A guide to choosing the right ‘Digital Identity Verification Solution’

Living in the digital era, everything is now just a click away. From customer onboarding to online payments, personal information is what we consider the most valuable resource. Businesses are striving hard to implement processes that will let users to efficiently perform their tasks in digital space. Identity verification is an emerging market in the digital sphere that is becoming a need for every digital business.
An increasing number of organizations are opting for digital customer verification solutions. But numerous challenges are waiting for them. What qualities to look for in identity verification solution? How to efficiently and securely connect users’ digital and physical identities in a convenient way?
We’ll cover these questions in our blog. The first section will cover the challenges of digitization followed by key considerations for selecting digital verification solutions. Finally, we’ll discuss the important features of an efficient ID verification solution.
Choosing the service-provider that brings transparency and security for the organisation is essential.
Digital Challenges laying a foundation of Identity verification
Digitization has become a necessity for every business. With this digital transformation comes the significant challenges for organisations. To address them while protecting the business from potential threats and frauds, enterprises are investing their resources more than before. The presence of an immense number of individuals in digital spaces is threatening itself. You never know the real identity and intention of an individual present online. That’s the reason why online identity verification is spiking in demand.
Although identity verification is not new, the incentives it offers are now enhanced. Trust is something that must be established between an organisation and a customer. With trust, comes efficiency and convenience. Undoubtedly, online businesses will always be under the radar of fraudsters and cybercriminals. There doesn’t exist any bulletproof solution yet that can fully deter fraudulent activities. Currently, the goal is to minimize these risks, if not prevent them fully.
Identity verification is the solution to overcome these hurdles. As digital identity becomes prevalent, extra layers of security checks are required to authenticate the user. However, with digitization, user expectations have become even more eminent when selecting the product or service. This conveys a clear indication for the companies to go an extra mile and incorporate identity verification solution that offers incentives beyond the traditional solutions.
Databases – the beginning of digital identity
Data is a goldmine for cybercriminals. The creation of databases by banks, government agencies and other private companies was another beginning of digital identity. With the advent of technologies such as big data, consumer information is the new currency in the digital world. This readily present information of users is the core driver for the increase in data breaches.
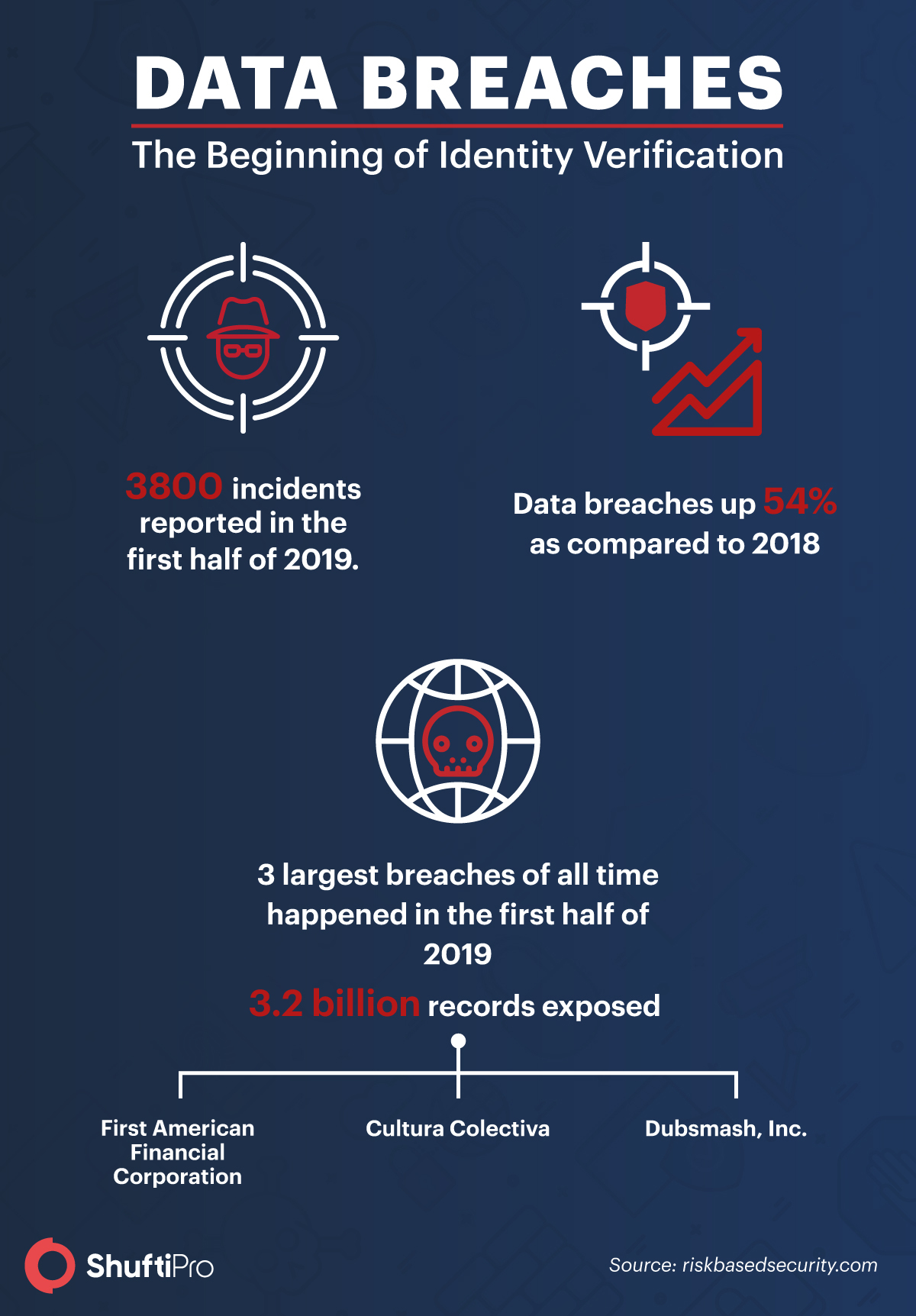
Online activities are emerging and the need to protect user data is crucial than ever. The rising trend of data breaches is forcing companies to raise trust in their digital services. According to the Risk-Based Security breach report, the business sector was responsible for 84.6% of records compromised in 2019. This urges companies to rush their identity verification.
