Blog
KYC Verification Process – 3 Steps to Know Your Customer Compliance
Since the turn of the century, we’ve been propelled into a technological revolution. As digital i...
 Explore More
Explore More
Blog, Identity & KYC
How Brexit Impacts UK-based Identity Verification Companies?
Brexit and its ramifications for the UK seem to be the only topic that anyone is interested in Br...
 Explore More
Explore More
Anti Money Laundering, Blog, Reg Tech
RegTech facilitates effortless AML Compliance
The latest report by Research and Markets states that RegTech industry is expected to grow...
 Explore More
Explore More
Blog
From Fraudsters to Artists – The Dire Need of AML Compliance for NFTs
Over the past few years, NFTs or Non-Fungible Tokens have become popular in the crypto sector. Ac...
 Explore More
Explore More
Blog, Online Marketplace
How Car Rentals can safeguard their interest with Digital KYC?
Car rentals stand to benefit a great deal from Digital KYC as it will enable them to verify the c...
 Explore More
Explore More
Blog
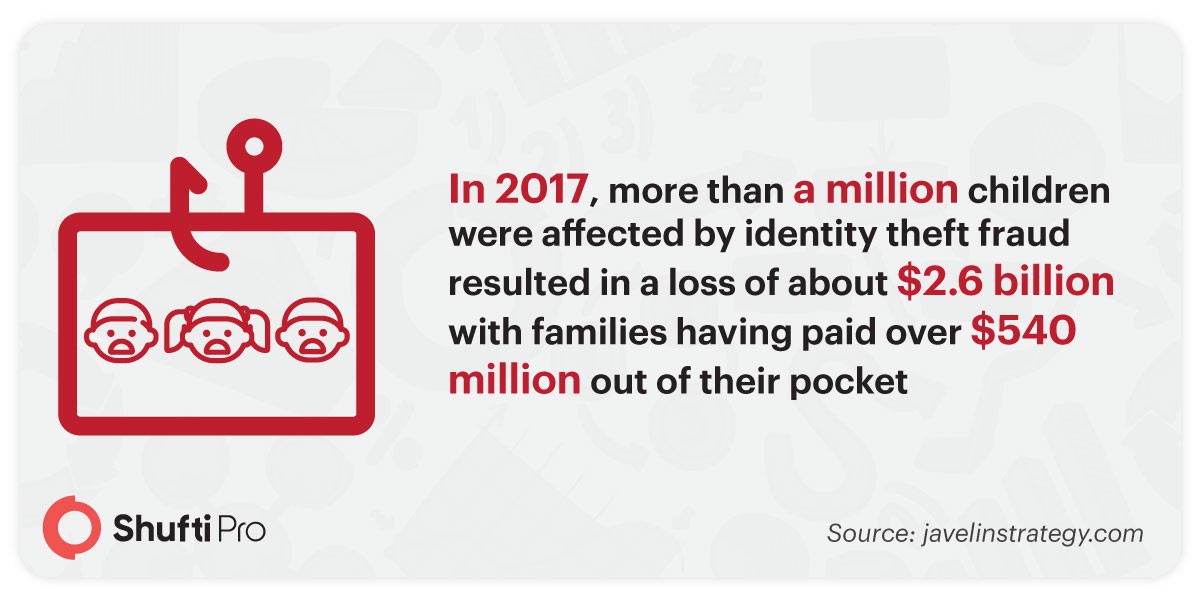
Combatting Identity Theft with KYC Verification – A Risk-Based Approach in Online Shopping
The proliferation of online stores has radically transformed how people shop and greatly affected...
 Explore More
Explore More
Blog
COVID-19 & Telehealth Fraud: Why ID Verification Is Necessary
From being a medical coverage option to becoming a medical necessity, the telehealth industry has...
 Explore More
Explore More
Blog
Know Your Player | Onboard Verified Gamers and Scale Globally
In today’s digitised gaming world, player verification stands as a cornerstone for onboarding leg...
 Explore More
Explore More
Blog
Digital ID Verification – Why is it Critical for Customer Experience?
