the identities of Ultimate Beneficial Owners (UBOs) and their source of income. By screening UBO identities against global watchlists, businesses can make sure they are onboarding legitimate shareholders and prevent money laundering and other criminal activities.
The Pandora Papers – The Biggest Ever Leak of Shell Companies Data
The concealed deals and hidden assets of some of the world’s wealthiest and powerful people have been uncovered in the biggest leak of offshore data in history.
Pandora Papers is a database that holds 11.9 million sensitive files regarding offshore shell companies and trust in tax havens such as Dubai, Monaco, Cayman Islands, and Panama.
The paper exposed the offshore activities of 35 world leaders, consisting of current and former heads of states and prime ministers. 300 other public service officers, from more than 90 countries, were also alleged of having illegal assets.
Additionally, celebrities, rock stars, and business tycoons were also exposed as many use shell businesses to hold expensive properties, yachts, incognito offshore accounts, etc.
The pandora papers also uncovered the internal criminal operations of the financial world, providing insight into the hidden patterns of the world’s offshore economy that provides the world’s wealthiest people to invest their funds in shell businesses.
The pandora papers outline the latest and largest in terms of data volume, in a series of leaks of financial data science 2013. Rendering benefits from offshore businesses is not itself illicit, and in many cases, people may have legit reasons, like security, for doing so. The anonymity provided by the tax havens, however, has always proven attractive for money launderers, terrorist financing groups, and tax evaders, some of which have been exposed in the Pandora Papers.
Shell Companies – A Red Flag for Legit Businesses
The Panama Papers confirmed that the offshore arrangements exist to provide the people a gateway of doing things they can not do onshore. Whilst entirely legit, offshore assets, shell businesses, and the digital address are being used to hide out the real identities of Ultimate Beneficial Owners (UBOs).
Shell companies being anonymously established in countries having weak KYC and AML regulations are utilized by the criminals to commit various financial crimes, some of them are enlisted below:
-
- Forged billing schemes: Creating a fake invoice for business payments
- Money laundering: Rendering illegitimate gains and hiding them in the offshore shell companies
- Tax evasion: Hiding assets and other financial information from tax collecting bodies.
- Bribery and corruption: Facilitating government and public briberies
- Terrorist financing: Aiding terrorist groups.
- Drug and human trafficking: Routing illicit gains to assist drug and human trafficking businesses
These examples clearly illustrate that shell business are a red flag for legit companies. Developing a B2B relationship with such companies will put the clients in real danger and expose them to financial crimes. Due to this reason, the partnering businesses have a significant chance of getting sanctioned from the regulatory bodies, hefty fines, and bans.
Insights Over UBO Global Regulatory Requirements
Company’s UBOs hold great significance in B2B relationships. Ultimate Beneficial Owners (UBOs) are individuals that control as well as have influence over the company. In most countries, the threshold to be considered a UBO is having at least 25% of businesses ownership.
Laws and regulations regarding UBOs vary from region to region, some of them are listed below:
Europe
- In the EU, under the 6AMLD, UBOs are individuals having business ownership of 25% and voting rights
- Any sort of changes in companies UBOs status must be reported to the country’s regulatory body within 30 days
- Businesses are liable to pay five million euros and face four years of imprisonment for being non-compliant with UBO reporting compliance
- Under 6AMLD, the UBO information must be publicly accessible, aiming to reduce the transparency in business relationships
United Kingdom
- Under AMLD6, UBOs registers must be publicly available to reduce the transparency in ultimate beneficial owners’ data, having the objective of preventing the risk of financial crime
- Person with Significant Control (PSC) must undergo AML screening as a regulatory obligation
- AMLD6 states that in case of UBOs can not be identified, the businesses must verify the senior-most entity of the company and maintain the records of proceedings
- Customer due diligence protocols must be followed before establishing UBO relationships and authentic proofs must be gathered.
United States
- According to the CDD Final Rule, identifying and verifying the true identities of the UBOs are mandatory for the businesses before developing relationships
- Companies must understand the purpose and nature of the client’s relation to creat customer risk profiles
- Ongoing monitoring systems must be deployed to keep an eye over clients’ activities and have a mechanism of reporting suspicious activities to the regulatory bodies
- On the basis of a risk-based approach, customers data logs must be maintained and updated regularly
- Businesses are mandated to report significant changes in UBOs information to Financial Crimes Enforcement Network (FinCEN)
Japan
- The Act on the Prevention of Transfer of Criminal (APTC) requires financial corporations to identify UBOs when developing corporate relations with other businesses
- Financial Institutions (FIs) are mandated to practice EDD procedures if suspicious activities are detected or the clients are trying to manipulate the FIs. Additionally, financial transactions being carried out in high-risk countries must also be verified
- Suspicious Transaction Report (STR) must be provided to the regulatory bodies when the UBOs of the partnering business can’t be identified. STR must be submitted if there are proofs of suspicious financial transactions or involvement in criminal activities
- Regulatory entities have established sanctions of up to two years of imprisonment and/or a fine of three million Yen for failures to comply with the AML regulation
Final Thoughts
Investigating shell businesses and their UBOs is a challenging task. Acquiring clients’ information for verifying the corporate entities requires persistent follow-through. Mostly, such illegal companies operate in countries having weak AML/KYC regulations.
Shufti’s AI-powered identity verification solution verifies the authenticity of government-issued identity documents in less than a second. With 98.67% accurate identity verification results, businesses can ensure they are getting in touch with the right investors. Furthermore, AI-backed Know Your Business (KYB) verification allows companies to verify partnering firms and their source of income. Backed with AML screening, businesses can ensure that they are not onboarding shell companies and facilitating the flow of illegally earned money through their organization.
Want to know more about UBO verification AML screening? Get in touch with us.

 Explore Now
Explore Now














