How Shufti’s KYC Solution Can Ensure Compliance For Call Centers Fighting Crime

With emerging technologies and rapid digitization, the world is relying on the web and a variety of digital tools more than ever before, ultimately making lives convenient for users. With all this newfound ease, cybercriminals have also discovered their way into the system by exploiting loopholes and seizing opportunities for committing fraud. Call centers have become a huge source of digital scams where criminals use a myriad of techniques like robocalls, fake SMS messages, and phishing, convincing customers to purchase fake products and services, eventually leading to users losing their money.
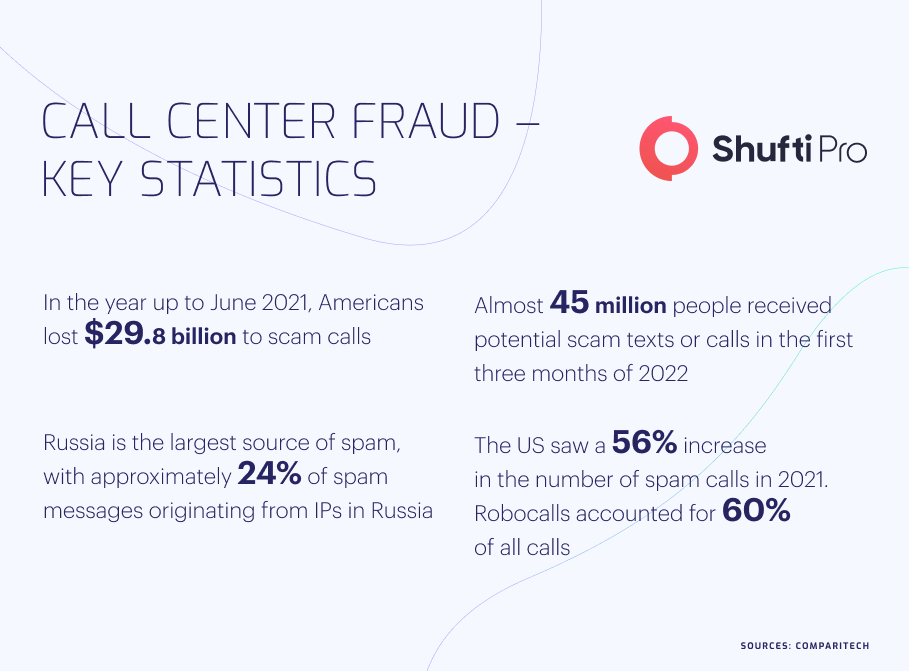
In Q1 2021 alone, $29.8 billion was lost in scams related to call centers which have highlighted the importance of identity verification measures for the sector. Unlike banks and insurance companies, call centers have not implemented strict Know Your Customer (KYC) measures resulting in an increased crime ratio compared to the overall industry.
An Overview of Call Center Fraud
Although the advancement in digital technology has eased a lot of operations, it has also encouraged cyber criminals to use more sophisticated methods to carry out different scams. The fraudsters make calls to users, pretend to be the agents of legitimate companies or banks, and ask for sensitive details. Once the users provide their confidential details, they can get access to different assets like bank accounts, credit card accounts, cryptocurrency wallets, etc., and use the maliciously obtained credentials for financial gain. The scammers use a variety of advanced software for this purpose which lets the customers believe that they are official representatives of a given company.
It’s not just consumers either, various industries, particularly banks, governmental agencies, and the telecommunication sector, are also facing threats posed by call center scams. Identity theft is one of the primary frauds which is linked to fake calls, which further gives rise to a large number of crimes like account takeovers, fake bank account openings and illicit financial transactions. It is quite crucial that regulatory authorities step in and enforce strict KYC measures, which can help verify a user’s true identity while onboarding and keep detailed records to track criminals in case of any future fraud.
