Telehealth Services and Sophisticated Crimes – How Shufti Can Help Health Centers

The speed of innovation has never been faster. Re-emerging from a global pandemic, businesses of all sizes, across all industries and in every region across the globe have focused their attention on how to perfectly meet the ever-evolving demands of customers instantly and at a large scale. Companies launched digital payment systems, omnichannel options and contactless services to meet customers’ needs. However, no technology accelerated as quickly during the past recent years as that of telehealth. Although it’s not new, advances in video communication applications, smart gadgets availability and internet access are diversifying the use cases.
Strong continued uptake, increased customer satisfaction, and heavy investment into the telehealth industry contribute to helping this sector grow. While these services have come up with various opportunities that are favourable for both criminals as well as legit patients. With the increase in telehealth services crimes including data theft, patient identity theft and false insurance claims are on the rise. However, the growth of this industry is quite impressive, and it seems that these services are here to stay regardless of surging crimes.
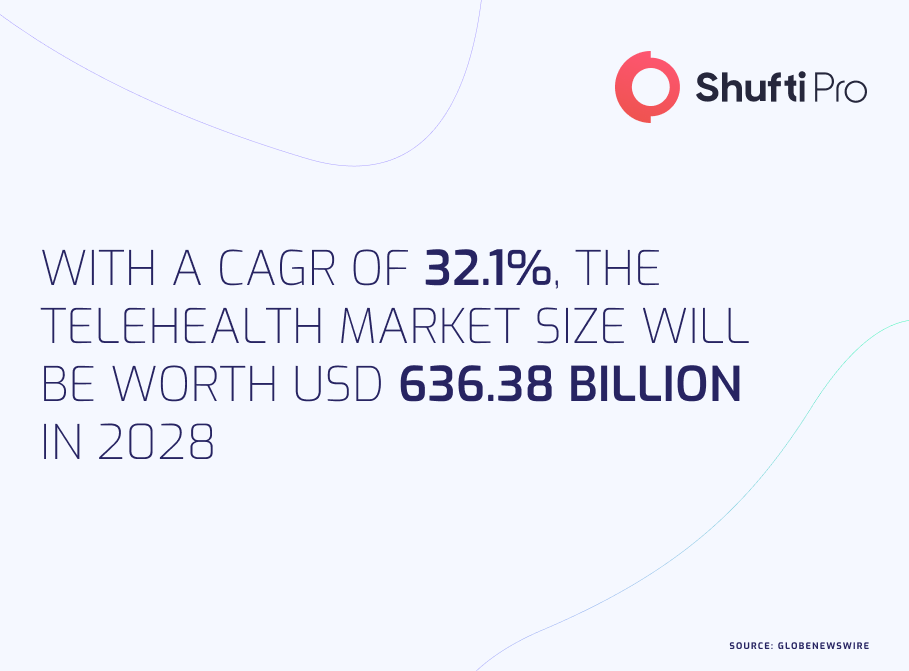
The Telehealth Era – A New Beginning
Contrary to what many people around the world think, digital healthcare, also known as telehealth, is a growing medicare service and much more than a cheap virtual knockoff of traditional care. When used properly, it enhances the patient experience and reduces the cost. It has also made health services accessible to the 89% of adults in the US and 78% globally who had hands-on smartphones, including the people living in medically underserved communities.
However, in 2020 the usage of telehealth services was at its peak, during the first wave of coronavirus when it accounted for 69% of doctor-patient interactions. Similar patterns have also been witnessed across Europe and Asia over the past two years, provoking governments to take appropriate steps to back telehealth services. In this regard, the EU Parliament and European Council have launched the EU4 Health program to prompt the sharing of patient digital medicare records, e-prescriptions and telehealth in general. On another hand, Saudi Arabia is also taking initiatives to implement strategies that include mobile applications and a network of highly specialized professionals along with medicare centres with primary care in remote areas.
But in many jurisdictions, telehealth service providers seem to face challenges including regulations, payment restrictions, and patient acceptance. Therefore, any country that seeks to enhance its health services, increase access and lower the cost should develop a telehealth-friendly environment, not contacting digital medicare.
Sophisticated Crimes Related to TeleHealth
The increase in the growth of telehealth services is predicted to continue. With the rapid surge in patients as well as telehealth service providers, combined with ineffective laws has paved the way for criminals to come up with bogus schemes and a series of crimes. Companies have been identified as charging patients and insurers consultations that barely last for minutes over the call or by glitching video conferences. According to the US Department of Health and Human Services studies, there has been a 63-fold increase in telehealth appointments and use among patients with Medicare coverage.
Telehealth fraud is the new iteration of the healthcare scams and abuse of publicly funded systems. However, before the coronavirus outbreak, telehealth services were very rare, and the activities were stringently monitored. But, now as the services are getting common, it’s becoming challenging for the healthcare service providers to closely assess the operations, thus, criminals are exploiting systems at large.
For instance, Florida-based businesswomen signed a plea agreement to resolve criminal allegations and civil claims for involvement in a $400 million false claim fraud scheme. The alleged criminal and her co-conspirators created a series of DME supply companies with false information. They then submitted more than $400 million in illegal DME claims to official government programs and stated that the higher portion of the claims was due to the avail of telehealth services, but in reality, they were bribing health professionals to approve claims. However, the doctors had no virtual interaction with the criminals.
In another case, the owner of the Orlando telemarketing call centre was alleged to be involved in a $2.8 million kickback scheme in which bogus telehealth services were endorsed. According to the trials, the alleged entity was using the call centre to manipulate healthcare beneficiaries and falsely telling them telehealth services covered high-cost cancer screening and genetic testing. Each service cost $6000. However, if the victims get fantasized and agree to take tests, the call centre owner pays bribes and kickbacks to the laboratories to obtain fake results.
Global Telehealth Regulation To Secure Services
China
The use of telehealth services is legal in china. It’s termed internet plus healthcare in the country. Various administrative laws were promoted by the PRC National Health Commission and the National Administration of Traditional Chinese Medicine to support telehealth services. The rules include;
- Effective measures for internet diagnosis and treatment
- Administrative measures for internet hospitals
- Appropriate practices for remote medical services
China has yet to implement privacy and data protection laws that apply particularly to telehealth services. According to the rules, medical facility centers shall comply with all the relevant regulations and policies associated with information security and confidentiality of healthcare data. These include;
- Cyber Security Law
- Regulations of the PRC on Administration of Human Genetic Resources
- Administrative Measures for Health-Related Information
- Good Administrative Practice for Electronic Medical Records
However, according to the State Council’s recommendation published on July 12, 2020, the legal scope of internet health services shall be further expanded on the preliminary condition to ensure the safety of patients as well as the quality of services.
Indonesia
Like China, virtual medical services are permitted in Indonesia. Article 1 of the Regulation of Minister of Health of the Republic Indonesia Number 20 of 2019 regarding the Organization of Telemedicine Services through Health Service Facilities states telehealth as the provision of remote service by medicare professionals by using patient information and communication technologies.
Telehealth is regulated under the following regulations:
- Circular Letter of the Minister of Health No. 2 of 2020
- Indonesian Doctors Association Regulation No. 74 of 2020
How Shufti Can Help
Shufti’s state-of-the-art digital identity verification service is a viable option for telehealth service providers. By employing Shufti’s solution businesses can verify patients before getting them onboard with 98.67% accuracy in less than a second. Other than this, the service providers can stay put with the regulatory obligation and can avoid hefty fines.
Want to know more about robust identity verification services?

 Explore Now
Explore Now