Last year was all about lockdown and pandemic disrupting business operations to the very core. Th...
 Explore More
Explore More
Blog
Financial Regulations Against Crypto Sanctions Evasion in the UK – Is the Crypto Sector Safe?
Many governments throughout the world are facing concerns of money laundering and sanctions evasi...
 Explore More
Explore More
Blog
Secure the Fintech Future with RegTech
Financial Technology (Fintech) refers to the use of technological advancements in the financial i...
 Explore More
Explore More
Blog
Mounting Cases of Money Laundering through Digital Currencies in 2021
Even though cryptocurrencies like Bitcoin, Ethereum, and Dogecoin are increasing rapidly, yet the...
 Explore More
Explore More
Blog
Improving Identity Verification Processes Through Perpetual KYC – How Shufti Helps the Banking Sector
Banks are considered a subset of the financial services industry and play the most crucial role i...
 Explore More
Explore More
Blog
Initial Exchange Offerings (IEOs) – A Detailed Insight
The advent of the Crypto industry brought decentralized and innovative fundraising ways. One of t...
 Explore More
Explore More
Blog
The Digital Black Market for Identity Data
The collection, purchase, or trade of customer data is big business. Unless organizations and ind...
 Explore More
Explore More
Blog
A Comprehensive Guide to Choosing a Perfect e-KYC Solution for Businesses
Most of our processes, including financial and business dealings, have now shifted to online plat...
 Explore More
Explore More
Blog
Real Estate Industry Crimes and Strict AML Regulations – How Shufti Can Help
The real estate industry has long provided a safe way for fraudsters to secretly launder or inves...
 Explore More
Explore More
Blog
Deepfakes: AI Fraud Attacks Require Even Smarter AI Countermeasures. Now.
Verifying identities with advanced biometrics was already a challenge—then along came AI-generate...
 Explore More
Explore More
Biometric Technology, Blog, Online Marketplace
Face Verification Becoming Vital For Travel Industry
Over the past few years, biometric technology has become increasingly mainstream. This is due in ...
 Explore More
Explore More
Blog
The Priorities – FinCEN Issues First Governmentwide AML/CFT Guidelines
What is the Goal of FinCEN’s AML/CFT Priorities?CorruptionCybercrimeFraudProliferation FinancingT...
 Explore More
Explore More
Blog, Online Marketplace
ID Verification – Fraud Prevention in Online Gambling Industry
By its very nature, gambling is quite risky. Add to it the potential for fraud that it attracts, ...
 Explore More
Explore More
Anti Money Laundering, Blog, Financial Crime / AML, Identity & KYC
Winter is Coming: With a Storm of KYC and AML Regulations
The ever-evolving regulations are creating challenges and complexities for the financial institut...
 Explore More
Explore More
Blog, Online Marketplace
How Car Rentals can safeguard their interest with Digital KYC?
Car rentals stand to benefit a great deal from Digital KYC as it will enable them to verify the c...
