Kaseya Ransomware Attack – How to Protect Your Organization from Cyber Risks

Did you know that by 2021, a ransomware attack is projected to occur every 11 seconds, costing companies approximately USD 20 billion?
A single ransomware attack can halt business operations for weeks, tarnish a company’s reputation, and pave the way for future data breaches. Such an attack can lead to identity theft, account takeovers, and other disastrous consequences. As Kaseya recovers from the massive REvil ransomware attack after 10 days of no business, some precautionary measures that can prevent such cyber risks have come into the spotlight.
What is a Ransomware Attack?
A ransomware attack is a kind of malicious software (malware) that can block access to confidential data or a computer server by encrypting it. Usually, the victim is threatened to pay a ransom fee to the criminal within a deadline. If the victim fails to pay on time, the data is deleted forever. Generally, ransomware is launched through a phishing email.
Kaseya Ransomware Attack, Explained
Kaseya, an IT automation software provider, offers services for MSPs (Managed Service Providers). VSA is among the world’s most popular software for MSPs that delivers Remote Monitoring and Management (RMM) services. On July 2, 2021, the Kaseya VSA software reported a massive ransomware attack that hit approximately 60 MSPs.
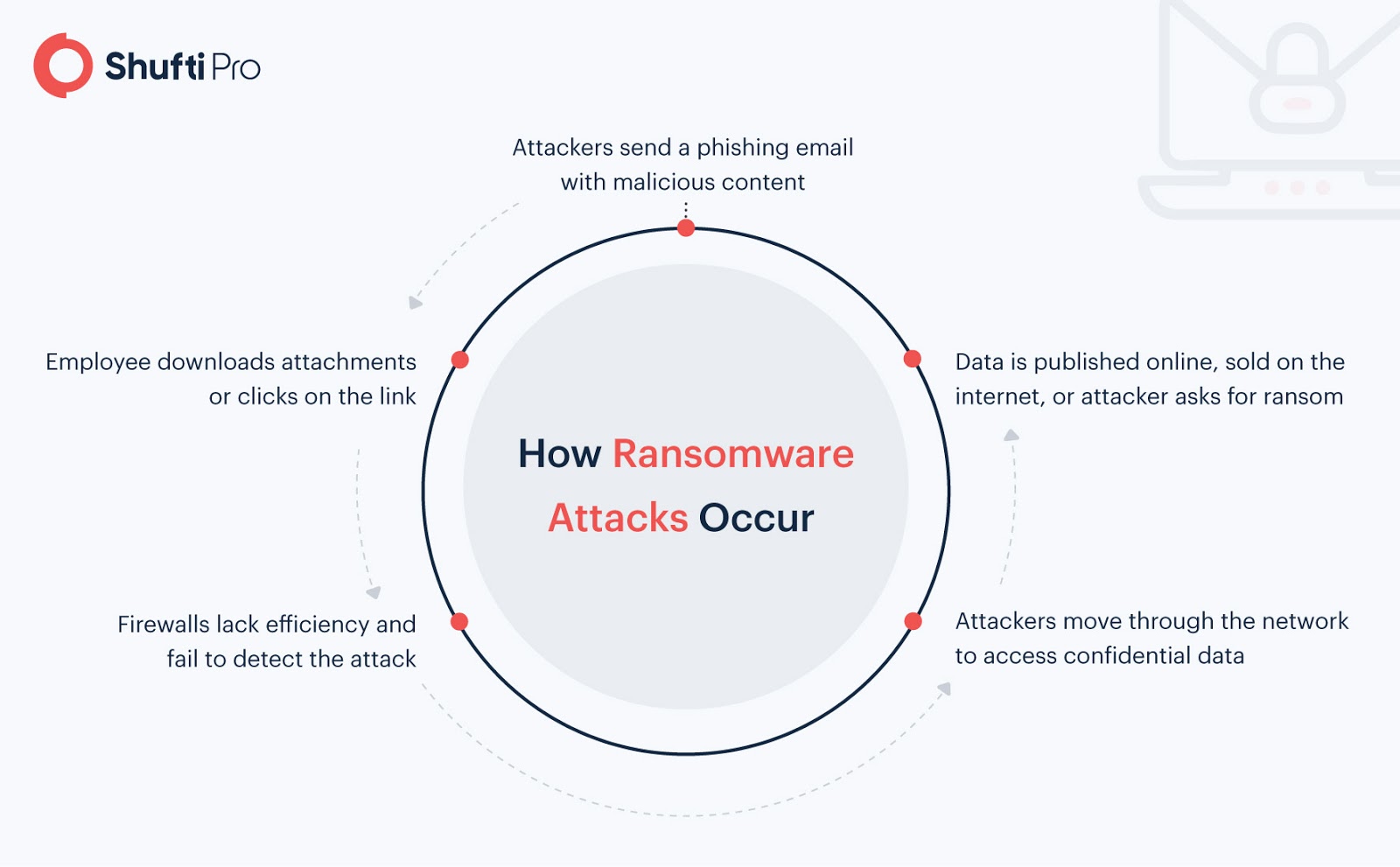
Initially, it was thought that Kaseya itself might have been compromised in the same way as the SolarWinds malware attack in December 2020. Instead, the attackers targeted a vulnerability in Kaseya’s VSA software, infecting 1,500+ small and medium-sized companies. According to the Huntress’ blog, the Russia-based criminal gang “REvil” first bypassed authentication to Kaseya’s VSA and then deployed malicious updates. In return, the gang demanded USD 70 billion in Bitcoin.
