Understanding Facial Identification: Face Verification vs. Face Recognition

Many terms in the biometrics field are used interchangeably, particularly regarding facial verification and face recognition. Although both terms are sometimes used interchangeably, the underlying technologies are different and are intended to assist with various use cases. Thus, it’s crucial to comprehend these differences since they impact how the terms should be used and implemented.
Face Verification vs Face Recognition
Whilst both use biometric verification and are used to validate individuals, they differ in many ways.
Face Verification: A type of biometric authentication that uses an individual’s biological characteristics to validate that the user is who they claim to be.
Face Recognition: A biometric software app that identifies or verifies a person by matching and analysing patterns based on the individual’s facial contours.

Understanding the Process of Face Verification
Face verification is 1:1 compared to facial recognition, which uses a 1:n comparison against a database of recognised faces. The user secures their digital account access by authenticating their face as a credential. The user only needs to snap a selfie to verify, then a biometric template is generated and compared with the stored template. A suitable match completes the safe authentication procedure in the background.
Here are the basic steps of the face verification online process:
- The user must provide a picture of a government-issued ID card, such as a passport or driver’s licence.
- Identity verification enables the user to capture a selfie, which is subsequently contrasted to the image on the ID document, to make sure the ID document belongs to the person who submitted it. This step deters scammers because they typically don’t want to utilise their photograph and share it with the organisation they’re trying to defraud.
- Liveness detection is a part of the selfie-taking process that ensures the user is there for the interaction. This is done to combat criminals increasingly employing spoofing attacks by using a photo or video of an authorised person as their own to obtain that person’s credentials or access rights.
- A biometric template is made during the liveness detection and selfie-taking process. Similar to a face signature, this template is specific to the person and is retained by the client for other authentication events.
- Users are given login information When they pass the company’s scrutiny.
- The user is prompted to snap another selfie when entering their account or completing a high-risk transaction. A match or no match decision can be made seconds after comparing a new biometrics template with the one established during the original enrolment.
- The new biometric template is matched to all subsequent face maps besides the original face map to increase the reliability and accuracy of verification.
Benefits of Face Verification Service
- Better Identity Assurance: Businesses can have a higher level of certainty that an individual is who they say they are by requesting a government-issued ID and comparing it to a selfie.
- Easier for Users: Facial authentication is now more widely used and accepted due to the popularity of Apple’s Face ID. With its simplicity, speed, and omnichannel compatibility, biometric-based authentication enhances the user experience and lowers friction when enriched with verified anti-spoofing capabilities.
- More Robust Fraud Detection: How effectively does the solution catch malware, bots, and criminals? To minimise fraud loss, businesses must be able to assess risk while making better application management decisions properly. Additionally, companies must improve their ability to recognise online businesses’ most significant threats, such as identity theft, synthetic fraud, and account takeover.
- Need for Speed: Users are becoming increasingly picky about their authentication methods, expecting them to be quick, easy, and dependable. With an extremely high degree of identity assurance, modern face verification can swiftly compare a new selfie to a photo already taken.
- Cross-Platform Portability: Cross-platform biometric verification is now possible, as biometric templates are created on any camera device. Users can sign up using a computer’s webcam and verify later from a smartphone. As a result, everything from opening a car door to resetting a safe password to logging into your bank account can now be done using face authentication.
Understanding the Process of Face Recognition
Facial recognition validates a user’s face using technology. Advanced face recognition software uses biometrics to map facial traits from a video or photo. The details are then cross-checked with a database of recognised faces to see if there is a match.
Here is how the face recognition process works:
- A facial image is extracted from a photograph or video.
- Face recognition software analyses photos of human faces based on details, like the distance between your eyes and the gap between your forehead and chin.
- The software develops a facial signature by analysing the landmarks that differentiate one face from another.
- A database of recognised faces is used for comparing the facial signature. This is called a 1:n comparison, where n is the database’s total number of facial signatures.
- A match or no match is determined based on the faceprint matches to the image in the database.
Face recognition software is not error-free. Several variables, including camera quality, database size, and the subject’s gender and race, can substantially impact the precision of face recognition solutions.