 Explore More
Explore More
Blog
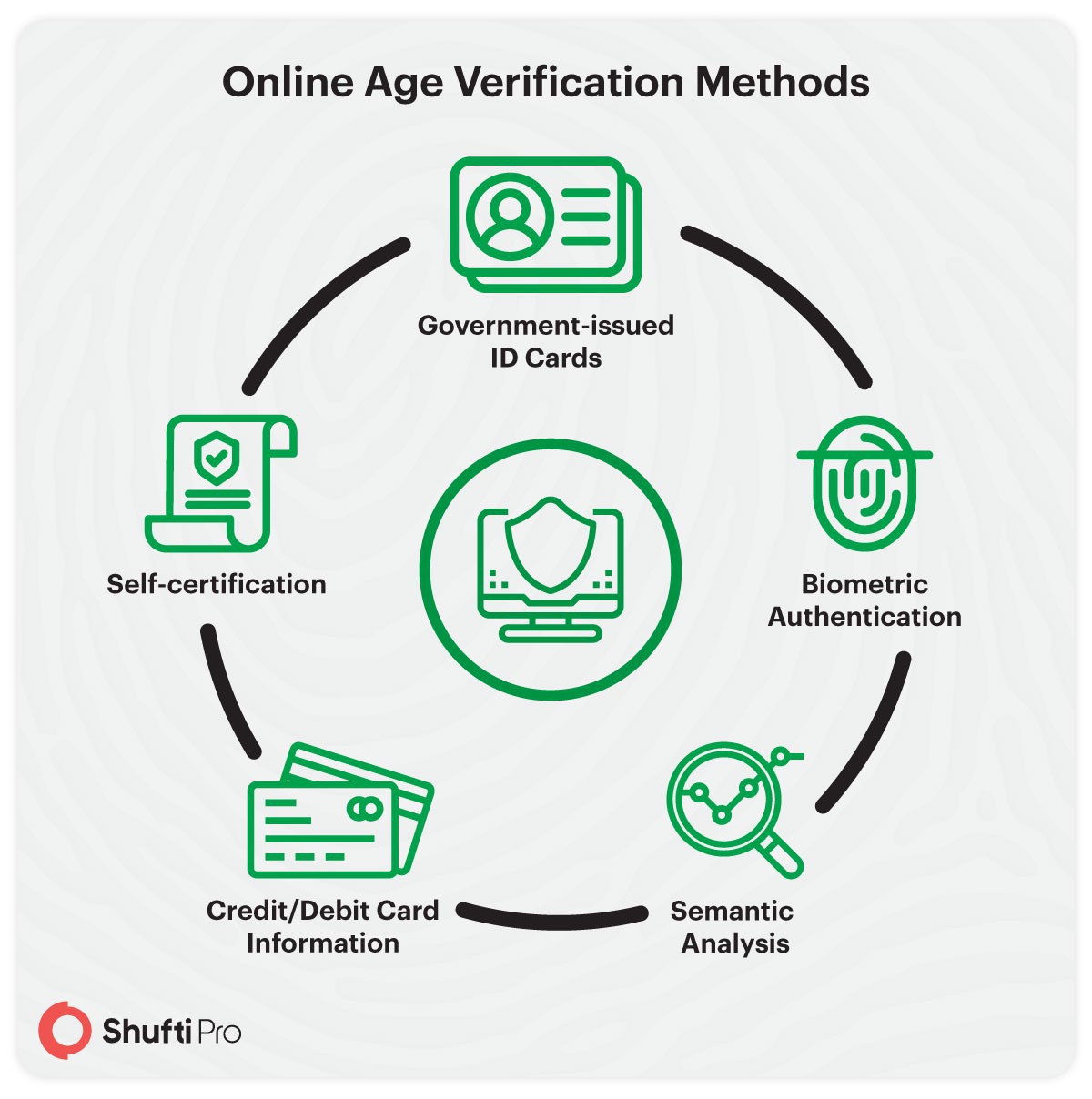
Age verification regulations demanding better compliance from businesses
“Youth is the hope of our future.” Jose Rizal
It is no secret that the youth is a valuable asse...
 Explore More
Explore More
Blog, Identity & KYC
4 Reasons Why Brokerage Firms Need ID Verification?
According to Steve Grobman, Chief Technology Officer for McAfee, “The digital world has transform...
 Explore More
Explore More
Blog
Securing Cryptocurrency Sector and Fighting Financial Crimes With Shufti’s AML Solution
A decade ago, digital currencies were an academic concept, largely unknown to the world’s general...
 Explore More
Explore More
Blog
How Businesses Can Avoid Identity Verification Fraud in 2019?
With a bulk of customers using online services, businesses wish to digitise their operations and ...
 Explore More
Explore More
Blog
The Definitive Guide to Anti-Money Laundering & Countering of Terrorist Financing
In this modern globalized era, money launderers, terrorist financiers and other criminal elements...
 Explore More
Explore More
Blog
Antiquities Market – A Conduit of Money Laundering and Terror Financing
Money laundering and terror financing through art and antiquities has been a concern of regulator...
