ID Document Fraud | Is Your Business Prepared to Fight the War Against Fraud in 2024?

In today’s data-driven, digitized world, various business processes have been automated to provide unmatched ease, speed and reliability. This digital transformation benefits businesses and individuals, as well as people with malicious intentions who employ sophisticated ways to manipulate banks or other institutions with forged documents. Identity document theft and forgery have emerged as a significant challenge for businesses – costing billions of dollars each year in losses or non-compliance fines.
Counterfeit documents have long been a persistent and formidable issue plaguing businesses, individuals, and governments, from securing loans beyond eligibility to getting illegal residence permits. Such documents are used for multiple fraudulent purposes. Thus, verifying the authenticity of ID documents has become increasingly complex and essential in today’s digital world.
Document Fraud | Prohibition and the Rise of Counterfeit Identification
Document fraud is a malicious act of developing, modifying, or counterfeiting a genuine document intending to manipulate verification checks for illicit gains. The offenses and fines can differ depending on the situation and intentions behind carrying out this crime. Forging government-issued documents such as identity cards, driver’s licenses, passports, or permanent residency papers is considered a significant offense in almost all jurisdictions and even more worse in cases developed with the intent of selling them to illegitimate individuals. The roots of ID document forgery can be traced back to the 1920s – the prohibition era, when the government of the United States imposed a ban on alcohol consumption nationwide. With the demand for such drinks remaining high despite the governmental restrictions, citizens seek access to hidden sellers or secret gatherings. This situation ultimately led to an increase in the need for fake documents. During those times, underground organized crime networks and skilled identity forgers emerged in large numbers to meet the increasing demand. They mastered the art of creating counterfeit copies that mimicked legitimate ID documents, providing people with the means to get access to restricted activities.
Who Commits Document Fraud?
Anything from altering personal information to forged numbers to full-scale document or identity forgery is qualified as fraud – which means that multiple individuals can use such documents in various scenarios, not only restricted to criminals. Determining who uses fraudulent documents and the intention behind the fraud is the first and key step in fraud risk management and mitigation.
Here is a breakdown of two major document fraud categories:
First-Party Fraud
In document fraud, individuals use their identity documents but alter some details or add misleading information. Essentially, criminals commit scams in their name and for personal gains – aiming to exploit restrictions or avail services inaccessible to them. One such example is inflating their income on account statements to qualify for significant valued loans. The blend of legitimate and fake information that makes first-party fraud believable makes it hard for compliance officers to spot the sign of forging.
Third-Party Fraud
In this kind of fraud, criminals assume a wholly different identity, typically by stealing victims’ ID documents or personal information mixing real and fake information to make a new, fictitious identity. As this can affect both victims and businesses, third-party fraud is a more adverse type. However, it involves unsuspecting people or completely illegal identities that have never existed in the real world. Generally speaking, third-party crimes are sophisticated and are hard to detect using traditional fraud detection and prevention systems
Types of Document Fraud
Like the categories of people who commit document fraud, multiple types of fake documents have been intentionally created to commit crimes. Put another way, criminals use different ways to make and use forged documents, each requiring a unique set of fraud detection checks for accurate analysis. Here are some common types of document fraud your business might encounter or will experience in the future:
Document Forgery
Document forgery involves imitating real identity documents entirely from scratch to make a new, fake document. However, making a believable forged document can be hard, but looking into the types of documents produced worldwide, document forgery can easily manipulate traditional document verification systems and compliance officers.
Document Alteration
This involves altering or manipulating legitimate identity documents by minor changes to government-generated documents. This is as simple as changing a name, address, date of birth, or a few numbers through Photoshop or image processing software. This form of document fraud is hard to detect by the naked eye, as it requires rigid document checks powered by OCR technology.
Synthetic Identities
In synthetic identity fraud, criminals usually mix real and bogus information to develop a new identity. Most commonly, this combines ID theft, document alteration, and document forgery – where certain information is stolen, such as name and credit card number, while the other information is self-created by the criminals, like forged bank statements and proof of address.
Template Fraud
In today’s digitized world, where everything is easily available online, it’s not hard to find editable legal document templates. However, these can be in any format, free or paid, and available in multiple ways. Technically, this is a form of document alteration. Templates are so prevalent and impactful that they can easily manipulate businesses and are very hard to detect without proper document verification checks.
Serial Fraud
This form of fraud is yet a new but rapidly growing type of document fraud that relies on combining one or more of the above-mentioned document fraud types. Usually, fraudsters identify vulnerabilities in business control systems and then, using automation technologies, exploit that loophole on an industrial scale. For instance, if criminals succeed in manipulating security checks using a winning combination of ID cards and supporting documents, then they create hundreds of copies and variants to open dozens of bank accounts programmatically – all under the control of one fraudster.
