Analyzing and Balancing the Variables of an Effective Identity Verification Solution

Today’s constantly transforming digital landscape where technology empowers businesses fast-paced operations, while new tech-driven tools bring negative consequences when used by the criminal activist. Risks of crimes like identity theft, money laundering, and terrorism financing are significantly augmented due to the use of sophisticated technology like photoshop and deep fakes. According to the Association of Certified Fraud Examiners reports, it’s forecasted that US businesses will lose an average of 5% of their revenues to frauds.
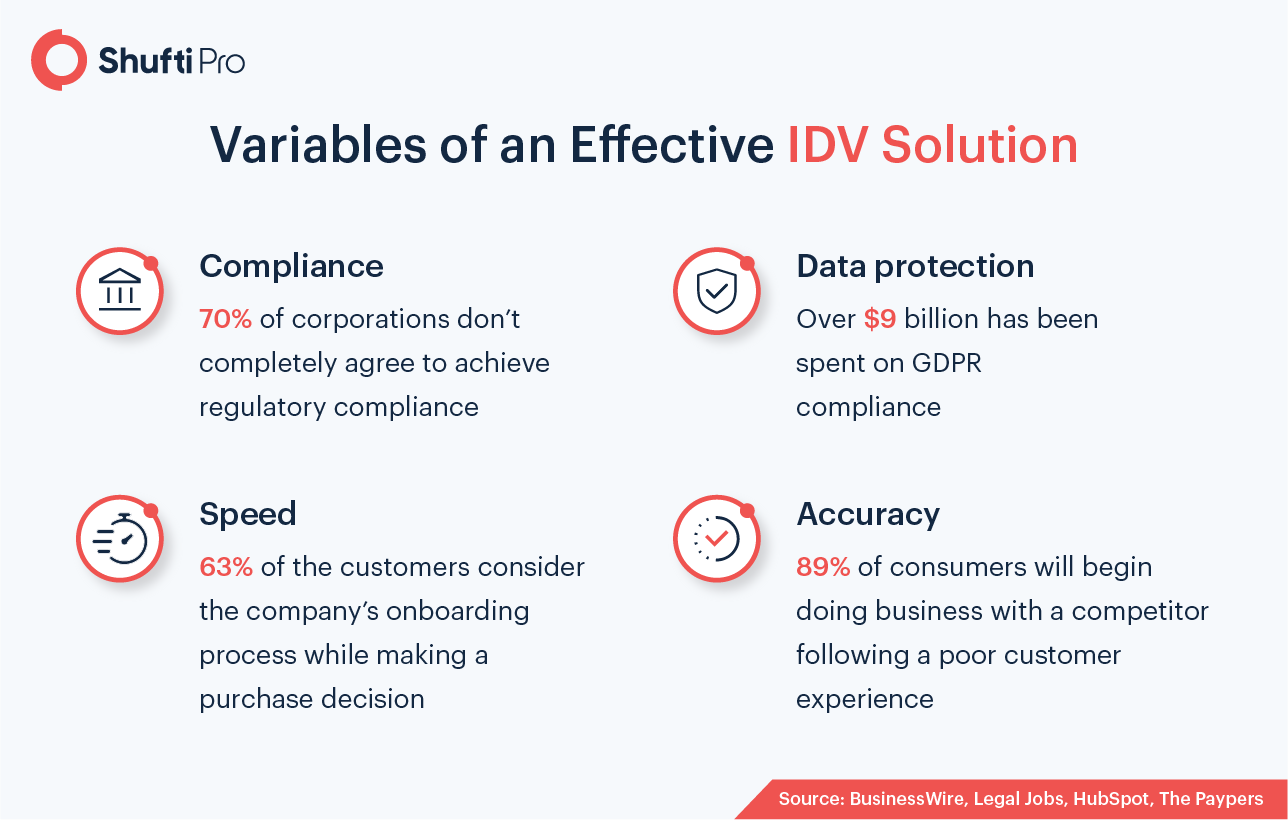
Businesses opt for third-party identity verification solutions. However, not every solution is able to balance the four variables of the ID verification equation.
1. Compliance with KYC Regulations
Banks and FinTech companies, in particular, are significantly affected by KYC and AML regulations for account opening and transactions. For the sake of convenience, customers prefer online banking services rather than the traditional system.