 Explore More
Explore More
Blog
Youtube Stepping up to Protect Minors’ Data Online
The explosion of the internet and mobile devices has paved new ways for marketers and Cybercrimin...
 Explore More
Explore More
Blog
Securing Banks and Curbing Financial Crimes with Shufti AML/KYC Solution
Banks and other financial institutions constantly face the challenges of tackling financial crime...
 Explore More
Explore More
Blog
KYC and Blockchain – The Foundation of a Secure Crypto Landscape
Blockchain technology has demonstrated fast-paced growth throughout the world and now faces the c...
 Explore More
Explore More
Blog
How Shufti’s KYC Solution Can Ensure Compliance For Call Centers Fighting Crime
With emerging technologies and rapid digitization, the world is relying on the web and a variety ...
 Explore More
Explore More
Blog
ID verification Services – Why Paper IDs are inferior to Digital Cards?
ID verification services are at the forefront of making online marketplace transparent and ensuri...
 Explore More
Explore More
Blog, Identity & KYC
ICOs and KYC Compliance
With the surge in digitalisation of payments and crowdfunding; the need to set proper standards f...
 Explore More
Explore More
Blog
A Guide to Anti-Money Laundering (AML) Regulations in the UAE
As the Middle East’s financial hub, the UAE offers several enticing free trade zones that a...
 Explore More
Explore More
Blog
Shufti’s Secret to Acquiring 92% End-User Satisfaction Rate
Shufti, the global identity verification service provider, started from humble beginnings wit...
 Explore More
Explore More
Blog
Digital Identity Verification for Open Finance & FinTech Platforms
Financial applications in the modern world have been sub-categorized into open and closed banking...
 Explore More
Explore More
Blog, Financial Crime / AML, Fraud Prevention, Identity & KYC
Facial Recognition: Worries About the Use of Synthetic Media
In 2019, 4.4 billion internet users were connected to the internet worldwide, a rise of 9% from l...
 Explore More
Explore More
Blog
Fraud Prevention – Challenges, Strategies, Best Practices, and Technologies
The twenty-first century is by far the most revolutionary time in the history of humans in terms ...
 Explore More
Explore More
Blog
Establishing trust in Open Banking through Identity Verification
Over the last few years, open banking is becoming an emanated global trend. This rising trend is ...
 Explore More
Explore More
Blog
Shell Companies and Money Laundering: How to Combat Them?
Shell companies are notorious for all the right reasons. These entities often called ghost compan...
 Explore More
Explore More
Blog
Anti-Money Laundering (AML) Solutions – Ensuring Responsible Gambling and Data Protection
Like other industries, the gambling industry is also becoming a prime target of criminals. Howeve...
 Explore More
Explore More
Blog
AML Compliance – Addressing Financial Crime Challenges in the UAE’s Banking Sector
The United Arab Emirates (UAE) is fast becoming the world’s most reputable financial hub, but the...
 Explore More
Explore More
Blog
Identifying and Combating Trade-Based Money Laundering with Shufti AML Screening Services
The crime involved in trading is as old as human history. Where there is trade there is money inv...
 Explore More
Explore More
Blog, Identity & KYC
Why You Need To Know Your Buyer
Online payments are fast replacing cash transactions with the top payment companies harboring 1bi...
 Explore More
Explore More
Blog
CCPA Compliance Checklist – Is your business ready?
With the world moving towards digitization, organizations have a customer base from all around th...
 Explore More
Explore More
Blog
A Guide to Anti-Money Laundering (AML) Regulations in the UAE
As the Middle East’s financial hub, the UAE offers several enticing free trade zones that a...
 Explore More
Explore More
Blog, Fraud Prevention
8 Fraud Prevention Tips for a smooth business uptake in 2018
The Need for Fraud Prevention
As technology has evolved over the years, the way we do business ha...
 Explore More
Explore More
Blog
UK Elections: Photo ID Law Change Raising Concerns for Voters
Law changes bring several hassles for the public and government authorities. The recent photo ID ...
 Explore More
Explore More
Blog, Identity & KYC
Online Identity Verification – Why Shufti is Perfect for Digital Authentication
In a short period of time, Shufti has managed to make a significant mark upon the end-to-end ...
