UK’s Digital Identity Framework – Cornerstone of Reliable ID
In today’s technology-driven era, digital identity is becoming inevitable. Physical interactions may not seem a safe option especially when the COVID is in full swing. Individuals and businesses are moving towards the digital space to keep up with social distancing practices as well as to adopt smart and efficient ways of identity verification. Recently, there has been a lot of debate around the UK’s Digital Identity Trust Framework, and for all the right reasons. The law is an important development towards how digital identities are dealt with in the UK.
What is Digital Identity Framework by the UK?
The UK’s trust framework is a list of detailed guidelines on how a reliable identity verification should look like. It sets forth rules for service providers to create, manage and recover digital identity accounts and that services are accessible and inclusive at all times.
A Framework to Govern the Digital Landscape
The UK government in February this year published an official document named “The UK Digital Identity and Attributes Trust Framework” that set forth guidelines for entities that create and use digital identities of end-users. Companies that follow these rules are granted a special ‘trust mark’ that guarantees their reputation as a trustworthy service provider in the public. The framework is created in collaboration with different public and private organizations to come up with effective principles for digital identity.

Digital Identity
As per the framework, digital identity is a representation of an individual in the digital space that allows them to prove their identity during online transactions and interactions. Below are some types of digital identities that can be created under the law:
- A digital wallet that stores pieces of trusted information – also called attributes – related to the user. The individual gets to decide whom to disclose their personal data and at which time. Digital wallets consist of details like full name, date of birth, and the right to work or reside.
- A digital identity that allows authentication in the form of an online product or service. One example of this is e-commerce stores requesting buyers to verify their age before they buy age-restricted products online. In this regard, customers only need to sign in with the identity verification service that automatically authorizes their age of consent and identity information, keeping intact data protection standards.
Attributes
The Trusted Framework defines attributes as fragments of information that give details about a certain individual or entity. When combined, attributes form a complete digital identity that can be used to authenticate digital transactions. Attributes may correspond to someone’s health condition, bank credit or even a company registration number. Some examples of attributes could be the age of an individual, residential address or ZIP/postal code, etc.
Guidelines for Participating Entities
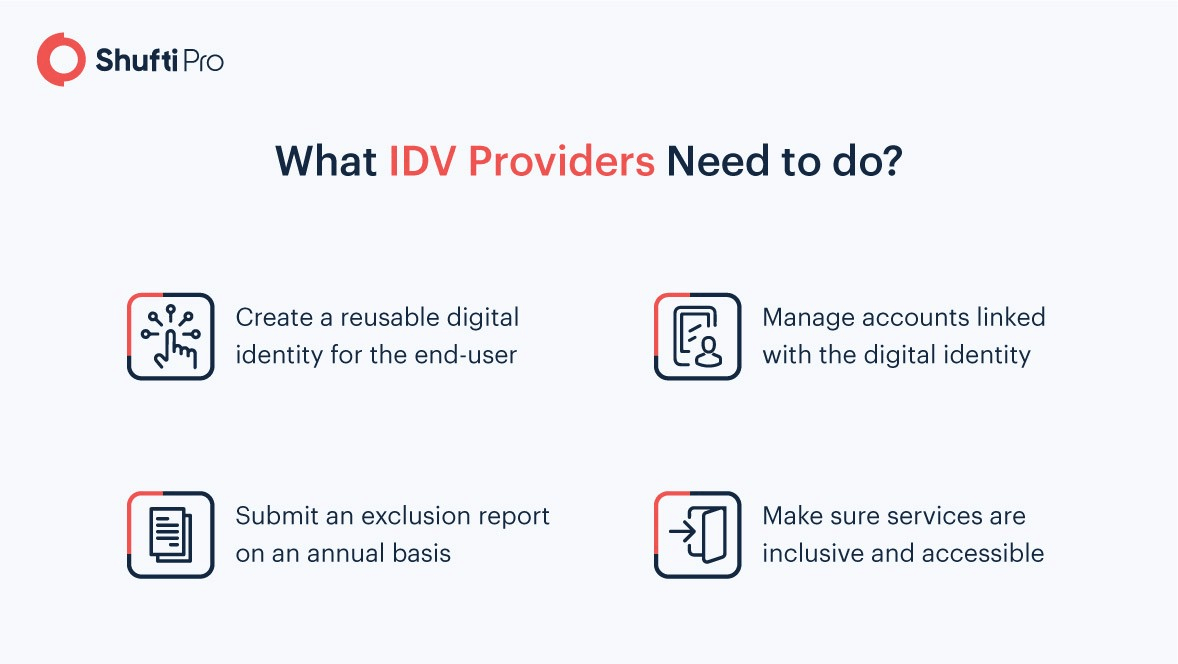
Entities that develop products or offer services that deal with digital identity are allowed to participate in the Digital Identity and Attributes Trust Framework. Individual organizations, as well as those who are part of an identity verification scheme, are required to perform the following roles, each one of which is related to a different set of responsibilities.
Data Protection and Minimization
Digital Identity Trust Framework incorporates data protection standards that are a mandatory requirement for identity and attribute service providers when they develop products and services. Having these measures in place ensures users have control over what personal information is used to create the digital identity. Moreover, they can better manage their attributes and decide which organizations have access and sharing rights to their data.
