Protect Your Business Against Identity Theft with Face ID Check

The efficacy of biometric authentication becomes questionable in the face of facial ID checks. It’s critical to understand the limitations of this security measure and to stay vigilant for any potential identity theft or fraud attempts. Businesses can use a scan or a photo of a person’s face for a face ID check, which helps identify or validate that person’s identification. The most popular method for completing this process is to use the person’s submitted photo or a selfie. Nonetheless, with the face ID check, faces can be recognised in videos and CCTV views.
By 2030, the face ID check market is predicted to be valued at $16.74 billion, a rise of more than 125% from 2020. Learn everything there is to know about the face ID check, including what they are, how they work, use cases, advantages for businesses, and why they are crucial to preventing identity theft. Furthermore, comprehends the stages of the face ID check, their future, and the rationale behind their use by companies.
What is a Face ID Check?
One type of biometric security is a face ID check. Voice, fingerprint, and iris recognition are examples of further biometric software. Face ID check is typically connected to law enforcement and security. Face ID check is undoubtedly helpful from a security standpoint, but companies can also use the technology to check employee attendance, enhance customer experiences in stores, and ensure compliance with anti-money laundering laws.
What is Identity Theft?
Identity theft is the act of taking someone else’s data or sensitive information and using it for their own gain. According to the National Council on Identity Theft Protection, the number of identity theft reports has increased dramatically in the last several years, from $3.43 million in 2019 to $5.74 million in 2021. Identity theft comes in a variety of ways, and each one has a unique impact on people and companies.

How to Prevent Identity Theft with Face Check ID
Identity theft can be prevented with face check ID solutions. It includes:
Facial Recognition
KYC verification is made possible by the use of a face ID check solution. A face scan is used to create models of the subject, which are then saved as machine-learning data and compared to the images stored in databases. It eliminates the need for ID cards and the need for laborious identification processes. It is, therefore, among the more widely used biometric services.
The increased likelihood of fraud, identity theft, and data hacking has coincided with an increase in internet connectivity; because of this, organisations, governments, and people worldwide rely on enhanced face ID check to protect private data and promote confidence in online interaction.
Facial recognition technology is critical to legal compliance in industries with strict KYC regulations, such as financial institutions, fintech, banking, insurance, and e-commerce. It also facilitates identity theft prevention, improves personal information security, and guarantees the dependability of online systems and services.
Biometric Verification
Biometrics are the distinct physical and behavioural characteristics of an individual that allow organisations or law enforcement to recognise them. Biological markers are typically biometrics, which are used to identify an individual and include voice, eyes, iris, veins, face impressions, fingerprints, and DNA. However, behavioural traits such as lip motions, eye movements, nose size, and keystrokes on a device are also employed in biometric identification. Making security systems impenetrable whilst protecting people’s records and personally identifiable information against identity theft, unauthorised access, and data breaches is the primary goal of utilising biometrics.
Face ID Check Use Cases
Many industries and sectors use the face ID check to mitigate predicate crimes. A few industries include:
Law Enforcement
Law enforcement agencies utilise the face ID check around the United States. Police officers typically do this by getting suspects’ mug shots and comparing them to federal, state, and local facial recognition databases. After a suspect’s photo is taken, it is stored in databases and is examined each time law enforcement does a criminal search.
Nevertheless, face ID check is also used by law enforcement to recognise individuals in CCTV footage or to identify suspects. Law enforcement officers also utilise the face ID check in a similar manner to locate individuals who have gone missing and recognise victims of human trafficking. Law enforcement can be notified as soon as a missing person is identified by technology anywhere in the world if their information is stored in a database.
Airports and Border Control
At airports, face check ID is now a common occurrence. With the introduction of biometric passports, travellers can now bypass the lengthy lines at passport check and enter through an electronic passport control gate. By removing human errors, these gates not only improve passenger convenience but also enhance security.
A report revealed that 97% of travellers are expected to utilise facial recognition technology by next year. Additionally, it’s anticipated that comparable technologies will be utilised in the upcoming years to improve security at major concerts and athletic events.
Reducing Retail Crime
To lower retail crime, store owners can also implement a face ID check. This is due to the technology’s ability to detect the entry of known shoplifters, organised retail criminals, and those with a history of fraud and scams. When customers who might pose a threat come, loss prevention and retail security specialists can be alerted using photo verification that matches an individual’s photo to criminal information databases.