 Explore More
Explore More
Blog
Impact of California Consumer Privacy Act on Online Businesses
California consumer privacy act has been revolutionizing consumer data regulations. The act was p...
 Explore More
Explore More
Blog
Navigating the Changing Digital Finance Landscape 2023
The financial services sector has witnessed a rapid surge in the adoption of digital technologies...
 Explore More
Explore More
Blog
Enhanced Due Diligence – How to Identify and Deal with High-Risk Customers
Business relationships always come with associated risks that require carefully implemented measu...
 Explore More
Explore More
Blog
KYC & AML Regulations in the UK: An Ultimate Guide
Financial crimes have been around since the invention of money. Some argue that their origins are...
 Explore More
Explore More
Blog
Identity Verification vs Authentication: The Key Differences
Organisations today face significant concerns regarding data breaches and identity theft. Nearly ...
 Explore More
Explore More
Blog
The Definitive Guide to Anti-Money Laundering & Countering of Terrorist Financing
In this modern globalized era, money launderers, terrorist financiers and other criminal elements...
 Explore More
Explore More
Biometric Technology, Blog
How Liveness Detection is an apt Answer for Facial Spoof Attacks?
The world went haywire on the launch of the new iPhone X; well, to be honest, when does it not? H...
 Explore More
Explore More
Blog
Shufti’s Growth Skyrockets Above 100% in the Fiscal Year 2020
In 2020, Shufti witnessed a remarkable growth of over 100%. Together with this, it can comfor...
 Explore More
Explore More
Anti Money Laundering, Blog, Identity & KYC, Reg Tech
RegTech – FATF Guidance for Digital Identity Verification
Regulatory authorities have recognized the benefits of technology and its use for seamless regula...
 Explore More
Explore More
Blog
Age verification regulations demanding better compliance from businesses
“Youth is the hope of our future.” Jose Rizal
It is no secret that the youth is a valuable asse...
 Explore More
Explore More
Blog
ID Verification for Ultimate Subscription Fraud Prevention
Cellular phones were first introduced in the consumer market in 1973 when Motorolla first introdu...
 Explore More
Explore More
Blog
Keeping AI Bias Out of the IDV Game with Shufti
Consider this: 85% of financial institutions today use some form of AI in their products. The tec...
 Explore More
Explore More
Blog
e-IDV | Enhancing Fintech Onboarding, Operations & Compliance
Fintech is unprecedentedly growing and changing as it responds to the always-changing tech landsc...
 Explore More
Explore More
Blog
Multi-Tier Security – Another Line of Defense Against Bank Account Scammers
The banking sector has been witnessing a significant rise in criminal activities is a major conce...
 Explore More
Explore More
Blog
Expanding the UX Lens with Lisa Kleinman
Creating a UX experience can feel like a paradox: users are more diverse than ever, yet they expe...
 Explore More
Explore More
Blog
A Detailed Insight Into Australia’s Gaming and Gambling Regulations
In recent years, the online gaming and gambling industry has experienced significant growth as te...
 Explore More
Explore More
Blog
How Optical Character Recognition Improves the Process of Identity Verification for Businesses
Evolving technologies have created a competitive market where every business strives to optimize ...
 Explore More
Explore More
Blog
Know Your Customer – Addressing the Risks of Financial Crimes in Challenger Banks
With emerging technologies, financial services are witnessing a digital revolution that is changi...
 Explore More
Explore More
Blog
Navigating the New Era of Customer Identity: Strategies for Compliance Professionals
Introduction
The identity verification and authentication landscape is undergoing a rapid transfo...
 Explore More
Explore More
Blog
KYC/AML Compliance – Eliminating Financial Crime in Challenger Banks
Challenger banks have emerged in the financial services paradigm by bringing digital innovations ...
 Explore More
Explore More
Blog
Major Fines in the Gaming and Gambling Industry and the Role of e-IDV
The outbreak of Covid-19 has changed how we do business. Many firms that used to operate physical...
 Explore More
Explore More