Customer Identification Programme (CIP) vs Know Your Customer (KYC) | What’s the Difference?

Often, people confuse CIP and KYC and think both are the same. Customer Identification Programme(CIP) and Know Your Customer KYC solutions are two essential terms in the identity verification field, and it’s critical that businesses understand the regulatory requirements and how these solutions enable compliance to be met. The Financial Times reported that KYC and CIP fines rose 50% last year, with banks charged almost $5 billion for Money Laundering infractions, sanctions breaches, and Know Your Customer failures. Nonetheless, there is a substantial difference between both of them. CIP is a regulatory requirement by the USA Patriot Act, whilst Know Your Customer KYC isn’t mandatory. Understand what a Customer Identification Programme and Know Your Customer is, along with their importance, requirements, and the difference between CIP and KYC.
What is CIP?
The Customer Identification Programme, or the CIP process, is the US regulatory requirement. CIP compliance is a compulsory regulation for businesses operating in the US that requires firms to verify their customers before onboarding them or before having any transaction or business operations. CIP became effective in the US after the US Patriot Act in 2003 to combat financial risks, including terrorist financing and money laundering.
According to the US Patriot Act, all financial institutions, including banks, investment firms, brokerage, digital asset providers, credit unions, saving associations, and a few non-regulated banks, as well as other organisations in the United States. On the contrary, the Bank Secrecy Act (BSA) regulation in 1970 in the US also mandates businesses to comply with the CIP. The main aim of BSA-CIP was to help government and financial institutions prevent terrorist financing, money laundering, and other illegal financial activities. The customer identification programme requires businesses to validate their identity.
What is KYC?
KYC verification is a process businesses employ before onboarding clients or forming any ties or associations with other businesses. KYC compliance is required by many regulatory bodies around the globe, including the Financial Action Task Force (FATF) and the EU’s Anti-Money Language Directives (AMLDs), to ensure secure business operations worldwide.
KYC laws are regulatory requirements imposed on businesses by regulatory bodies. Initially, KYC was required as a part of the Money laundering requirement to mitigate financial crimes. The primary objective of KYC is to validate the identity of businesses and ensure that businesses are exactly who they claim they are. The KYC screening process ensures that financial institutions have all the information about their customers, making it easy for them to assess the risk each individual possesses in order to combat money laundering and terrorist financing. KYC solutions require businesses to gather all the relevant information related to the individuals associated and continuously monitor them to indicate if businesses have engaged in any fraudulent activities.
The CIP Rule: What’s in it for Businesses?
The customer identification programme rule consists of 6 fundamentals as per the guidelines given by the Federal Deposit Insurance Corporation (FDIC):
- Establishment of a comprehensive CIP written programme.
- Collecting necessary documents, including name, date of birth, address, and government-issued personal identification number, by the authorised personnel.
- Implementing identity verification procedures.
- Maintaining customer data records and continuously updating them.
- Checking customers against government, private, and trusted data sources.
- Updating customers about the CIP requirements and maintaining the record.
Which Entities are Subject to CIP?
According to the CIP Rule, any company that falls under the Bank Secrecy Act (BSA) must abide by its regulations in the United States. Some well-known instances include:
- Banks
- Credit unions
- Brokerage firms
- Savings associations
- Cryptocurrency exchanges
- Lenders
- Payment service providers
- Gambling platforms
- Investment firms
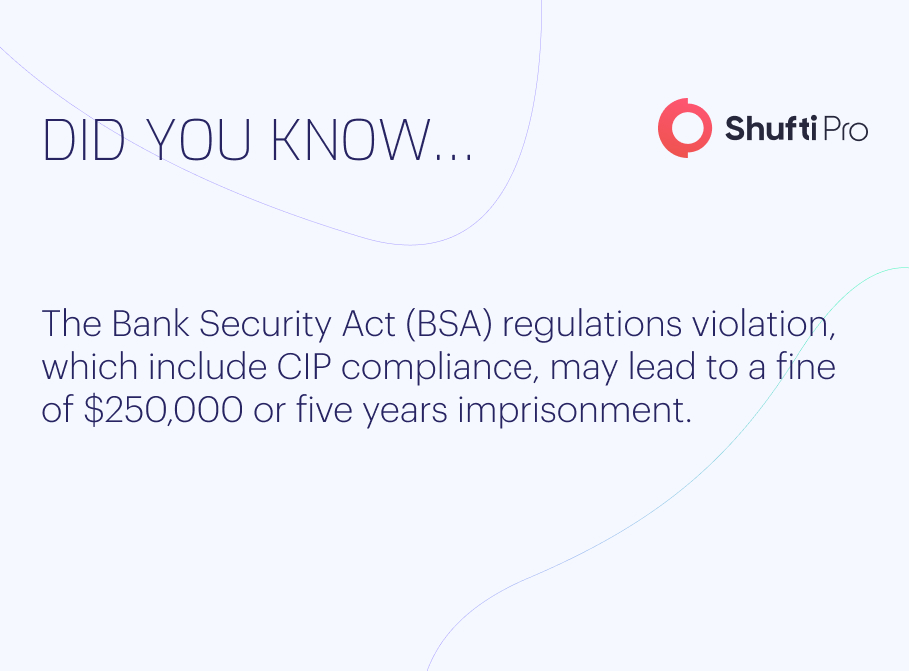
Violations of BSA requirements, including CIP compliance, can result in heavy penalties or even detention for up to five years.
