Identity Verification – Addressing the Challenge of Fraud in the Telecommunications Sector

Transforming technology, growing digitization, and increased use of online transactions have accounted for a large amount of users’ data shared on the internet. In order to use the telecommunication platforms, users have to input their personal details which eventually leads to the risks of identity theft and financial fraud. The dependency of the entire telecom industry on digitization without effective identity verification measures has increased the potential risk for cyber attacks encouraging criminals to carry out their illicit motives.
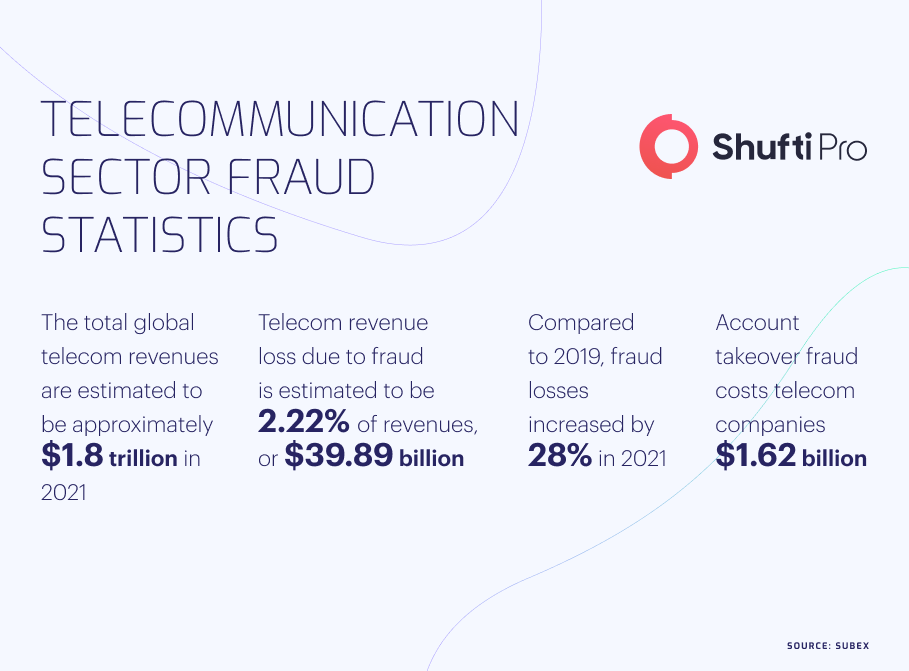
In 2021, 75% of telecom network operators experienced incidents of fraud while 61% reported that network security threats have increased as compared to last year. Criminal activities in the telecommunication industry resulted in a revenue loss of $38.89 billion with the expectancy to grow in coming years. Sim swap fraud, account takeover, and subscription scams are the major ones resulting due to a lack of identity verification services. Curbing financial crimes and identity theft fraud through stringent measures has become imperative for the smooth flow of digital transactions.
Telecommunication Fraud – A Huge Threat to Digital Operations
The exponential increase in the use of mobile devices over the past few years has compelled telecom industries to introduce the concept of digitally onboarding new users. Even though this trend is cost-efficient and user-friendly, it has encouraged bad actors to join networks using stolen identities further resulting in financial crimes. All the crucial sectors including banks and online fund transfer apps are directly or indirectly connected to the telecommunication industry posing huge risks to the whole economic system.
All the global regulators are working tirelessly to eradicate these criminal practices but fraudsters always manage to find the loopholes and exploit the system. IDC has estimated that currently there are more than 200 different types of techniques used by imposters to carry out their illicit motives and the number is increasing with the emergence of new technologies. CFCA has termed IP manipulation, call-back schemes, SMS phishing, and subscription fraud to be the top fraud methods in the telecom sector.