Improving the Retail Experience
The Face ID check can also be utilised to enhance the shopping experience for customers in a store. Experts predict that the face ID check will be able to identify consumers, recommend products based on their past purchases, and navigate them around the store in the next few years, even though it is not currently generally accessible. After making their selections, customers can bypass any long lines by paying using biometric authentication.
Banking Operations
Face identification technology has several applications in the financial services industry, including transaction enabling, KYC verification, and data security. Banks and other financial service providers may develop safe systems and keep fraudsters out by reducing their reliance on passcodes and passwords. Financial institutions can also make sure they fulfil all KYC and AML requirements by including verification and biometric facial ID procedures during onboarding.
When banks implement a face ID check, they eliminate the possibility of password breaches. Furthermore, liveness detection, a method for figuring out if the source of a biometric sample is a real person or a fake representation, will stop hackers from exploiting their photo database, even if they manage to copy it.
Healthcare
Biometric authentication techniques are utilised in hospitals and other healthcare settings to improve patient care. This is due to the fact that face ID check can be used to expedite patient registration, access patient records, identify particular hereditary disorders, and even sense emotion and suffering in patients. Furthermore, some businesses are even creating apps that utilise the face ID check to make sure users take their prescription drugs as directed.
Monitoring the Attendance of Employees or Students
Face ID check is being used by educational institutions to make sure that students are not missing class. Additionally, this technology stops students from using fake accounts or logging in on another pupil’s behalf.
Some workplaces use this technology, too, to track employee attendance in real time. This technology is crucial when sensitive information is stored at work. The Face ID check can be used to control access to these storage areas so employers can track when and who accessed them.
Monitoring Gambling Addictions
Lastly, casinos may also utilise face ID verification to guarantee compliance and safeguard patrons. It is difficult for human employees to keep an eye on and identify people who are moving throughout the casino. But on a busy casino floor, they can keep an eye on every move.
It can, therefore, be used to assist staff members in identifying individuals who are listed on self-exclusion lists or who are registered as gambling addicts. In addition to helping these people, the technology can benefit the casino owner, who risks paying large fines if it is discovered that they permitted people on self-exclusion lists to keep playing.
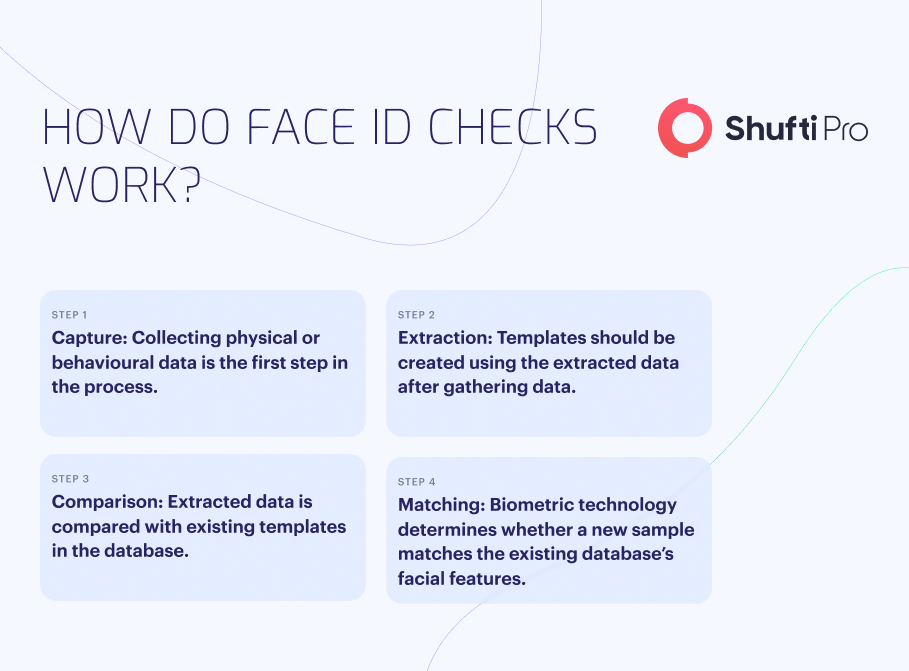
Benefits of Face Check ID
Face Check ID has numerous benefits, including but not limited to the following:
Increased Security
Face ID checks can assist law enforcement in identifying terrorists and other offenders. Face ID checks can be applied to personal surveillance cameras and gadgets as a security measure.