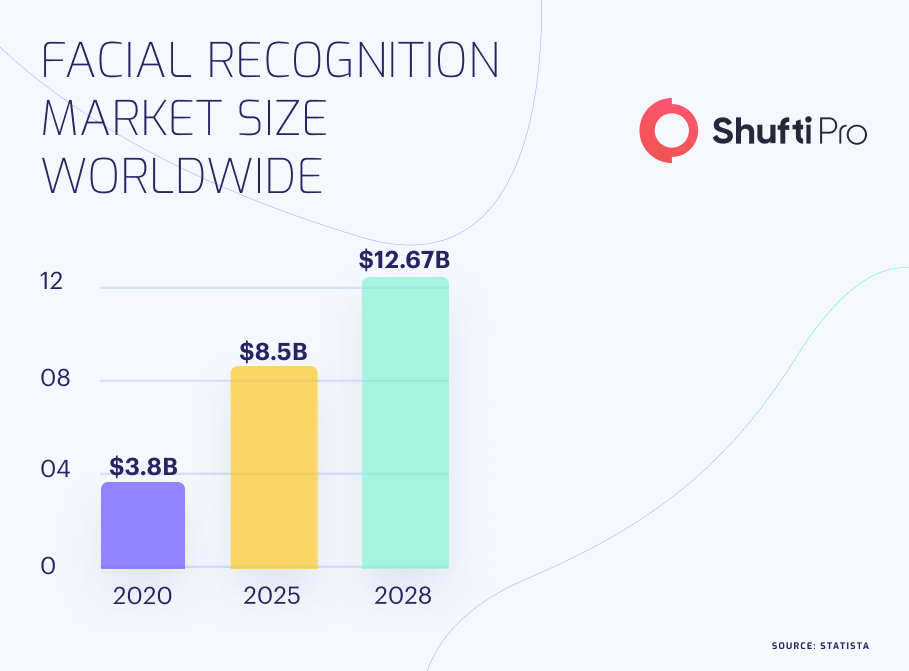
Top Use Cases of Face Recognition
- Retail: Facial recognition is used to detect known shoplifters, organised retail criminals, or those with a track record of fraud visiting retail outlets.
- Law Enforcement: Law enforcement organisations, including local police departments, are already using facial recognition to quickly identify people in the field while maintaining a safe distance. This data can give them contextual information indicating that they should exercise caution.
- Advertising: Facial recognition enables precise advertising by estimating people’s gender and age.
- School Safety: Facial recognition systems identify when problematic parents, expelled students, drug dealers, or other potential threats to school safety approach the premises.
- Missing Persons: Victims of human trafficking victims and missing children are found using facial recognition technology. Law enforcement will be notified if a missing person is identified by face recognition anywhere, as long as they have been entered into a database.
- Social Media: Facebook automatically recognises when one of its users appears in a photo using face recognition technology. This makes it easy for people to locate photographs of themselves and suggests situations in which specific people should be mentioned in pictures.
- Casinos: When a known cheater or someone on a voluntary exclusion list enters a casino, facial recognition technology lets casinos identify them immediately. The casinos may be heavily fined if these players are caught gaming.
Why Choose Face Verification Over Face Recognition?
Face verification benefits clients and businesses alike. Facial authentication, in contrast to facial recognition technologies which frequently operate without the user’s knowledge, is permission-based, offering a user high levels of security whilst enabling seamless access to their accounts. The appealing aspect of facial verification is that users only need to snap a new selfie to log into their preferred app; they are spared from completing the complete identity verification process.
Businesses can employ facial verification solutions to ensure that only authorised users are setting up and accessing their accounts. Another benefit of facial verification is that companies can use the same biometric information—such as a validated 3D face map—collected during enrolment and reuse it for subsequent authentication occasions. This implies that both ongoing user verification and identity proofing can be handled by the same solution.
Naturally, no technology is entirely risk-free. Due to the volume of data involved in facial recognition, handling and storing challenges may arise. Despite significant advancements, face recognition is still imperfect when faces are seen from different camera angles or when there are barriers like hats. Additionally, there have been privacy-related controversies, especially in the retail and governmental sectors. This is why facial recognition should be combined with multi-factor approaches (such as facial authentication) to improve user access rather than being utilised for identity proofing.
How Can Shufti Help?
Shufti’s face verification solution uses deep learning algorithms to accurately identify and validate human faces. Shufti is a globally trusted biometric verification solution provider incorporating advanced anti-spoofing measures to combat fraud.
Here’s what makes Shufti’s face verification services a strong barrier against impersonation attacks and stolen identities:
- Verify clients within seconds
- Guard against identity theft
- Detect spoof attacks
- Enhanced user experience
Still confused about how a face verification solution keeps scammers at bay?