Telecommunication Fraud
Due to a huge number of users and a lack of identity verification measures, it has become a gruesome task for authorities to identify the culprits behind telecom scams. Sim swapping, CLI manipulation, and robocalling are some of the crimes in the telecommunication industry which are hard to identify without strict identity verification checks. All the global authorities and responsible countries are working tirelessly to eradicate this menace and in the recent past, a number of legislations and crackdowns have been observed to control these scams.
China Crack Down on Telecom Scammers
China is considered a country top affected by this crime which led the authorities to take decisive action against all bad actors. Ministry of Public Security along with other authorities initiated a huge crackdown addressing 394,000 scam cases while interrogating 634,000 suspects involved in illegal activities.
Around 42,000 criminal gangs involved in sim card fraud were busted which led to punishments for 440,000 suspects. Due to these nationwide campaigns, the number of cases of telecom fraud in China has been continuously dropping for more than six months and is expected to decrease further.
Hundreds arrested in Global INTERPOL Investigation in Telecom Sector
Interpol along with 76 other countries conducted a two-month international clampdown against organized crime groups behind telecommunication and other social engineering frauds. During this operation, police in all the participating countries raided the call centres and other suspected organizations involved in telecom scams particularly email deception, romance scams, and connected financial crimes.
As per the official statement by Interpol, some 2000 operators have been arrested, 4000 bank accounts are frozen and $50 million of illicit funds are intercepted. Interpol has further mentioned that investigations are still ongoing and these numbers are expected to rise.
Global Regulations Monitoring Telecom Operations
Telecommunication fraud has taken the form of a global threat, eliminating which is quite crucial for the smooth flow of operations. The majority of the countries have established telecom authorities that are regulating the whole industry and taking measures to keep criminals away and ensure transparency.
Federal Communications Commission of the USA
The Federal Communications Commission (FCC) in the USA is responsible for enforcing telecommunication laws in all 50 states. FCC works directly under the President of the United States and has the authority to propose laws and regulations to the Senate and House of Representatives.
Fighting robocalls, spoofing and other telco scams are on the list of FCC initiatives, and it has vowed to protect and empower consumers in the sector.
Communication Act UK
The Office of Communication (Ofcom) is the regulatory body in the UK that is working under the Communication Act to eliminate scammers from the telecom industry. The primary role of Ofcom is to develop and enforce laws linked to the telecommunication industry.
The department is completely responsible for establishing a telecommunication regulatory network within the country.
Australia
Australian Communications and Media Authority (ACMA) is working tirelessly to eradicate telephonic and SMS scams. It has been reported that SMS scams in the country have increased by 188% as compared to the same period in 2021.
In order to eradicate SMS frauds, ACMA has implemented a new set of rules as per which advanced codes are registered to filter the scammers out of the system.
Eliminating Telecom Frauds with Identity Verification
Although a hard task to accomplish, telecom industries are short of options other than implementing strict Know Your Customer (KYC) measures to put an end to scams. The telecommunication industry can follow the model of banks and other financial institutions which have implemented KYC solutions, preventing risks of identity fraud and other financial crimes. By incorporating KYC checks in vulnerable areas, telecom operators can eliminate the threats of fraud and control monetary losses.
Any system efficient enough to screen consumers while onboarding can serve the purpose. Moreover, anti money laundering (AML) screening should also be made part of the system to ensure money launderers do not exploit the system. To implement KYC and AML solutions, the telecom sector needs an efficient service powered by artificial intelligence with access to sanctions lists by global watchdogs.
What Shufti can Offer?
Shufti’s state-of-the-art Know Your Customer (KYC) and anti-money laundering (AML) screening measures can help the telecommunication industry enforce enhanced customer monitoring checks. Powered by artificial intelligence algorithms, Shufti’s solution can screen consumers against 1700+ global watchlists and produces output in less than a second.
The identity verification services are the optimum solution for telecommunication companies to identify the real identities of clients while onboarding. Shufti’s solution is the most viable option which will provide output with 98.67% accuracy.
Want to know more about identity verification and AML screening solutions?

 Explore Now
Explore Now