Low Criminality Rate
Face check ID makes tracking down trespassers, criminals, and burglars easier. Even knowing that face ID checks are in place can discourage crime, especially minor crimes. Businesses can replace passwords for computer access with face ID checks. Ideally, unlike passwords, there is nothing on the technology that can be stolen or altered.
Removing Bias from Stop and Search
Police face criticism from the public about unwarranted stops and searches; the face ID check could help with this. Face ID check has the ability to lessen bias and the number of stops and searches of law-abiding persons by using an automated procedure to identify suspects among crowds rather than a human one.
Increased Practicality
Customers will be able to pay at stores with their faces instead of taking out credit cards or cash as the technology spreads. This might shorten checkout wait times, unnecessary delays, and long-standing queues. The face check ID provides a rapid, automatic, and smooth verification procedure as they don’t involve touch, unlike fingerprinting or other security measures.
Faster Processing
The businesses that utilise the face ID check benefit from the fact that identifying a face simply takes a few seconds. In these days of sophisticated hacking technology and cyberattacks, businesses want verification solutions that are quick and safe. Verifying someone’s identity quickly and effectively is made possible by the face ID check.
Combining Technologies
The majority of face ID checks work with the majority of security programmes. It is quite simple to incorporate. This reduces the amount of extra money needed to put it into practice, reduces human effort, and helps maintain compliance.
Why Should Businesses Adopt Face ID Check?
A survey found that over 65% of consumers already knew what biometrics were. People have become accustomed to the process, especially with regard to face ID checks or facial recognition technology. Consumers only need to hold still for a brief period of time for the webcam or camera on their smartphone to complete the face ID check process.
Although no technology is 100% safe from hackers, face ID check is a challenging method to circumvent. Including liveness checks and anti-spoofing makes the process far more complex than simply obtaining a password, discouraging fraudsters. According to a report, 81% of hacking-related breaches used weak or stolen passwords.
Companies can use a face ID check solution to make sure that only permitted individuals are creating and using their accounts, removing the need for passwords. An additional advantage of face check ID is that businesses can reuse the biometric data they obtained during enrollment, such as a verified 3D face map, for further authentication. This suggests that a single solution may handle identity and continuous user verification.
Without a doubt, none of the technologies is risk-free. The amount of data being used in the face ID check may provide handling and storage issues. Even with great progress, face check ID remains unsatisfactory when faces are viewed from diverse camera angles or when obstacles such as hats are present. There have also been privacy-related issues, particularly in the government and retail industries. For this reason, rather than being used for verification, face ID checks should be used with multi-factor approaches (like facial authentication, facial recognition, liveness detection, and biometric authentication) to enhance user access.

Future of Face ID Checks
Financial crimes, identity theft, and digital fraud are here to stay, and firms must take the necessary precautions to both neutralise and reduce their effects. Businesses don’t need to search much further to achieve this goal because face ID checks are methodically built to protect digital identities, consumer data, and corporate operations from new threats and increasing risks. It is true that in this digital age, traditional authentication methods such as passwords, pins, and tokens are no longer practical. Face ID check is becoming more widely employed globally in a variety of businesses. Whilst privacy concerns may cause adoption to lag in some areas, adoption is currently accelerating globally and revolutionising corporate practices. Without any doubt, the adoption of this face ID check will be widespread, and all industries will implement it to verify users, protect identities, and stay protected against predicate crimes.
How can Shufti Help?
To help businesses combat fraud, Shufti, an all-encompassing kyc verification service provider, provides face recognition, liveness detection, and facial biometric recognition, as well as cutting-edge, foolproof face ID check solutions. Our system possesses accuracy and reliability due to the flawless fusion of biometric technology, machine learning algorithms, and artificial intelligence. Our services are available in 240+ countries and territories, and we support over 10,000 ID documents in 150+ languages, making us the ideal choice for international businesses without concerns about national and international compliance. Our solutions are efficient and maintain compliance requirements worldwide.
Confused about how to prevent identity theft with face ID checks whilst maintaining national and global compliance requirements?