Considerations for the company before selecting the solution
Ready to incorporate identity verification solution, but wait did you do your homework? You can’t just randomly select any solution and expect it to cater to your needs efficiently. There are some key points that must be taken into consideration before choosing the identity verification solution.
Evaluate your needs
It’s a well-understood fact that every use case requires a different level of user authentication and security. For instance, if your business needs a simple verification system that checks and the identity of people entering your office, more likely an attendance system, the simple biometric fingerprint verification will do the job. In this scenario, the enterprise won’t need an expensive solution with multiple checks.
Contrary to this, enterprises dealing with critical data such as banks, financial institutions, crypto firms, etc. require comprehensive identity verification solutions. The reason is mere customer authentication is not enough, KYC and AML regulations further oblige AML screening and cross-checking against multiple data sources. So, the first step before selecting the ID verification solution, be clear about your needs and business demands.
Analyse the process flow
What set of information do you need to verify the identity of your consumers? What services does your business require? What will be the steps involved in the verification process? These are some vital questions that businesses must answer when opting for the right verification solution. If your company only needs an identity document to verify the user’s identity then don’t include an extra facial recognition check.
This happens in case of the gaming industry, liquor stores, and age-restricted sites that only need identity verification service for age verification of their customers. Sometimes, companies make the biggest mistake of including unnecessary features in the process assuming it will improve the overall process. However, most of the time it turns out to be opposite, creating friction. Less is more! Your emphasis must be on what is actually needed and that’s the key to determine right services.
Tracking customer behaviour
Customer behaviour is a significant factor in the success of an enterprise. Businesses need to track customer behaviour in regard to omnichannel presence. It’s vital for a company to analyse whether consumers use mobiles or desktops to carry out their activities. At the planning phase, the right fit for every channel must be decided. The reason is every channel has unique characteristics and presents different challenges, for example, the responsiveness of solution on mobile.
So, whatever strategy, you’re planning to opt, mobile-first or desktop-first, ensure the process consistency and smooth customer interaction.
Balancing security and user experience
Authorising the user’s identity while ensuring the seamless user experience is a significant challenge companies encounter. The balance between user experience and security of the enterprise must be achieved. The incentives of the identity verification process are enormous, however, only in case of right use case and the appropriate solution. For instance, users are more likely to follow extensive ID checks while accessing bank accounts rather than a social media account.