Know Your Customer (KYC) compliance is considered crucial because it determines clients’ information before establishing corporate relationships. It enables the corporations to carry out Customer Due Diligence (CDD) to authenticate clients to overcome the unnecessary risk of identity fraud, terrorist financing, money laundering, and other financial crimes. KYC regulations safeguard businesses from reputational damages due to cybersecurity breaches or manipulating attempts. Following are the components of the KYC compliance:
1. Simplified Customer Due Diligence
KYC checks are performed at the time of client onboarding. It’s usually carried out to assess the potential risk of crimes posed by customers. CDD doesn’t require comprehensive screening. It’s a simplified process as the clients are not classified as medium or high-risk profiles.
2. Standard Due Diligence
Businesses are obliged to carry out standard due diligence when the client is a public authority or a celebrity. Such customers are categorized as low or medium-risk processors. However, the set of standards varies across jurisdictions.
3. Enhanced Due Diligence
Financial institutions and FinTech companies often facilitate Politically Exposed Peoples (PEPs) and other high-risk clients that pose a high level of risk to businesses.. Such entities must be screened comprehensively to determine if they are involved in terrorist financing, money laundering, and bribery. In addition to this, companies’ Ultimate Beneficial Owners (UBOs) must be verified as well, along with the source of financial earnings. UBOs must be screened against the global financial watchlists, sanction lists, and PEPs lists to overcome the risk of financial fraud.
To meet the KYC compliance obligations, financial institutions and fintech businesses require an automated identity verification mechanism that can ensure convenience for the end-user and security for businesses. To do so, businesses have to opt for the cross-platform solution that holds new technology features like facial biometric authentication, capable of learning from real-life instances.
Data Protection
Data protection is one of the rising concerns for digital businesses these days. For the same reason, data protection regulations are rapidly growing globally. It’s expected that by the end of 2023, 65% of people’s data will be secured. The customers’ personally identifiable information that businesses acquire and store must be appropriately handled. From account credentials to financial information, all the data must be kept secure under the data protection laws.
For instance, the UK’s Data Protection Act holds a set of standards that the financial and FinTech organizations have to adhere to keep clients’ information secure. Data Protection Act key points are
- The acquired data must be used for specific task
- Businesses must not store data for a long time unless mandated by law
- The information must be used in defined ways
- No compromise over data security and protection
The Data Protection Act assists the companies to assure the clients’ and staffs’ information is protected. It’s the business’s responsibility to gather real information before onboarding them. However, data or security breaches can develop adverse consequences and can result in sanctions, penalties, and hefty fines. In some cases, the clients can also pursue compensation from the businesses.
Speed
Quality and speed are the most critical factors that businesses are continuously fighting for. Balancing both isn’t the end of the debate, it’s the race of maintaining position for the foreseeable future.
However, businesses that didn’t go for digitization are now rushing to opt for ID verification solutions. Keeping in mind that millions of people are using online services for the first time, many of them are exposed to cybercriminals. It means the businesses have to incorporate the ID verification systems that can provide robust and simple onboarding procedures. On the other hand, businesses having sluggish onboarding and verification systems result in a higher Registration Abandonment Rate (RAR).
Accuracy
If businesses lack automated identity verification systems, they are opting for manual means of verification. Ultimately, the loopholes in the ID verification system increase. It also bottlenecks the onboarding processes and slows down operations.
However, manual procedures usually rely on a tedious method of acquiring the ID documents from client to verify them. Manual verification requires ample time and generates heaps of errors. Such circumstances, unfortunately, impact the verification accuracy and provide an easy path for the fraudster to exploit the security framework.
Key Takeaways
The transition from conventional verification methods to automated procedures is becoming a business necessity. The AI-driven verification solution can overcome the unnecessary risk of human errors in verifying the customer’s identity along with their documents. In addition to these perks, digital identity verification can surely enhance operational productivity, lower the cost and provide a frictionless experience to the clients.
Shufti’s robust identity verification solution is ideal for businesses looking to grow in the digital world. AI-backed ID verification solution assists companies to stay put with the KYC regulation, secure customers’ data,and renders verification results in less than a second with 98.67% accuracy.
Want to know more about identity verification for your business?

 Explore Now
Explore Now













