Top 5 Cybersecurity Trends to Look Out for in 2022

With 2022 just around the corner, new developments in cybersecurity are already beginning to take shape. Considering the 600% upshot in cybercrime amid the pandemic, the urgency for cybersecurity is further augmented. Given the dependency of modern businesses on digital solutions, it is safe to say that the corporate world may undergo monumental upgrades. New regulations for cybersecurity updates are inevitable to combat the increasing number of cyberattacks.
According to reports, cyberattacks contributed to losses of up to $6 trillion in 2021 alone, which is the single largest economic upset in history. By 2025, cybercrimes are expected to cost the world $10.5 trillion. As governments work towards elevating their cybersecurity posture, the key criteria here is the extent to which businesses can adopt the best practices.
1. Phishing Attacks to Remain a Major Issue
Although Canada is far ahead as compared to the rest of the world in mitigating cyber threats, 78% of Canadian organizations still faced a cyberattack in 2020. This indicates the catastrophic effect of cyberattacks with numbers rising in the negative direction. The most common type of cyberattacks took the form of ransomware and phishing. Looking at the trends of 2021, it’s clear that hackers and malware are becoming advanced with improvements in technology.
A rise in phishing attacks was observed this year, as fake COVID-19 vaccination drives led to e-commerce fraud where credit card information was collected by bogus online shops. The number of overall data breaches recorded by September 2021 was 1,291, which had already exceeded the total of 2020. In order to avoid becoming the victims of phishing sites and emails, businesses must elevate their identity verification measures and conduct employee training. For this reason, the demand for cybersecurity professionals will further increase in 2022, as companies will need their guidance to stay ahead of their competition.
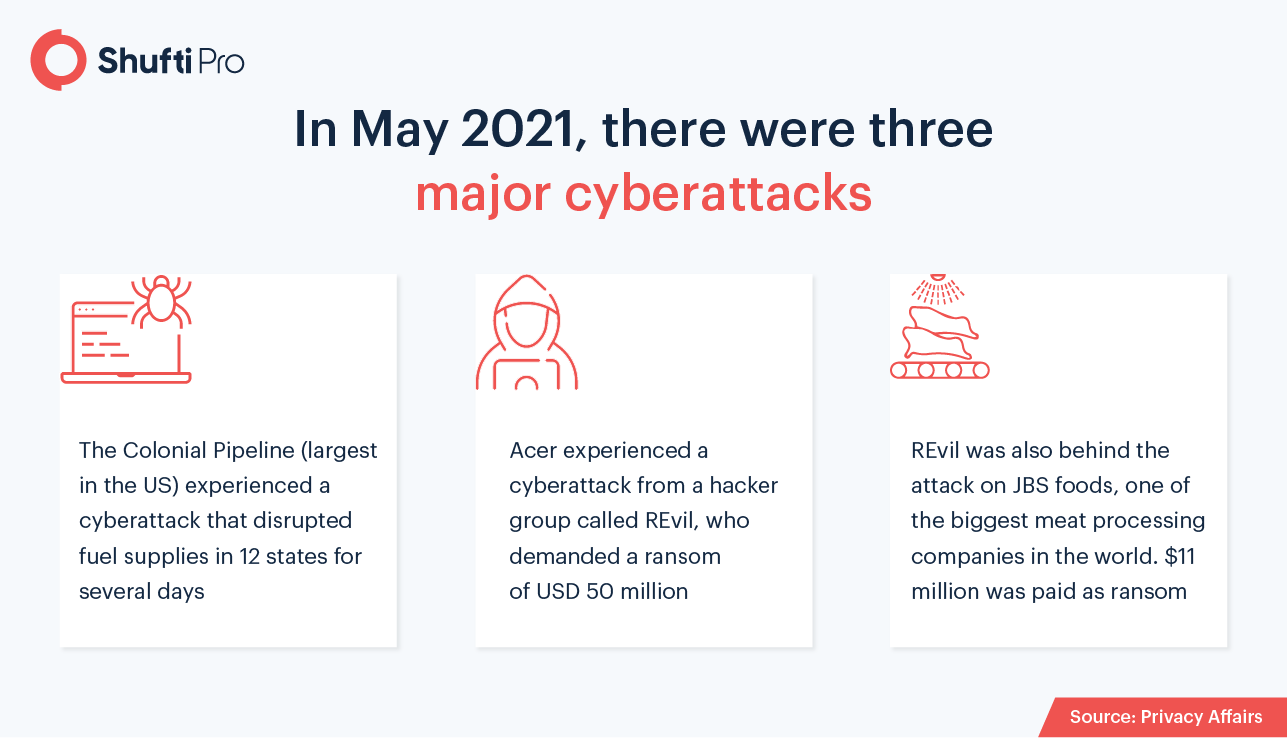
2. Internal Threats & Cloud Attacks
Trojan horses are rightfully named as they can effectively wipe out a large amount of data. However, the origins of all cyberattacks are not malware, as statistics show that 15 to 25 percent of data breaches were due to the involvement of corrupt employees or business partners. In the coming times, virtual workplaces will further gain prominence and companies will need to be more careful at the same time. Therefore, it is becoming essential for businesses to control access levels for new employees, freelancers, and third-party suppliers.
As the pandemic forced businesses to improvise and follow remote working procedures, a lot of data sharing, communication, and other activities are being conducted through cloud services. Although this enables businesses to stay connected and generate revenue regardless of the location of employees, it has a few drawbacks in terms of cybersecurity. In 2022, cloud services are expected to be used by an increasing number of companies as they strive to adopt virtual or hybrid solutions even after the pandemic’s restrictions.
On one hand, cloud services allow scalability and flexibility in business processes. On the other hand, they create risks of cyber attacks and data breaches. 2020 saw more data breaches through cloud systems as compared to on-premises storage. This means that banks and financial institutions will have to take necessary countermeasures to secure their cloud systems and confidential information. In order to avoid data breaches, businesses must not leave out any gaps in their security systems and raise awareness among their staff to follow the best practices for data privacy.
3. Artificial Intelligence as a Saviour