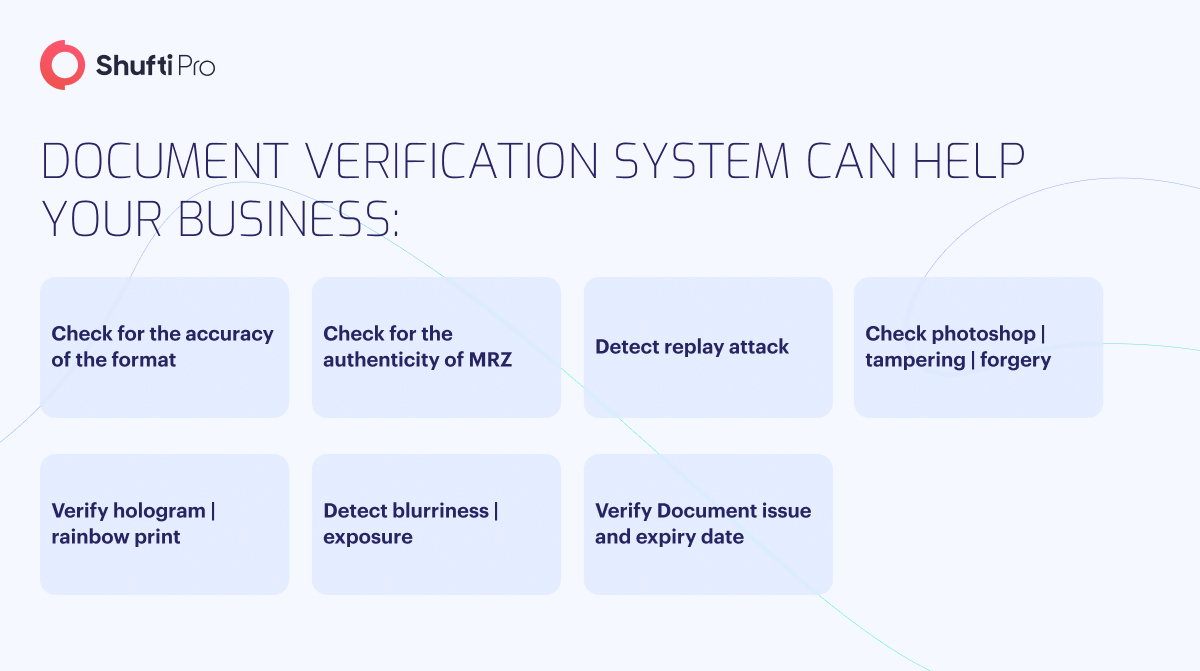
Document Fraud Detection and Prevention
The world of fraud is multi-layered and complex and has a lot of variables – who is committing the crimes, what techniques are used to create fake documents, which type of document is used, and even the business type a criminal is trying to manipulate. However, there is an array of document fraud detection and prevention methods that help businesses fight the surging crime rate. Used with the blend of automation technologies, document verification checks effectively stop fraudsters – or at least make business verification systems less appealing to criminals.
Fraud Risk Assessment
The first and foremost step in effective fraud risk management is assessing the fraud risk. Identifying potential threats your business is exposed to, in-house verification system shortcomings, risk tolerance, and potential risk assessment solutions that can streamline your company’s operations. These parameters must be clearly defined before developing or implementing a fraud risk detection framework.
KYC Onboarding Process
Knowing your customer backed by document verification helps businesses define strengths and weaknesses. Optical character recognition, intelligent document processors, and identity verification solutions are the key aspects that can enhance the effectiveness of document checks as well as define which document types and
Document Verification Systems
With the surge in identity fraud, fintech companies have emerged with an array of document verification tools and solutions powered by artificial intelligence and machine learning algorithms. These sets of fraud prevention checks analyze metadata, templates, structuring, and integrity of signed documents. State-of-the-art systems are pre-loaded with government-issued ID document templates, which are used to compare against incoming ones. The latest edition in today’s document verification solutions is self-learning capabilities that can go beyond pre-trained classification approaches to identify signs of document fraud.
Document Fraud – An Alarming Situation for Today’s Businesses
Depending on the jurisdictions’ law and order, document fraud penalties and fines vary. Some of the legislations associated to document forgery across Europe is quoted below:
- In the United Kingdom (UK), the Forgery and Counterfeiting Act of 1981 defines offenses related to document forgery, altering or creating fake identities, or using illicit instruments to bypass security checks. According to Article 1, the offense of forgery is defined as: “a person is guilty of forgery if he makes a false instrument, with the intention that he or another shall use it to induce somebody to accept it as genuine, and by reason of so accepting it to do or not to do some act to his own or any other person’s prejudice.” However, the severity of fines and penalties vary case-wise but can make an individual involved in such activities face a sentence of up to 10 years.
- In Germany, Section 267 defines forgery offenses and states, “Whosoever for the purpose of deception in legal commerce produces a counterfeit document, falsifies a genuine document or uses a counterfeit or a falsified document shall be liable to imprisonment not exceeding five years or a fine.” According to this section, even an attempt to forge a document is punishable. The German Criminal Code imposes sentences from six months to 10 years of imprisonment – depending on the offense type and its outcomes.
Document Fraud Detection with Shufti
Document fraud is on the rise and shows no sign of slowing down. The same technologies behind digitizing business operations are behind the surge in such activities. Fraudsters are discovering and learning new ways of manipulating information to exploit identity verification checks. To overcome the risk of exposure to such crimes, businesses need to integrate fool-proof document verification solutions.
Shufti, a leading identity verification service and solution, offers document authentication services across 240+ countries and territories, aiming to assist businesses in every region of the world in the fight against evolving fraudsters. The company uses intelligent, robust, and streamlined processes that instantly identify and detect anomalies and signs of forgery. Using in-house, white-labeled OCR technology, our solutions can fast-track data extraction and temperate generation – making it easier for businesses to scale operations, fight fraud, and reduce processing time.
With Shufti, businesses can:
- Seamless text extraction through intelligent OCR
- Arm your business against identity fraud
- Employ AI to discern tampered and counterfeit identification documents
- Analyze metadata to uncover inconsistencies and signs of alteration

 Explore Now
Explore Now