As per the framework policies, users have the right to only share information that is necessary and restrict access to the rest of it. Data minimization standards are based on the “right to see personal data” defined under the GDPR. An example of this kind of data sharing is when a user visits an age-limited platform, and they need to provide details for age verification. Using the digital identity, users can verify they are above the legal age limit without having to provide any necessary information.
Keeping up with Privacy Protocols
The trust framework requires participating entities to following two privacy compliance standards that are:
- ISO/IEC 27701:2019 is a privacy extension to ISO/IEC 27001 that highlights access control rights for Personally Identifiable Information (PII) controllers and processors to reduce privacy risks for consumers. This regulation is chartered by the International Organization of Standardisation.
- The BS 10012:2017 by British Standards Organisation is a framework for service providers to develop personal information management systems.
Apart from these, the Digital Identity Trust Framework directs compliant entities to create their own privacy compliance infrastructure, appoint a Data Protection Officer (DPO), develop a policy for data protection, and also formulate a process for Data Protection Impact Assessment (DPIA).
User Consent & Agreement
While accessing an individual’s digital identity, enterprises must have a lawful basis for how the information will be used. Consent is mandatory after making users aware of the data sharing and accessibility terms and conditions. The framework limits service providers to use personally identifiable information for marketing purposes. Data subjects – identifiable natural persons according to GDPR – also have the right to update or delete attributes corresponding to their digital identity as part of their agreement with the digital identity service provider.
Granting Access Rights
According to the guidelines, participating organizations must develop a mechanism through which their clients can know what part of personal information is accessed, shared and used for which purposes. The data should be up-to-date and free of errors not leading to any ambiguity in the digital identity of the end-user.
Data Protection Officer
Digital Identity and Attributes Trust Framework require organizations to designate an official Data Protection Officer (DPO). The responsibilities of the DPO include ensuring requirements listed under the UK’s GDPR Article 39. Moreover, creating a data protection process is also necessary to guarantee proper regulatory compliance with the ISO/IEC 29100 standard.
Key Takeaways
- Digital Identity Trust Framework in the UK regulates how identity service providers process digitally available personal data of individuals
- The framework defines digital identity as a collection of attributes – pieces of user information – that allows individuals to interact in the online space
- Participating entities under the framework must ensure data protection and privacy standards, appoint a DPO and obtain user consent and offer inclusive and accessible services






























![AUSTRAC’s ML/TF Risk Assessment Report on Major Banks [Part 1] AUSTRAC’s ML/TF Risk Assessment Report on Major Banks [Part 1]](https://shuftipro.com/wp-content/uploads/aust.png)






![A Brief Overview of the Cryptocurrency Landscape in the US and Canada [2022] A Brief Overview of the Cryptocurrency Landscape in the US and Canada [2022]](https://shuftipro.com/wp-content/uploads/crypto-cureency-lanscape.png)


