Considering the cybersecurity trends for 2022, artificial intelligence has become increasingly necessary to establish a strong frontier against cyberattacks. In 2020, 47.3% of companies had a medium to high-security automation level, which was a significant increase as compared to 39% in 2019. The basic concept behind AI comes into play here, as experts suggest that the higher the level of automation, the more secure a business system will be.
An officer in charge of security can make errors like falling prey to a phishing email, but today’s advanced AI systems can easily detect such attacks. Automation of security systems also reduces the risk of internal threats as a lesser number of humans will be able to leak confidential information. Moreover, AI allows much more accuracy in analyzing risk as compared to humans.
4. Securing the Supply Chains
A number of cybersecurity concerns are raised due to loopholes and insufficient security protocols in supply chains. These ultimately give way to numerous false allegations on vendors and third parties. However, the industry has responded to this with a positive approach to improve vendor management as a cybersecurity measure. This is being considered as one of the key focus areas for 2022, starting from the disclosure of business information. Despite cloud service providers claiming that a centralized storage system is far more secure, the coming year will prove that this is not true.
As seen from reports of cyberattacks involving cloud storage, the current business operations actually turn out to be the opposite of secure. Businesses will need to incorporate KYB (Know Your Business) measures to verify their partners, third-party vendors, and suppliers. Unless companies put it all on the table at the start of the collaboration, they are welcoming cyber attackers to breach their data. For example, such exposure was created by Amazon in a reported event where AWS appliance installations were hacked. Therefore, it’s clear that 2022 will see more cyber threats unless work is done to improve security.
5. Identity-based Security Protocols
As the techniques of fraudsters continue to evolve, personal information on digital platforms is becoming increasingly vulnerable to cybercrime. To overcome the theft of financial information, digital banking platforms will need to incorporate identity verification measures. With the new methods of hybrid work and the transfer of major business data to cloud applications, the importance of identity verification is further justified. Although the concept in itself is nothing new, the urgency for cybersecurity will force its adoption in companies.
As most cyberattacks begin with a stolen identity, managing the access protocols will be a key aspect in maintaining a business reputation. Misuse of credentials and data breaches will mean the end of small businesses if the modern cyber attackers capitalize on the loopholes in their system. Business directories and employee registries must be configured with security barriers like 2-factor authentication and transaction monitoring systems should be incorporated to detect suspicious activities.
Key Takeaways
Sooner or later, banks, financial institutions, and businesses will need robust identity verification solutions to eliminate the root cause of cyberattacks. Onboarding of legitimate individuals can only be ensured when the company knows who they are every time they try to access the system. Based on the trends, data breaches and ransomware are not going to be eliminated any time soon.
Want to learn more about on-premises solutions for your business?












![40 Surprising Facts and Statistics About Money Laundering [2021 Update] 40 Surprising Facts and Statistics About Money Laundering [2021 Update]](https://shuftipro.com/wp-content/uploads/blog.jpeg)





















![The US Corporate Transparency Act – What’s New? [December 2022] The US Corporate Transparency Act – What’s New? [December 2022]](https://shuftipro.com/wp-content/uploads/us-coporate-transparency.jpg)







