High-Profile Criminal Cases Targeting Call Centers
Due to the rising amount of crime by scammer call centers, all major jurisdictions are either legislating new laws or amending existing ones to prosecute criminals and bring them under the law. Across the globe, several cases have surfaced recently where law enforcement authorities arrested criminal gangs involved in scams related to call centers.
108 Persons Detained in Latvia and Lithuania
The law enforcement agencies of Latvia and Lithuania, along with Europol, conducted a major operation and arrested 108 criminals involved in a number of crimes, including call center scams, money laundering, and terrorist financing. The Police have reported that scammers were running a call center where they had hired a large number of employees who were experts in multiple languages. They used to call common people and companies, urging them to invest money in different schemes, ultimately leading to fraud. It has also been found that criminals were using money laundering techniques to send money out of the countries. A Joint Investigation Team (JIT) has been set up to probe the whole case and bring culprits to justice.
McLean Man Sentenced for Call Center Scam
A man in the US has been sentenced to three years in prison for his participation in a scam defrauding $1.6 million out of 1300 victims. The investigations have found that the criminal was running a call center and contacted unsuspecting users through fake calls or emails, offering them contracts with his companies in return for heavy profits. In the wake of several complaints by victims, Police raided the place, arresting him and his accomplices.
Types of Call Center Fraud Reported in 2022
The number of fraud cases and fraudulent attempts are rising every year, costing victims financial losses in the billions. Let’s have a look at the top call center fraud types which are the most reported in 2022:
Identity Theft
Identity theft is the most common scam linked to call center fraud where criminals use stolen details of sophisticated users, including credit card details, mobile phone numbers, and identity card numbers, to fool call center agents while convincing them to do financial transactions. Identity theft is difficult to track as criminals use almost all legitimate details to commit fraud.
Account Takeover
Another popular fraud is account takeover, where cyber criminals try to change sensitive details like passwords, PINs, and usernames by calling call centers. They usually provide the right details of verification which lead the call center agents to believe they are account owners and change credentials. In this way, the scammers take over the account, and then they are open to making any further changes or performing financial transactions.
IVR Mining
Interactive Voice Response mining is quite a complex process that criminals use to abuse call centers through automated calls. They usually go through a series of questions on a trial-and-error basis to enter the system and exploit it further. IVR systems are automated, which means they can’t always detect fraudulent activity, and it’s possible for cybercriminals to contact them multiple times until access to the unsuspecting victim’s account is gained.
Global Regulatory Authorities Monitoring Call Centers
Regulatory authorities in almost all the major jurisdictions are working tirelessly to eradicate call center fraud, which is costing users and companies huge financial losses. With each passing year, the amount of crime in this sector is rising which has raised concerns for financial watchdogs to urge countries to form a comprehensive framework eliminating risks of identity theft and other monetary scams.
US
Federal Communications Commission (FCC) is the primary authoritative body that regulates the whole US telecommunication sector, including call centers. FCC has termed malicious and fraudulent calls a big threat to the whole financial system and urged call centers to implement stringent KYC measures to verify the true identities of callers. FCC has also instructed contact centers to urgently report suspicious activity through their portals so criminals can be brought under the law.
UK
The UK government has made a dedicated department, “Action Cell” where the call centers can report any suspicious call by the callers. It is also working to form a robust system of identity verification that can reveal the true identities of all callers and quickly identify criminals trying to abuse the system.
How Shufti Is Helping Mitigate Call Center Fraud
Combating crimes, particularly identity theft, account takeovers, and other financial scams, is crucial for the call center industry. The customer support department is often thought of as the most important part of any business. It is here to stay and thus now is the right time for call centers to invest in identity verification measures to secure their users’ identities and assets.
Shufti’s state-of-the-art identity verification services are a viable option for authenticating the true identities of callers and reporting suspicious activities in the system. Powered by an AI algorithm, Shufti’s KYC solution will screen the user details against their documents and provide results in just seconds with a 98.67% accuracy.
Ready to discover our KYC solutions for call centers?

 Explore Now
Explore Now