KYC Requirement
KYC standards were implemented by FINRA Rule 2090. Despite the fact that these standards vary by country, KYC generally includes three fundamental risk-based measures aimed at avoiding money laundering, identity theft, and other sorts of financial crimes. The 3 main kyc requirements are as follows:
- Creating a customer identification programme that collects and verifies important identifying information such as a person’s name, date of birth, mailing address, and identity number.
- Conducting Customer Due Diligence (CDD), which entails evaluating customer risk by verifying customer identities, creating risk profiles, and keeping track of both customers and their transactions on an ongoing basis.
- Customers are being monitored, and any suspicious activity is being reported to FinCEN and other law enforcement authorities.
CIP Requirement
The Bank Secrecy Act of 1970 (BSA) mandates financial institutions to work with US government authorities to identify and avoid money laundering. Adherence with BSA compliance requires financial institutions to keep up with a Customer Identification Programme (CIP) to demonstrate that new customers’ identities have been confirmed upon account opening.
With the historic signing of the USA Patriot Act in 2001, the present standards for CIP were written into law, mandating banks, savings organisations, credit unions, and other non-federally governed banks to have a CIP suitable to their size and operation. Maintaining an efficient CIP is also a crucial component of adhering to the BSA’s initial provisions. The CIP regulation requires a financial institution to verify the legitimacy of each “customer,” defined broadly as “a person who creates a new account,” and must be able to “form a reasonable belief that it knows the true identity of each customer.”
KYC vs CIP
CIP is a required component of the BSA-mandated AML compliance programme. It is also mostly used by US-based financial institutions, whereas KYC is a collection of regulatory standards used on a global scale by many businesses.
Nevertheless, KYC can cover all aspects of CIP, as well as CDD and other ongoing procedures. CIP and KYC differ primarily in their primary objective and depth within the broader world of customer verification:
CIP (Customer Identification Program)
- CIP is largely concerned with confirming the customer’s identification.
- It is involved with authenticating consumers’ genuine identities, frequently during the account opening process.
- CIP contributes to a reasonable belief that the corporation is aware of the customer’s true identity.
KYC (Know Your Customer)
- KYC has a broader scope that includes not only identification verification but also assessing the customer’s entire risk.
- It aids in the collection and analysis of a variety of data about the consumer, such as their identification, transactions, and risk profile.
- KYC seeks to understand the consumer better, analyse any risks, and make sure the organisation can handle and track the client relationship over time.
Incorporating CIP into KYC
KYC programs commonly include CIP as part of their processes. As mentioned, KYC standards are designed to protect financial institutions against fraud, corruption, theft, terrorist financing, identity theft, and money laundering. An effective KYC programme has three main components:
CIP: The gathering and verification of customer-provided information in order to create an informed opinion that the customer is real and is exactly who they claim to be.
Customer Due Diligence (CDD): Assuring a customer’s trustworthiness and suitability for doing business with. Multiple levels of the CDD process should be used depending on the customer’s risk and the kinds of transactions they want to conduct. For instance, if a customer does a transaction of $100, that would require a simple form of CDD that is SDD, but the amount exceeding the limit will require a greater EDD in return.
Ongoing Monitoring: The first two elements of a KYC programme normally protect financial organisations at the beginning of the account opening procedure but do not protect against changes once a customer has been established. In order to make sure that a client does not appear on a government sanctions list or exhibit odd behavior, regular re-evaluations are required. Whilst regular re-screening may be suitable in some instances, the optimum practice is to have ongoing tracking so that any shifts may be detected in real-time.
How Can Shufti Help?
Compliance with CIP or KYC is not only a requirement, but it is becoming more difficult as transactions transition to digital platforms. In a digital landscape, financial organisations must not only accurately evaluate new consumers, but they must also do it without putting friction and unnecessary delays into their onboarding procedures.
Shufti KYC can help you automate CIP and KYC programmes, allowing businesses to automatically accept up to 99.97% of consumers whilst meeting compliance standards. Shufti provides powerful CIP and KYC services that expedite clients in real-time. Our sophisticated CIP and KYC system is trusted worldwide for instantly confirming identities and assisting businesses in complying with global requirements.
Still confused about whether to choose CIP or KYC based on domestic and global mandatory requirements?






















![Know your patient process explained [Under the GPhC’s guideline] Know your patient process explained [Under the GPhC’s guideline]](https://shuftipro.com/wp-content/uploads/know-your-patient-2.png)
















