.@CISAgov is taking action to understand and address the supply-chain #ransomware attack against Kaseya VSA and the multiple #MSPs that employ VSA software. Review the Kaseya advisory and immediately follow their guidance to shutdown VSA servers: https://t.co/48QLkEm1eY
— US-CERT (@USCERT_gov) July 2, 2021
Could the Attack Have Been Avoided?
According to the latest update by Bloomberg, five former software engineers and developers had warned Kaseya leaders about the vulnerabilities in the systems. Examples of the vulnerabilities included outdated code, weak encryption and passwords, and a failure to meet basic cybersecurity requirements. Despite the concerns, the problems were never fully addressed, and new features were prioritized over fixing the existing issues.
Ransomware attacks such as this endanger the long-term sustainability of companies of all types and sizes. Below are some effective anti-ransomware strategies for safeguarding your business.
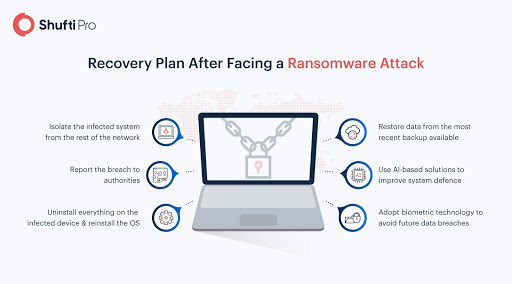
Best Practices for Preventing Ransomware Attacks
1- Set Up Firewalls
A firewall is a security system that monitors incoming and outgoing traffic based on predefined security rules. It examines the traffic for malware and other threats. Its capabilities can determine where a file is coming from, where it is headed, and other information about how it travelled. The information is then used that to ascertain whether the file contains ransomware.
Additionally, a next-generation firewall (NGFW) can also be deployed instead of using a traditional firewall for ransomware protection. NGFWs use deep packet inspection (DPI) to examine the contents of the file itself, hunting for ransomware, and then discarding any document that has it.
2- Use Technology Against Technology
While ransomware attacks can vary in type and intensity, all of them are deployed for one basic purpose – gaining ransom in return for stolen/blocked data. In case the ransom is not paid by the victim, the data is sold on the dark web, posted all over the internet, or used to commit other financial crimes. Money service businesses and data-sensitive companies need to restrict admin rights and limit access to servers by securing databases with AI-backed solutions.
Identity verification solutions, for instance, are commonly used by banks to verify the identity of every individual that attempts to access an account. These solutions use thousands of AI models to authenticate customers based on their official ID cards. By combining document verification with facial recognition technology, a fool-proof system is created for preventing fraudulent access, identity theft, account takeovers, and more.
Suggested Read: The Role of Artificial Intelligence in the Future Of Financial Fraud Detection
3- Establish a Security-focused Workplace Culture
To maintain compliance with KYC (Know Your Customer) regulations and stay protected from cyber risks, companies need to start with their staff. Provide them with more authority, educate them about regulatory compliance, and provide them with adequate training for detecting suspicious activities. Proper cybersecurity training combined with the latest fraud prevention technology can secure businesses against any form of cyberattack. Had the higher management at Kaseya taken swift action against the vulnerabilities detected by its employees, 1,500+ customers could have been saved from data compromise.
4- Conduct Regular Audits
Although businesses cannot completely eradicate cybersecurity threats, regular reviews and assessments can prevent billion-dollar losses stemming from cyber-attacks. In a joint statement by the FBI and CISA following the Kaseya ransomware attack, the company has been advised to conduct an audit of all admin accounts, particularly the accounts with access to remote management tools. This is a necessary step for ensuring that each account has a verified owner. Other audits highlighted by the regulators include a review of the disaster recovery plan, backup strategy, and vulnerability management processes.
#FBI Statement on Kaseya Ransomware Attack @CISAgov https://t.co/EHuplZdgAZ pic.twitter.com/hz9inabQgC
— FBI (@FBI) July 4, 2021
5- Enforce Multi-Factor Authentication (2FA)
Data-sensitive businesses such as financial institutions, software companies, and insurance firms must enforce two-factor authentication on every account as an added security measure and ransomware protection. Where most usernames and PIN codes can be compromised quickly by a malicious program, 2FA provides a significant increase in security for sensitive business data. The FBI backs this strategy for preventing account breaches arising from ransomware attacks by stating that every customer must implement 2FA on the accounts that are under the control of the organization.
With 65% of businesses allowing their employees to access company applications from personal, unmanaged devices, a simple step in the form of 2FA can save you from future catastrophes.
Suggested Read: Phishing Attacks and the Role of Two-Factor Authentication
How Can Shufti Help?
Shufti’s two-factor authentication prevents malicious actors from gaining access to personal and business accounts. With an accuracy rate of 98.67%, verification results are provided within five seconds. The process is deemed as a better alternative to traditional security methods, as it avoids phishing attacks and malware activity through a strong security hold. Need more information?
Talk to our experts or avail a 7-day free trial today!


























































![Anti-Money Laundering Compliance for Crypto Exchanges [2021 Update] Anti-Money Laundering Compliance for Crypto Exchanges [2021 Update]](https://shuftipro.com/wp-content/uploads/onsite-blog-Anti-Money-Laundering-Compliance-for-Crypto-Exchanges.jpg)