Before selecting the solutions, it is vital for a business to analyse the worth of the service and how likely the users will adapt their processes – and of course the user flow. The identity verification solutions need to establish a certain threshold. For instance, while incorporating facial recognition service for ID verification, any match above the defined threshold must be accounted for a match.
It is essential to ensure that the defined threshold for ID verification is neither too low that will increase the risk of false positives and hence, security vulnerable, nor it is too high to reject the good match, ultimately affecting user experience. While incorporating the solution, make sure that every step provides great user experience while remaining secure. Because in the end, it’s all about the user journey and how likely they’ll complete the process.
Checklist for Identity verification solution
Once you have decided to integrate an online identity verification solution. The next step is to go through an identity verification solution market. Some features must be checked for efficient verification of customers. Here’s our checklist for features that need to be analysed while selecting the solution.

Global coverage
Mostly online IDV solutions offer coverage within the country only because of lack of access to country-specific information databases. Every country has its own laws and regulations and information availability also differs. Your customers can be from any part of the world and letting them go just because your vendor doesn’t offer global coverage is unsatisfactory.
Ensure that the selected verification service offers global coverage empowering you to verify ID documents of your customers from all over the world.
Real-time verification
Real-time verification is one of the essential features to look for in an identity verification solution. The ability to verify the user identity within seconds while they’re in the middle of registration has become an important factor to strike balance between security and customer experience. Delayed verification processes result in lost conversions.
Geolocation services
Online frauds are rising and enterprises need a solution that offers an extra layer of security to deter fraud in real-time. Geographical information, IP address, mobile & device specifications, timestamps, all these features formulate a strong foundation for the business to assess any potential risks.
Globally compliant solution
Is your selected IDV solution compliant with the relevant global regulations? The question that you must answer before implementing the identity verification process. Identity checks are well-known in organisations, still, many of them have to face severe legal penalties due to non-compliance with the regulations. KYC and AML regulations are becoming stringent. Select a solution that easily adapts the changing compliance requirements.
Legal enforceability
Is your service-provider following proper data security standards? You wouldn’t want your consumers’ data to go into wrong hands right? Ensure that the agreement between the company and the IDV solution provider is legally enforceable. Always know beforehand, what happens to the data once the customer decides to opt-out of the service. The best solution is the one that is compliant with GDPR and other consumers data protection laws.
Paperless process
To carry out the identity verification process, consent from the user is obligatory. But how to take consent from remote customers? Does the online IDV solution drop paper and wet signature process while digitally capturing the consent from the user? Look out for the solution that offers consent verification service to take and verify the consent from the user. It facilitates the enterprises to avoid any false defamation cases while staying compliant to the data protection regulations.
API and documentation availability
API docs are a valuable component of any solution. It allows you to deeply understand the solution, its flexibility and process flow, and evaluate the IDV provider. Comprehensive documentation presents clear requirements that you need to fulfil to build out an integration. Do check out the API of the IDV solution before integrating and if they are providing you with a free trial of the service then it’s a cherry on top.
Customised functions
What features do your businesses need? A simple biometric verification service or a complete IDV solution offering AML screening and document verification? Not every service provider will offer you a customised package. The best solution provider is the one who understands the business needs and requirements and accordingly offers the services.
Ensure that the selected verification service offers global coverage empowering you to verify ID documents of your customers from all over the world.
It all boils down to
With the advancement in technology, organisations are actively turning towards digital solutions to cater to the growing demands of customers and needs of the business. Identity verification is now mission-critical for business operations. Having a seamless verification process will not only incline the users to employ your services but will also benefit the organisation in the long run. The first impression goes a long way and that’s how Shufti’s identity verification solution is designed.
At Shufti, we ensure to achieve the best identity verification solution through hybrid technology of human and artificial intelligence. The IDV solution verifies people in real-time within 30-60 seconds and provides reliable proof of verification. Taking into consideration the unique expectations and requirements of the company, it offers a customised solution with pay as you go pricing feature. To sum up Shufti is one in all solution to cater your customer verification needs.
Have more questions on how Shufti can help you? Share your concerns with our team and get a solution as per your business needs!
Find more relevant resources:
A guide to choosing the right ‘Digital Identity Verification Solution’
Have more questions on how Shufti can help you? Share your concerns with our team and get a solution as per your business needs!